CPRA vs. CCPA: What’s the Difference? 6 Key Changes to Understand
Less than one year after the CCPA took effect, California passed another consumer privacy law: the CPRA. Here are six changes to help you understand the differences between CPRA vs. CCPA.
In 2018, the state of California passed the California Consumer Privacy Act (CCPA), a landmark piece of legislation that secured several privacy rights for California consumers.
Just over a year later, in November 2020, Californians voted to approve Proposition 24, creating the California Privacy Rights Act (CPRA) of 2020. The CPRA can be thought of as a more comprehensive version of the CCPA, updating, modifying, and extending certain rules and stipulations to increase the rights of California consumers.
Wondering what the differences are between CPRA and CCPA?
We have highlighted six key differences that we’ll explore in this post. Read on to find out the impact the CPRA may have on your organization.
Difference #1: Updated Criteria for Qualifying as a Business
Under the CPRA, an organization can classify as a business if they are a legal entity that is operated for profit, involves the collection of California consumers’ personal information (PI), determines the purposes and means of processing PI, and satisfies one or more of the following conditions:
(A) Has an annual gross revenue of over $25 million in the preceding calendar year
(B) Alone, or in combination, annually buys, sells, or shares the personal information of 100,000 or more consumers or households
(C) Derives 50% or more of its annual revenue from selling or sharing consumers’ personal information
Most notably, the CPRA doubles the CCPA’s threshold criteria of 50,000 California consumers or households within condition B. It also expands the CCPA’s definition in criteria C, including annual revenue derived from sharing PI in addition to selling it.
Potential Impact
This change in criteria means that some small to midsize businesses that have to comply with the CCPA may not fall under the scope of the CPRA. Because the CPRA increases the number of consumers or households in criteria A (from 50,000 in the CCPA to 100,000 in the CPRA), the new law may actually reduce the number of businesses that qualify under that threshold. However, the inclusion of “sharing” related to deriving 50% or more of annual revenue from selling or sharing consumers’ personal information in criteria C may potentially increase the number of organizations that would qualify as a business under that threshold.
Difference #2: A New Category of Highly Protected Data
The CPRA introduces a new category of protected data: sensitive personal information (SPI). This concept is very similar to Article 9 of the General Data Protection Regulation (GDPR)—”Processing of special categories of personal data”—which calls for a greater level of data protection due to the sensitivity of the personal information. The addition of this new data category may require businesses to implement additional technical and operational controls to process such data and to limit the use and disclosure of SPI according to consumers’ rights under the CPRA.
The CPRA imposes specific requirements and restrictions on SPI, giving users expanded rights to control businesses’ use of their personal information. These new requirements include:
- Updated disclosure requirements
- Purpose limitation requirements
- Opt-out requirements for use and disclosure
- Opt-in consent requirements after a previously-selected Opt-out
Potential Impact
The introduction of SPI means that businesses, as defined by the CPRA above, must be especially vigilant to protect this class of data and respond accordingly when a consumer decides to opt out. If a business intends to process consumers’ SPI as defined within Section 1798.121 and 1798.135 of the CPRA, then there are additional requirements that must be implemented. For example, businesses that store SPI must include a clear and conspicuous link on their websites titled “Limit the Use of My Sensitive Personal Information” that enables consumers to restrict the processing of their SPI.
Difference #3: New and Expanded Consumer Privacy Rights
There are five consumer privacy rights that are present in the CCPA that have been modified under the CPRA. These rights are:
- Right to Opt-Out of Third-Party Sales and Sharing: The CCPA allows consumers to opt-out of businesses selling their data. The CPRA expands this right to include the sharing of personal information, in addition to selling. The CPRA defines sharing as “disclosing, disseminating, making available, transferring, … a consumer’s personal information by the business to a third party for cross-context behavioral advertising, whether or not for monetary or other valuable consideration …”
- Right to Know: The CCPA requires that businesses respond to consumer requests to know personal information that was collected within the prior 12 months. The CPRA extends this timeline, enabling consumers to potentially request personal information collected beyond the prior 12-month window under certain circumstances.
- Right to Delete: Through the CCPA, California consumers can request that a business delete their personal information if it is no longer needed to fulfill one of the purposes listed in Cal. Civ. Code Sec. 1798.105 (e.g., security needs, debugging). The CPRA will also require businesses to send the request to delete to third parties that have bought or received the consumer’s personal information so that all parties are aware that it must be deleted, subject to some exceptions.
- Right to Data Portability: The CCPA includes a “right to know”, which means that consumers have the right to receive a copy of their personal information by mail or electronically. Now, under the CPRA, a consumer can request that a business transfer specific personal information to another entity “to the extent technically feasible, in a structured, commonly used, machine-readable format.”
- Opt-In Rights for Minors: The use of minors’ data is a general concern within the law, and the CCPA requires that businesses obtain opt-in consent to sell the personal information of a California consumer under 16 years of age. The CPRA goes one step further, mandating that businesses wait 12 months before asking a minor consumer for consent in selling or sharing their personal information after the minor has declined. It also states that the opt-in right must explicitly include the sharing of data for cross-context behavioral advertising.
In addition to expanding several of the CCPA’s consumer privacy rights, the CPRA also introduces four brand–new consumer privacy rights that are not present in the CCPA:
- Right to Correct Information: A consumer has the right to request that a business correct any inaccurate personal information.
- Right to Limit Use and Disclosure of Sensitive PI: A consumer has the right to limit the use and disclosure of their SPI to that “use which is necessary to perform the services or provide the goods reasonably expected by an average consumer who requests such goods and services.”
- Right to Access Information About Automated Decision Making: A consumer has the right to request “meaningful information about the logic involved in those decision-making processes, as well as a description of the likely outcome of the process with respect to the consumer.”
- Right to Opt-Out of Automated Decision-Making Technology: A consumer has the right to opt-out of being subject to automated decision-making processes, including profiling.
Potential Impact
Businesses must ensure that they are prepared to comply with the CPRA’s new and expanded consumer privacy rights. They will need to develop strong processes and controls to ensure they are both capable of and prepared to respond swiftly to consumer requests. Many businesses may need to make significant changes to their existing security and privacy-related controls, hire additional personnel, or contract third-party services to help them prepare for CPRA compliance.
Difference #4: Adoption of Select GDPR Principles
The GDPR has served as a template for many new privacy regulations, including the CPRA. For example, the GDPR enforces the concepts of data minimization, purpose limitation, and storage limitation. These principles are not included in the CCPA, but they are now codified as part of the CPRA:
- Data minimization: The requirement that “a business’s collection, use, retention, and sharing of a consumer’s personal information shall be reasonably necessary and proportionate to achieve the purposes for which the personal information was collected or processed.”
- Purpose limitation: This requires that businesses “only collect consumer’s personal information for specific, explicit, and legitimate disclosed purposes, and should not further collect, use, or disclose consumer’s personal information for reasons incompatible with those purposes.”
- Storage limitation: This requirement addresses “the length of time the business intends to retain each category of personal information, including sensitive personal information, or if that is not possible, the criteria used to determine such period, provided that a business shall not retain a consumer’s personal information or sensitive personal information for each disclosed purpose for which the personal information was collected for longer than is reasonably necessary for that disclosed purpose.”
Potential Impact
By codifying these principles explicitly in the CPRA, California has authorized the state regulator to enforce, and potentially penalize, a business’s failure to 1) reasonably limit the collection of personal information to what is necessary for the purpose for which it was collected, and 2) limit the retention of personal information to the least amount of time necessary to fulfill the purpose for which it was collected.
Difference #5: Expansion of Legally Actionable Data in a Breach
Data breaches are a serious concern for businesses of all sizes. When a breach occurs, hackers can extract sensitive information, which puts both the business and consumers at risk. In the event a data breach occurs, the CCPA gives consumers the private right to take legal action if their nonencrypted or nonredacted personal information becomes exposed because a business failed to implement reasonable security procedures and practices appropriate to the nature of the information processed. While the CPRA does not explicitly alter this right, it does add consumer login credentials to the list of personal information categories that may be actionable under the law.
Potential Impact
Many organizations suffer as a result of a data breach, as hackers gain access to personal information and exfiltrate that data from the boundary of the system. The CPRA’s expansion of scope to include login credentials as a legally actionable personal information security breach may be a response to the wave of authentication hacks affecting consumers in recent years. In addition to more advanced layers of data encryption, many businesses may want to require multi-factor authentication as an additional security layer.
Difference #6: Creation of a New Privacy Enforcement Authority
The CCPA was originally enforced by the California Office of the Attorney General (OAG). The CPRA shifts this authority by establishing the California Privacy Protection Agency (CPPA) and granting it investigative, enforcement, and rulemaking powers.
Potential Impact
The CPPA’s outlined role in enforcing the CPRA is a notable change from the CCPA. The codification in Section 1798.199.10 provides instruction regarding the CPPA including, “[t]he agency shall be governed by a five-member board, including the chairperson. The chairperson and one member of the board shall be appointed by the Governor. The Attorney General, Senate Rules Committee, and Speaker of the Assembly shall each appoint one member. These appointments should be made from among Californians with expertise in the areas of privacy, technology, and consumer rights.” It remains to be seen how this new agency will wield its authority, but we expect that we will see an increase in the number of investigations and enforcement actions taken by the CPPA.
Start Preparing for CPRA Compliance Today
Although all aspects of the CPRA do not take full effect until January 1, 2023, organizations that do business in California should start laying the groundwork for CPRA compliance throughout the course of 2021 and 2022. If you currently have measures for CCPA in place, now is the time to perform a gap assessment based on the information available regarding the CPRA.
To prepare for the CPRA, organizations can take proactive steps such as:
- Conducting a data-mapping exercise to identify and document what PI will fall under the scope of the CPRA.
- Updating privacy notices to reflect the new and modified consumer privacy rights and related disclosure obligations.
- Reviewing downstream data-sharing practices and informing third parties that they may be required to comply with these new regulations.
By understanding the full scope of the CPRA and designing a thoughtful roadmap toward full compliance, companies can avoid the potential impacts of non-compliance once the CPRA is fully operative.
How to Feature Your Cybersecurity Assessment on Your Website
A cybersecurity assessment like a SOC 2 or an ISO 27001 certification is a statement about your commitment to protecting information. This post looks at examples of how leading companies give that report a permanent home on their websites and provides best practices so you can do the same.
A cybersecurity assessment like a SOC 2 examination or an ISO 27001 certification is much more than just a document – it’s a statement. Specifically, these reports communicate to your customers, prospects, and business partners that you take cybersecurity seriously, and you can be trusted with their sensitive information. So, it’s a great idea – in fact, a competitive advantage – to spread the word.
In my last post, I talked about that first step – announcing your assessment with a press release. But your report lives beyond that initial announcement, which means you need to give that report (or some form of it) a permanent home on your website where it can be accessed any time it’s needed. We’ll look at some real-world examples of how companies do just that.
Isn’t my compliance report a “need-to-know” document?
You might say, “My compliance report should only be given to a customer on a need-to-know basis after an NDA is signed. It’s too much information to put on a website.”
There’s a lot of truth to that – in a literal sense. Some documents are meant to be public (like a SOC 3 report, for example), but in general, compliance reports are reserved for specific situations where a non-disclosure agreement is in place. You may even find explicit instructions on what the report should be used for, such as the Restricted Use section of a SOC 2 report.
However, none of that precludes you from talking about the fact that you have completed cybersecurity assessments and discussing the security principles and policies behind them. Today’s companies, surrounded by a barrage of reports about breaches and data leaks, want to trust the companies they transact with. Your reports are the meaningful, widely accepted evidence that backs up your claims.
Let’s look at some examples
I think one of the best ways of understanding how you can feature your assessments on your website is to look at examples of some great companies who have done an excellent job at this. Let’s check out four.
Example 1: Snowflake
Snowflake is a fast-growing data platform company that made news in September 2020 as the largest-ever software IPO (SNOW). As a company that provides customers with a cloud-based data warehouse, you can imagine how important it is for Snowflake to demonstrate trust to all its business partners.


Snowflake has created a Security and Trust Center, with several different options for learning about various aspects of Snowflake’s approach to security throughout its platform, including a dedicated page listing its security and compliance reports. From here, a short description explains each report, with instructions on how to obtain them – specifically, acquiring an NDA and filling out a contact form. Note the following:
- Snowflake displays all its certification badges proudly across the main trust center page
- Includes simple, clear explanations of each of the certifications they go through
- Provides a straightforward process for requesting a report, conditioned on meeting specific criteria
Example 2: Salesforce
Salesforce, the original SaaS company, is the 800-pound gorilla when it comes to anything related to customer relationships. Those relationships are sacred, so obviously Salesforce needs to demonstrate to their customers how seriously they take security.

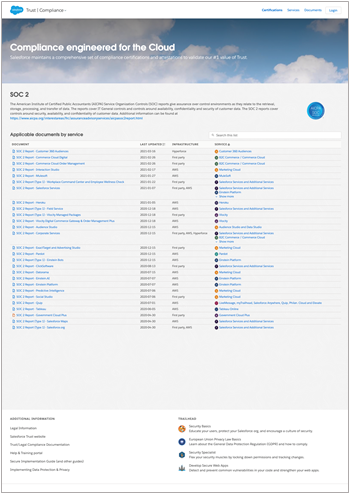
Salesforce has a much larger library of certification reports given the breadth of their business and has taken a more direct approach to presenting their certifications. Looking at their site, one might assume they expect visitors to know what they are looking for, so all the certifications are laid out in an easy-to-navigate grid form, with little additional context, so the user can drill down and get exactly what they need. Some observations:
- The Salesforce compliance center sits on its own domain: compliance.salesforce.com
- Each report is broken down by product, date, and infrastructure
- Access to most reports is protected with your Salesforce credentials
Example 3: Asana
Asana is a popular project management application – in fact, my marketing team here at A-LIGN depends on Asana for almost all our projects! Since Asana’s customers, like us, rely on the tool every day to coordinate teams and keep work moving, we need to know that our information is protected.
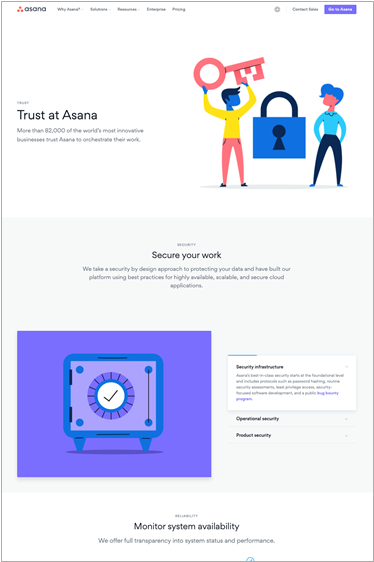
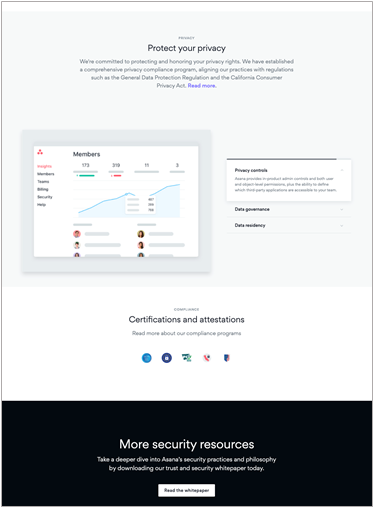
Asana’s approach is to communicate a message of trust to their customers. Personally, I’m a big fan of customer-focused messaging, and I appreciate how Asana has laid out their story. They place their certification badges at the bottom of their page, providing links to publicly accessible reports. In particular, they provide a link to their SOC 3 report, which as the AICPA states, is “designed to meet the needs of users who need assurance about the controls at a service organization relevant to security, availability, processing integrity, confidentiality, or privacy, but do not have the need for or the knowledge necessary to make effective use of a SOC 2 report.” Some things to notice:
- Everything, including the URL asana.com/trust, speaks directly to their customer commitment
- They use clear language and graphics to explain their entire approach to security
- They focus on publicly available resources to instill confidence in their security program
Example 4: Freshworks
Finally, let’s check out Freshworks. Freshworks is an engagement platform for employees and customers, so like some of our other examples, it’s pretty clear why protecting information related to those groups is so important.
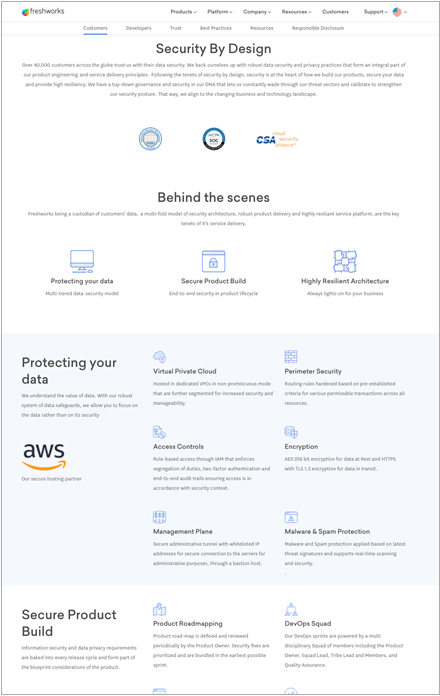
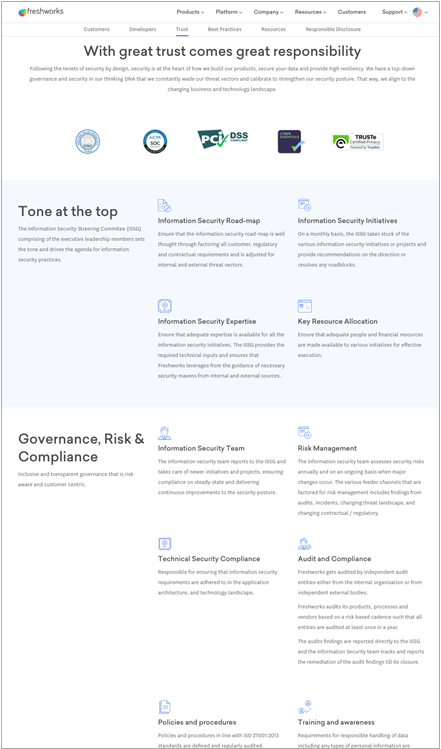
Freshworks has a very advanced Security Center on their website, with multiple pages for different audiences (customers and developers), a trust center, best practices, resources, and even an area for responsible disclosure. What I like most about their site is how thought-through it is, with so much information and such a high degree of transparency. In website terminology, we call this a microsite – an entire area devoted to one concept, with a defined purpose and its own navigation and structure. Here are some things worth pointing out:
- The microsite contains a rich FAQ area with answers to common questions
- It includes a breakdown of many of their security processes and how they impact different audiences
- They include a bug bounty hall of fame to promote responsible disclosure
Putting it all together
Hopefully these pages gave you some good ideas for how to use your compliance reports on your website. My biggest takeaways:
- Share your approach to security and relate it to your customers and business partners
- To whatever extent you are comfortable, be transparent with some of your core security and compliance processes
- Include some of the best practices you follow (encryption, penetration testing, etc.)
- Guide your visitors through the process of requesting a report
- Feature your auditor, as their credibility will translate to your customers
Compliance is all about the customer
When you put your cybersecurity attestations on your website, you can frame a message that’s all about your relationship with your customers. There’s plenty you can talk about without giving away the details of your security program to your customers, so finding that balance is important. And remember – most people don’t natively understand security, so be clear and simple in your language and explanations.
Most importantly, remember that your assurance program is an opportunity to engage in a dialogue with people who are interested in how you do business. It’s much more than just the document – it’s a representation of who you are as a business and how you treat your customers.
I’m always happy to speak with people about how to best market their cybersecurity attestations. If you are interested in a conversation, or anything A-LIGN has to offer, please drop us a line!
How to Announce Your Cybersecurity Assessment with a Press Release
You’ve just finished any one of the numerous cybersecurity assessments that are common today. Congratulations… but now what? A-LIGN’s SVP of Marketing, Brian Gladstein, describes some of the ways to leverage that final report and drive new revenue into your business, starting with a press release and an announcement plan.
How to Announce Your Cybersecurity Assessment with a Press Release
You’ve just finished your SOC 2 examination, or received your HITRUST certification, or you’ve completed any one of the numerous cybersecurity assessments that are common today. Congratulations! It must feel good to have the project behind you… but now what? Turns out there are many ways to leverage that final report to help build trust with customers, strengthen your brand, and drive new revenue into your business.
I think it’s safe to say that most people involved in the audit process would not consider themselves “marketers”. In fact, for many, the very idea of self-promotion can be off-putting. But these days, cybersecurity assessments play a critical role in business. They generate trust with a future business partner or serve as a competitive differentiator that wins over a prospect. In this post I want to focus on how to announce your cybersecurity assessment report, and I’ll share some tips I’ve learned after 20 years marketing in the cybersecurity and high–tech industry.
So, whether you’ve got a marketing department or a PR firm writing press releases for you, or it’s something you’ve got to do yourself as an executive at a small business, I hope these pointers and specific examples below will help you get the biggest impact from your assessment report announcement.
Building a Plan
The heart of any announcement like this is the press release – and I’ll dig deep into what to include in that write-up shortly. But press releases don’t exist in a vacuum – you need to get people to read them – so before I write a press release I like to think of how I’m going to get the word out. There are a few easy ways to do this:
- Publish on the wire. There are a variety of wire services that distribute news reports to journalists and news organizations, for example newswire.com ($199 per press release) or Cision/PRWeb ($99-$389 per press release). Find the best fit for you if you don’t use a service already.
- Create a blog post. Press releases tend to have a formal writing style, but a blog post is your chance to make a more personal, human statement about how you take your customers’ security seriously. Be sure to link to the official press release you’ve published.
- Post on social media. Create a catchy graphic (Canva.com is always a great resource) and post about your report on social media. Ask employees to like and share – the increased engagement will help your post get more visibility.
- Email your customers. Don’t underestimate how important a short email announcing the report can be for your customers. Point them to your social media post and ask them to share with their own networks.
- Showcase your badge. Adding the certification or assessment badge to your website, email footers, and other marketing materials can be a quick and easy way to share the achievement with stakeholders. I’ll be sharing more tips on how to feature your certification on your website in an upcoming blog post – stay tuned!
Finally, for important customers and other critical business relationships, it might be worth picking up the phone or integrating the announcement into a regular customer success cadence – that all depends on the ins and outs of your specific business ecosystem.
Writing the Press Release
Let’s get to the writing. I’m not going to go through all the basics of writing and formatting a press release from scratch – there are a number of resources online for that such as this article from Forbes or this one from class:PR. Start with one of those templates and approach the press release as follows:
- Focus on one main idea. Before you put pen to paper, think about what the one, single idea you want your readers to walk away with. You’ll undoubtedly ground the main idea in the news of your report, but you have the opportunity to go beyond just the facts here. Why did you conduct this? What does it mean for your customers? How does this report reinforce your company values? A good press release delivers one powerful message and everything is written to reinforce that message. Start with the end in mind and you’ll end up with a strong press release.
Write your main idea down as a statement, for example:
- We have successfully completed our SOC 2 examination, demonstrating our commitment to protecting customers’ user profiles and personal information.
- We have successfully completed our FedRAMP certification, allowing us to serve a significant portion of the Federal market with our cloud-based product.
- We are proud to announce our HITRUST certification as part of our increased focus on third-party privacy and security across our vendor ecosystem.
- Create a clear, newsworthy headline and subheading. No one will read your press release unless they believe it’s interesting, and they determine that by scanning the headline and maybe the subheading. Take plenty of time to iterate on these first two phrases until you get something that stands out. Shorter is usually better, but don’t water it down too much. Get that main idea in there and drive it home.
Here’s an example that is a great place to start:
MyCompany Completes SOC 2 Type II Audit, Reinforcing Its Commitment to Data Security
Unqualified audit by independent firm provides assurance to cloud-based customers entrusting MyCompany with sensitive information.
- Get right to the point. If you’ve never heard the phrase “buried the lead,” it’s what happens when the important news is so far down in the article that the reader never gets there. People today have short attention spans, so strip out any marketing fluff and get the main news and value points right up front in that first paragraph or two.
CITY, State, Date — Company Name (include link), a (one line description about Company), today announced its successful completion of its System and Organization Controls 2 Type II (SOC 2 Type II) examination for the period of review period, as it looks to (statement about why this report matters, such as demonstrate its commitment to protecting customers’ sensitive information).
The independent examination, conducted by leading cybersecurity assessment firm A‑LIGN, validates that Company’s security practices and controls meet the Trust Services Principles and Criteria for security, availability, and privacy over an extended period of time.
- Use quotes from your leadership and your auditor. Your second or third paragraph should be a quote from your CEO or similarly prominent figure at your company, explaining why this assessment matters in clear, readable language. You can also throw a quote in from your auditor further down the press release (A-LIGN is always happy to provide quotes for our customers).
“Our customers rely on us every day to process critical information that contains sensitive data, which makes protecting that data a top priority for us,” said Executive’s Name, Title of Company. “We are proud to have completed this important examination and assure all our customers that we take security as seriously as they do.”
- Give readers a “next step”. The final paragraph or two of your press release is a good opportunity to describe a little more about the audit you went through and how readers can learn more.
Established by the American Institute of Certified Public Accountants (AICPA), the SOC 2 examination is designed for organizations of any size, regardless of industry and scope, by ensuring the personal assets of their potential and existing customers are protected. SOC 2 reports are recognized globally and affirm that a company’s infrastructure, software, people, data, policies, procedures and operations have been formally reviewed.
In addition to performing a SOC 2 audit on an annual basis, Company will make the report available to current or potential customers upon execution of a non-disclosure agreement (NDA). Visit www.company.com/trust for more details.
- Include boilerplates for your auditor and yourself. Every press release ends with the ABOUT section, a standard description of any company mentioned in the article. These boilerplates are helpful to people scanning many press releases so they can get quick context about the subject of the article without having to do research. Be sure to include contact information for both you and your auditor so people know how to get in touch.
About A-LIGN
A-LIGN is a technology-enabled security and compliance partner trusted by more than 2,500 global organizations to help mitigate cybersecurity risks. A-LIGN uniquely delivers a single-provider approach as a licensed SOC 1 and SOC 2 Auditor, accredited ISO 27001, ISO 27701 and ISO 22301 Certification Body, HISTRUST CSF Assessor firm, accredited FedRAMP 3PAO, candidate CMMC C3PAO, and PCI Qualified Security Assessor Company. Working with small businesses to global enterprises, A-LIGN experts and its proprietary compliance management platform, A-SCEND, are transforming the compliance experience. For more information, visit www.A‑LIGN.com.
Other Press Release Tips
There are a few other concepts worth keeping in mind as you write your press release.
- Don’t treat the press release like ‘marketing’. These articles function much more effectively when they are written clearly and down-to-earth. Use fact-based, direct language that sticks to the who/what/where/why/how.
- Keep it brief. The main body should be no more than 4-6 paragraphs, a couple of sentences each.
- Be relatable. Avoid technical and industry jargon, and write for the average reader. Talk about your accomplishment, but always put it in the context of how your customers and partners will benefit.
More Resources Coming Up
The announcement of your cybersecurity assessment is a big deal. That’s why you should treat it that way. And stay tuned for more tips on marketing your cybersecurity assessment including training your sales team, adding it to your website, and more.
Want to talk more about how to market your cybersecurity assessment? We are happy to help.
Don’t Wait: The Risks of Putting Off Your SOC 2 Audit
For fast-growing businesses, an audit or certification process may be the last thing on the list of priorities and action items. However, compliance with leading regulations, policies, and frameworks is crucial to continued expansion and success.
In today’s highly competitive, mobile, global, and remote business environment, cybersecurity is a top concern for businesses and consumers alike. Data privacy and security has never been more important. It’s likely that if your business wants to work with large customers or those in regulated industries, you will be asked to provide proof of your security controls, especially if you operate a cloud or services business.
System and Organization Controls (SOC) 2 is a voluntary framework designed to ensure that organizations are meeting a set of trust services criteria and implementing controls to protect data. The SOC 2 framework is well-known and thorough—and it’s common for partners, vendors, customers, and other business stakeholders to request proof of SOC 2 attestation from organizations. This proof comes in the form of a SOC 2 Type 1 or Type 2 report from a CPA firm.
From startups to more established companies, SOC 2 has many benefits. If you’ve been delaying the SOC 2 audit process, there are business risks you may unknowingly be facing.
Let’s explore a few of those risks—and why you can’t afford to delay your SOC 2 audit much longer.
Risk 1: Less Competitive Position
Without a SOC 2 report, you may lose business to competitors who have gone through the SOC 2 process and can prove their security chops. Organizations that receive a SOC 2 report can display a SOC 2 logo on their website or other materials—sending a message that they’ve successfully completed an audit and are security-savvy.
Many organizations are required by law to ensure the security of their data—or their customers’ data—and will therefore only work with partners and vendors who can demonstrate secure practices and compliance with regulations. Although SOC 2 is not a regulation or a certification, it is a highly respected, rigorous framework. It’s not unusual for customers, prospects, vendors, and partners to ask service providers to demonstrate SOC 2 “compliance,” often when they’re going through the sales process or at renewal time. This means they’re asking for a SOC 2 report—which can only be obtained via examination and attestation through a CPA firm.
Organizations can get ahead of these requests by completing the SOC 2 audit process. A good place to start is a SOC 2 audit checklist to ensure you have everything ready to start an assessment with a reputable partner firm.
Risk 2: Lost or Interrupted Sales
As noted, requests for a SOC 2 report often come during the sales process. At some point, a prospect may ask for your SOC 2 report before moving any further. At best, lack of a SOC 2 report could interrupt the deal, slowing things down. At worst, it will cost your organization the business.
Since SOC 2 is a rigorous framework, it isn’t something that can be completed overnight from one business call to the next. It requires planning, thought, ongoing cybersecurity controls, and the help of an external auditing partner. In short: it’s best to complete the SOC 2 examination process proactively and keep up compliance before it costs your organization revenue.
Risk 3: Lack of Customer Trust
A SOC 2 report sends a signal to customers that your organization takes security—and the protection of their information—seriously. Obtaining a SOC 2 report indicates a level of maturity around technology and business. In order to pass a SOC 2 examination and receive a letter of attestation successfully, it means an organization is addressing controls in areas including:
- Access control
- Passwords
- Change management
- Incident response
- Logging and monitoring
- And other critical areas of data protection
Without a SOC 2 attestation from a licensed CPA, customers have no way of verifying that their trust is being well-placed. And without trust, it is very difficult to do business.
Risk 4: Vulnerability to Security Threats
One of the most valuable outcomes of pursuing a SOC 2 attestation is improving and maintaining the strength of your own organization’s cybersecurity posture. SOC 2 is comprehensive and covers a wide range of controls, such as those listed above.
Of course, a SOC 2 report does not itself ensure security or assure ongoing compliance. But the controls required to pass an audit—when properly implemented and continuously used—greatly reduce risk to the organization. Each of these controls individually won’t fully protect your company, but, in combination, these elements create a much stronger shield against hackers and other threats (including insider threats from employees, trusted vendors, and others).
It’s also important to point out the value of having security controls audited by a certified, independent firm that specializes in cybersecurity assessments. When internal security teams—or cybersecurity vendors/providers like a managed security service provider (MSSP)—grade their own security controls, there is an inherent bias. Implementation teams have inside knowledge that external, third-party auditing firms don’t. It’s possible for these teams to make assumptions or miss problems because of this knowledge—an independent firm avoids this natural conflict of interest and gives you (and your customers) confidence that the validation process is unbiased.
SOC 2: A Business and Security Advantage
Putting off a SOC 2 audit can hold organizations back in the long run by impacting their competitiveness, slowing the sales process, and more. For organizations looking to compete in today’s security-aware business climate, SOC 2 compliance is a must-have—so don’t delay, and start your SOC 2 journey today.
Five Easy Steps to Get Started With Your SOC 2 Audit
A SOC 2 audit may seem intimidating, but companies can take steps to make the process smoother. We break down five key steps to start on SOC 2 compliance today.
Many organizations hear the word “audit” and freeze—even the idea of an audit conjures a vision of hours spent tracking down paperwork and digital evidence, making organizational changes, and months of work. While an audit may seem overwhelming at the beginning, organizations can take steps to make the process streamlined, smooth, and successful.
One of the most common audits that service organizations seek out is a System and Organization Controls (SOC) 2 audit, which aims to ensure that the organization employs adequate controls to protect customer information in its systems. Meeting the AICPA’s SOC 2 criteria can look slightly different for every organization, and organizations must attain a report by a CPA firm to document the attestation.
Oftentimes, these reports—which come in two formats, SOC 2 Type 1 and Type 2 reports—will be requested by prospective customers as part of their due diligence for new partners, or as part of their own audit and risk management processes.
Attaining and maintaining an annual SOC 2 attestation is valuable to many service providers. As noted, SOC 2 is often a requirement to do business with certain partners or customers. It can help build customer and partner confidence in your organization’s security and it demonstrates you take their trust seriously. By implementing the best practices required to meet the SOC 2 trust services criteria, your organization can uncover security vulnerabilities, remediate them, and ensure a responsible level of security practices.
In this post, we will walk through five key steps that can make the SOC 2 audit process less intimidating, especially if you’re seeking SOC 2 for the first time. Use these steps to get in shape for an audit and start your SOC 2 journey today.
Prioritize the Most Important Controls
The technology landscape is getting more complicated every year, and threat actors are always looking for a way into organizations to steal or exploit their data. Security controls are crucial for preventing or limiting the impact of breaches, yet it can seem like an endless list of to-dos and must-haves.
Before diving headlong into a SOC 2 audit with an external partner, examine the different controls required by SOC 2 and bolster any gaps you are aware of. By prioritizing the controls your organization needs, compliance becomes bite-sized—and less intimidating.
The areas of controls that are most important during a SOC 2 examination include:
- Information Security
- Access Control
- Password Management
- Change Management
- Risk Assessment and Mitigation
- Incident Response
- Logging and Monitoring
- Vendor Management
- Data Classification
- Acceptable Use
- Information, Software, and System Backup
- Business Continuity and Disaster Recovery
Determine which policies and procedures need the most attention, and in what order. Then, begin working through them methodically. A few ways to prioritize policies could include:
- Starting with those that require the least work, so you can tally up accomplishments
- Starting with those that require the most work, so you get them out of the way and can assess your time commitment going forward
- Starting with those that are the most visible to build awareness and momentum within your organization around the effort
Schedule Key Compliance Tasks to Stay on Track
In some ways, practicing year-round compliance is like going to the dentist—you may only visit your dentist once or twice a year for a cleaning, but you still brush, floss, and rinse every day. Good dental hygiene doesn’t happen as a result of a single visit, and neither does SOC 2 compliance.
If you’re seeking a SOC 2 audit, one of the best ways to make the process easier and to reduce the chances of an undesirable outcome to your audit is to practice compliance year-round—rather than in a rush at audit time. Cybersecurity threats never sleep, and neither can your controls.
Once you’ve determined your priority policies and procedures, break down the components of each and make a list of the controls that need to be put in place and kept up. Some activities can be done weekly, such as checking your logs, while others can be monthly or quarterly, such as reviewing access to systems or conducting vulnerability scans.
Make a timeline of these activities or a SOC 2 checklist, and then hold the organization accountable for maintaining each element. This will make your life much easier at audit time, and it reduces the likelihood of needing remediations.
Get Started with Audit Automation
As technology becomes more advanced and security risks grow, organizations are increasingly building the audit process into their cybersecurity stack. Elements of the auditing process can be automated, which can reduce the time needed for preparation and make auditing faster.
For example, our A-SCEND compliance management software can centralize and store evidence, re-use and repurpose evidence for multiple audits or frameworks, automatically create requests, track milestones in the audit process, and more. All of this reduces the pressure on an organization’s staff and also ensures that information makes its way into the right place.
IT organizations are looking for every opportunity to automate their tech stack, so they can move faster and get more done with fewer people. Implementing compliance management and audit automation software is a great way to get some small wins quickly.
Start Small and Grow Alongside Your Business’ Needs
Don’t bite off more than you can chew—especially when it’s your first time completing an audit of any kind. The SOC 2 criteria are flexible, and organizations can choose to comply with only the common criteria or to add in additional criteria. Either way, make sure you right-size with the correct criteria and keep your process streamlined and efficient.
This attitude applies to your auditing and security approach in general. While SOC 2 is an excellent framework for service providers to start with, compliance and regulations tend to grow alongside businesses as they expand. It’s likely that you will encounter more applicable regulations or requirements in the future.
For example, if you are a service organization and you begin working with payment card data, the Payment Card Industry Data Security Standard (PCI DSS)—a requirement from most global credit card providers—may become crucial. Depending on your client base, industry, business strategy, and how you expand, other possible requirements could include HITRUST, FedRAMP, ISO 27001, and more.
Completing a SOC 2 audit is an excellent learning experience. It can help your organization get into the right mindset for future certifications, frameworks, and regulations. And as you are subject to more compliance directives, you can build off what you’ve learned from the SOC 2 process.
Choose a Partner—Not Just an Auditor
SOC 2 compliance must be certified by an external auditor. For an organization seeking a SOC 2 report for the first time, an expert guide can be a boon. With deep experience and trained eyes, the right audit partner can help companies complete the auditing process smoothly and confidently. Notice that I used the word partner—not vendor or even auditor.
Attaining and maintaining compliance is not a one-time endeavor, and as organizations grow, they’re likely to encounter further policies, frameworks, and regulations that require certifications and audits, such as ISO 27001 or HITRUST. It takes a partner who will walk, step for step, beside your organization. A partner will take the time to understand your business, provide guidance and support around the audit experience, and help you reach your goals.
Getting Started on SOC 2 Compliance
Organizations beginning the SOC 2 audit process for the first time can get the ball rolling with the five steps above. By understanding and prioritizing controls, getting into shape internally with regard to policies and procedures, finding ways to automate the audit process, and joining forces with a true partner, SOC 2 compliance is within reach.
The A-LIGN Advantage: Unify Your Audit Experience
The emergence of automated security and compliance solutions still leaves organizations with a problem: these point solutions are unable to provide independent third-party certification. Preparation is a key component to a successful audit, but it is only the first step. A-LIGN is transforming how organizations demonstrate compliance by combining its compliance management platform, A‑SCEND, with its years of audit experience through a single-provider approach – from audit readiness to certification, across multiple security frameworks.
An audit encompasses readiness, evidence collection, fieldwork, reporting, and certification. Investing into readiness software alone creates a “last mile” problem, meaning that an organization will still need to invest time and money into an additional service provider to complete its audit. There is a management adage that “a failure to plan is planning to fail,” but when a solution is only focused on preparation then an organization may experience a failure to execute.
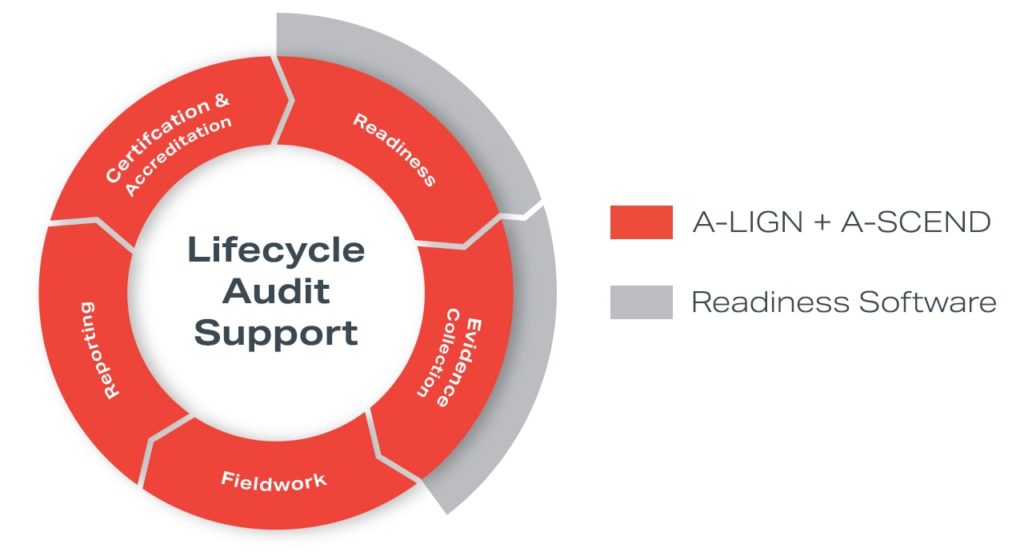
The image above only tells part of the story. Not only are automated security and compliance solutions limited in their capabilities, but they are also limited in their qualifications. A-LIGN has completed more than 10,000 audits for more than 2,500 clients in the past decade, making it the only trusted service provider with the ability to combine the depth and breadth of its expertise with an end-to-end compliance management platform, A-SCEND.

Automated security and compliance solutions are limited in their scope since they are unable to address many common security frameworks. Many organizations start with a SOC 2 audit, but soon expand to additional standards. The fact that automated security and compliance solutions are limited to SOC 2 can be a major hindrance for organizations seeking to consolidate their audit process. A-LIGN’s compliance management platform, A-SCEND, can centralize evidence collection, standardize compliance requests, and consolidate the audit process to streamline compliance across multiple frameworks.
According to the Gartner Market Guide for Organization Security Certification Services published on May 26, 2020 by Brent Predovich, Katell Thielemann, and Sam Olyaei, they recommend organizations “ Consolidate audits when there is a need to obtain more than one certification or attestation, and leverage one certification provider.”
Automated security compliance solutions fall short with their capabilities, qualifications, and scope, but perhaps the most important point to consider is that their feature set is being commodified by tech-enabled audit service providers like A-LIGN. A-LIGN is a strategic compliance partner, capable of addressing each step of the audit, across the scope of each major framework, qualified with its deep compliance expertise, while still delivering the strategic benefits of a technology solution. Contact A-LIGN today to learn how its compliance management platform can make it easier for you to complete your audits with a single-provider approach that also delivers your certification.
Set Reminders and Stay On Track with this PCI DSS Timeline
Many organizations struggle to keep up with the PCI compliance. We walk through three key areas and share a resource with over 57 requirements to check off and the related timeframes prescribed by the PCI DSS that you need to adhere to.
Credit card, debit card, and other financial data are extremely valuable, both to the people it belongs to and to cybercriminals. Like personally identifiable information (PII), financial data can be used for malicious purposes, which is why the Payment Card Industry Data Security Standard (PCI DSS) exists. Organizations that are PCI compliant demonstrate to customers, vendors, and partners that they take payment card security seriously—and this is nonnegotiable in today’s increasingly mobile, global, and remote landscape.
Yet maintaining PCI compliance is a challenge for many organizations. In fact, a surprisingly low number of organizations comply fully: In 2019, only 27.9 percent of organizations were fully in compliance with PCI DSS during interim validation and required some form of remediation, according to the 2020 Verizon Payment Security Report.
From small to midsize businesses (SMBs) to large enterprises, keeping track of all the daily, monthly, yearly, and other PCI requirements can be difficult. Many organizations fall behind or lose track of activities. This means that when it comes time to demonstrate compliance, it’s a scramble.
Given this, we have created PCI DSS by Numbers: A Cheat Sheet of Timeframes to Meet PCI DSS Requirements. Our cheat sheet breaks down the 57 core PCI DSS requirements that have timeframes associated with them and clarifies when they need to happen. This interactive cheat sheet lets you flip through the different types of timeframes you need to be aware of when it comes to PCI DSS:
- Response times: How quickly you need to respond to issues, incidents or important events
- Expirations: How long until items like policies, system hardening documents, or authentication passwords expire and must be updated
- Recurrences: How frequently information should be evaluated or tasks should be performed
- Retention: How long you need to hold on to sensitive or archived information
PCI DSS by Numbers gives a complete view of the timelines PCI DSS demands, but in this post, we wanted to explore three areas of security that have numerous milestones to meet in their own right. Each of these areas are fundamental for any organization, and all must be addressed regularly. Read on to learn more about why your organization needs to hit them.
Effectively Manage Logs
Logs are an important part of an organization’s security posture. By keeping a record of all activity within their systems, organizations can more easily identify cybersecurity threats and investigate what happened, why, how, and by who.
PCI DSS includes several requirements around log collection, analysis, and management, such as:
- Daily: Review all logs, including all security events; any logs that involve cardholder data (CHD) and/or sensitive authentication data (SAD); critical components; servers and security elements, such as firewalls.
- Three Months: At this point, a trail log should be available internally for analysis. The organization should also be maintaining visitor logs.
- Annually: Review media inventory logs to ensure that periodic assessments of your media and storage assets are taking place.
- Periodically: While the timing will depend on the organization’s risk levels, periodic log reviews include components not covered in the daily log review.
Manage Passwords
Passwords are an important security measure, but they must be strong and well protected. PCI DSS requirements for passwords span various timeframes and scenarios, but all are aimed at ensuring that passwords are carefully managed so that only legitimate users have access to corporate systems.
For example, password-related requirements include:
- Immediately: If a user is terminated, their access must be revoked without delay.
- 30 Minutes: If a password times out, accounts should lock users out for 30 minutes.
- 90 Days: Every 90 days, organizations should prompt their users to change their passwords.
- At First Use: If someone is using the system for the first time, they should be prompted to change their new or forgotten password.
- Minimum Length: To be PCI DSS compliant, passwords should be at least seven characters long.
- Lockouts: If a password has been incorrectly attempted six times, the system should lock the user out.
- Periodically: While the exact time frame is up to the organization’s discretion, non-consumer customer users should be prompted to change their passwords from time to time. This requirement applies only to service providers.
Conduct Regular Vulnerability Scans
Organizations can only protect what they can see. Vulnerability scanning is a valuable tool for organizations to understand the weaknesses in their security postures and remedy them before a threat actor uncovers them.
Vulnerability scanning must be conducted at least every quarter according to PCI DSS, and both internal and external penetration testing should take place at least annually, although many organizations choose to do pen testing more frequently. Under PCI DSS, penetration testing is also required if there is a significant change to the system, such as an infrastructure upgrade or sub-system replacement.
To comply with PCI DSS year-round, organizations should ensure the following schedule is being followed:
- Six Months: Service providers must conduct penetration tests on their segmentation controls. Non-service providers are exempt.
- Annually: All organizations should perform internal and external penetration testing, as well as penetration testing on their segmentation methods.
- After Significant Changes: In these cases, organizations must conduct the same testing as the step above: internal, external, and segmentation method penetration testing.
Dive Deeper into PCI DSS Compliance
As you can see, cybersecurity is a continuous practice. Each area of focus named above requires attention year-round—sometimes in frequent intervals, and sometimes annually.
Organizations that plan ahead, anticipate timelines, and keep up with activities are much more likely to succeed at maintaining PCI DSS compliance, giving their customers, partners, and other stakeholders reassurance that payment card security is top of mind. The three areas above are only a small subset of the requirements for PCI DSS compliance. Explore our full PCI DSS requirement timeframe cheat sheet for a list your organization can use to stay ahead and stay compliant.
Ensure You’re Meeting All Your PCI DSS Milestones with the A-LIGN PCI Requirement Timeframe Cheat Sheet
What are theSOC 2 Trust Services Criteria?
The SOC 2 audit process includes five categories of Trust Services Criteria: Security, Availability, Confidentiality, Processing Integrity, and Privacy. These categories each cover a set of internal controls related to different aspects of your information security program.
So you’ve decided to engage an auditor and produce your first SOC 2 report. It’s a smart thing to do, as more and more organizations are expecting that you’ve completed a SOC 2 as a pre-condition to doing business. Conducting an independent cybersecurity audit like a SOC 2 sends a strong signal that you take security seriously and have invested in processes and systems that will protect your customers’ and business partners’ data and sensitive information. In fact, getting your SOC 2 done can be a competitive differentiator these days.
One of the first decisions you’ll need to make regarding your SOC 2 is which of the 5 Trust Services Criteria categories you will include in your audit process. These categories each cover a set of internal controls related to different aspects of your information security program. The 5 Trust Services Criteria categories are:
- Security (or Common Criteria)
- Availability
- Confidentiality
- Processing Integrity
- Privacy
The first category, Security, is required to be in scope for every SOC 2 audit and is therefore frequently referred to as the Common Criteria. Sorry folks, you don’t get a choice about this one. The rest of them, however, is up to you to include or not.
Which Trust Services Criteria Should I Include?
While the Security category is a must-have, you are able to define the scope of your audit to include or not include the remaining four categories. How should you decide which to include? Start by developing an understanding of what your customers and business partners are asking for – what they need.
And remember, your SOC 2 report will be valid for 12 months, which can be a long time in business. The more you include the more robust that report will be, and the more likely it is to satisfy a greater number of customers with growing expectations.
1. Security (Common Criteria)
The Security Category refers to the protection of information throughout its lifecycle. Security controls are put in place to protect against unauthorized access, unauthorized disclosure, or damage to systems that could affect other criteria beyond the Security Category. Security controls are designed to include a wide array of risk-mitigating solutions, such as endpoint protection and network monitoring tools that prevent or detect unauthorized activity. Entity-level and control environment topics are also considered to provide that the necessary controls are in place to govern organization-wide security.
You must always include the Security category – it’s required.
2. Availability
The Availability Category considers controls that demonstrate systems maintain operational uptime and performance to meet stated business objectives and service level agreements. Availability does not set a minimum acceptable performance level, but it does address whether systems include controls to support and maintain system operation, such as performance monitoring, sufficient data backups and disaster recovery plans.
Consider including Availability if your customers have concerns about downtime, including Service Level Agreements (SLAs).
3. Confidentiality
The Confidentiality Category requires companies to demonstrate the ability to protect confidential information throughout its lifecycle, including collection, processing and disposal. The specific requirements for Confidentiality related controls may be defined by laws and regulations, as well as internal management or external partner agreements. Confidential information may include personal information, as well as other information, such as trade secrets and intellectual property. Controls for Confidentiality include encryption and identity and access management.
Consider including Confidentiality if you are storing sensitive information that is protected by Non-Disclosure Agreements (NDAs), or if your customers have requirements to delete data that’s no longer needed.
4. Processing Integrity
The Processing Integrity Category focuses on ensuring that data is processed in a predictable manner, free of accidental or unexplained errors. In other words, the information produced or manipulated by your systems needs to be accurate and reliable. Because of the number of systems used by an entity, processing integrity is usually only addressed at the system or functional level of an entity.
Consider including Processing Integrity if your customers are executing critical operational tasks on your systems, such as financial processing or data processing.
5. Privacy
The Privacy Category is similar to Confidentiality, but specifically refers to Personally Identifiable Information (PII), especially that which your organization captures from customers. The Privacy Category covers communication, consent, and collection of personal information, and verifies appropriate parties have access to that information and what can be done with it. Controls for Privacy include privacy policies and consent management mechanisms.
Consider including Privacy if your customers are storing Personally Identifiable Information (PII) such as social security numbers, birthdays, or healthcare data.
Learn More About SOC 2
Determining the appropriate Trust Services Criteria to include in your SOC 2 audit is obviously an important decision, and it’s one that a strong partner like A-LIGN can help you make. We have worked with thousands of clients, helping them scope their SOC 2, prepare for the audit, execute it efficiently, and get their final report faster. You may also find more valuable information in our SOC 2 resource library, and of course, we are always happy to chat about your situation with you and see how we can help.
Get Ahead of Your SOC 2 Before it’s an Emergency
As a licensed CPA firm with more than 10 years of experience and thousands of completed SOC audits, we know better than anyone how to help make the SOC 2 audit experience efficient and pain-free. With A-LIGN’s white-glove treatment, you’ll see how audit planning and preparation can go a long way to grow your business. The compliance process doesn’t have to be daunting, and if you get ahead of the demand, your organization, and future customers, will ultimately benefit.
Don’t wait. Let us help you get started with a SOC 2 readiness assessment today.
What’s The Difference Between SOC 2 Type I and Type II?
The difference between a SOC 2 Type I audit and a SOC 2 Type II audit is how the controls are evaluated – at a single point in time, or over a period of time. This decision can be driven by budget, timing, resources available, and what customers are asking for.
As you get ready to begin your SOC 2 audit, you’ll need to make a few decisions. First, you’ll have to choose an independent, accredited CPA firm, such as A-LIGN who can partner with you and help you produce your SOC 2 report smoothly and efficiently. Then you’ll have to decide which of the 5 Trust Services Criteria to include: Security, Availability, Confidentiality, Processing Integrity, and Privacy. This will determine the scope of the project and which controls will be evaluated.
You’ll also need to decide if you conduct a SOC 2 Type I audit or a SOC 2 Type II audit. But what’s behind that decision? It’s actually not that complicated – let’s cover it here.
Type I & Type II: Point-in-Time or Over a Duration
The difference between a SOC 2 Type I audit and a SOC 2 Type II audit is how the controls are evaluated – specifically, is your auditor going to examine them at a single point in time, or will they be evaluated over a period of time?
SOC 2 Type I audits attest to the design and implementation of controls at a single point in time. The auditor will review evidence from your systems as it exists at a particular “moment in time” and produce a Type I report.
SOC 2 Type II audits attest to the design, implementation and operating effectiveness of controls over a period of time, typically between 3 and 12 months. A Type II audit provides assurance that controls are not only designed and implemented, but that they operated effectively and as intended over the defined period of time.
A SOC 2 Type II will generally provide a greater level of trust to a customer or business partner due to the increased visibility of systems in action.
What Type of SOC 2 Audit is Right for Me?
There are a variety of factors you’ll need to consider to determine if you should proceed with a SOC 2 Type I or Type II audit, including your timing, your budget, the resources you have available, and of course what your customers or business partners are asking for. We’ve also got a number of other resources available to help you learn about SOC 2 in our SOC 2 resource library. Of course, we here at A-LIGN are happy to help you work through this question or any others you may have about the SOC 2 audit process.
Get Ahead of Your SOC 2 Before it’s an Emergency
As a licensed CPA firm with more than 10 years of experience and thousands of completed SOC audits, we know better than anyone how to help make the SOC 2 audit experience efficient and pain-free. With A-LIGN’s white-glove treatment, you’ll see how audit planning and preparation can go a long way to grow your business. The compliance process doesn’t have to be daunting, and if you get ahead of the demand, your organization, and future customers, will ultimately benefit.