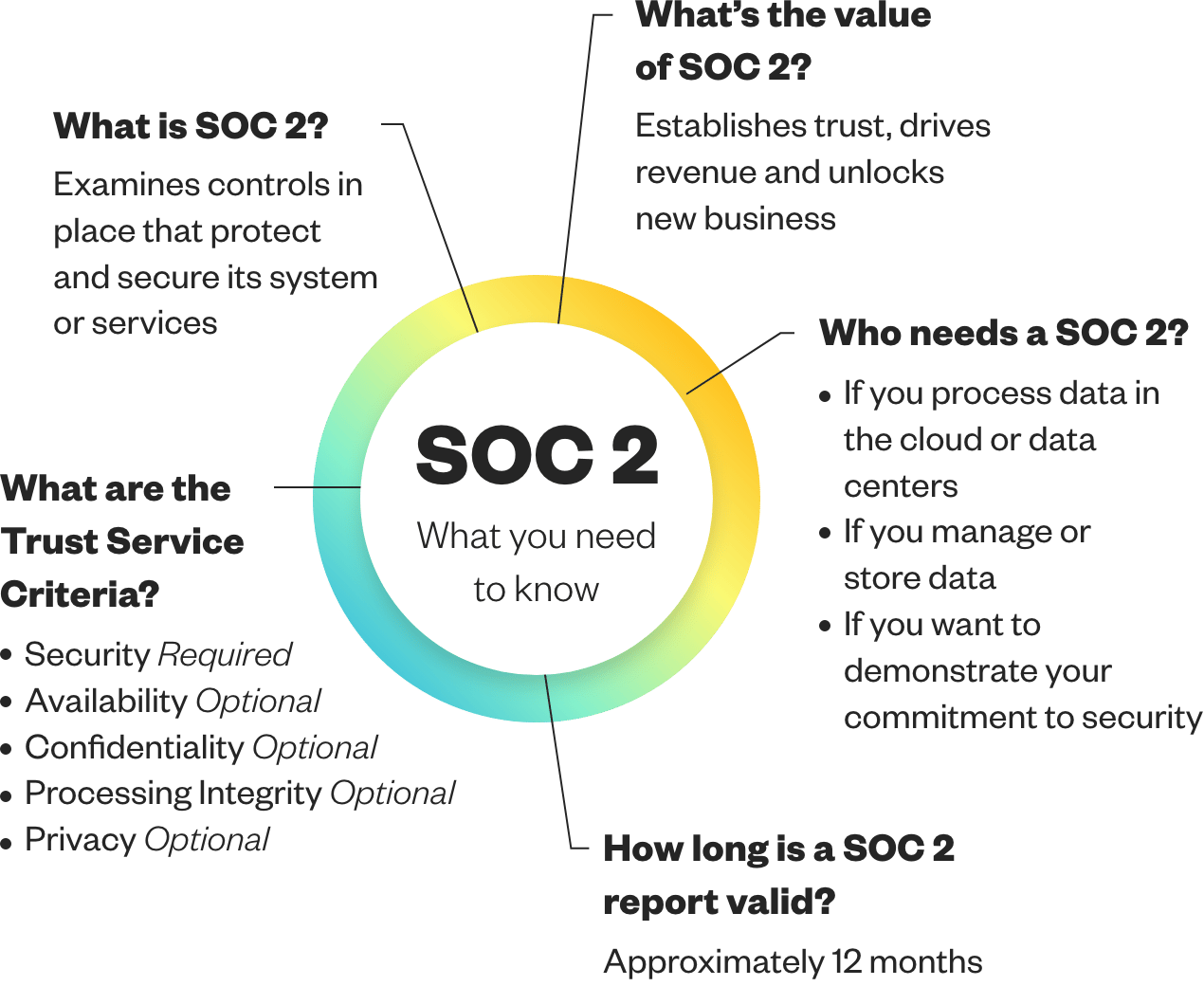
SOC, which stands for System and Organizational Controls, is a framework developed by the American Institute of Certified Public Accountants (AICPA) for the purpose of providing regular, independent attestation of the controls that a company has implemented to mitigate information-related risk.
There are three types of SOC audits: SOC 1, SOC 2, and SOC 3. When it comes to cybersecurity, SOC 2 has become the
de facto standard.
In a SOC 2 audit, you describe the policies, procedures, and systems you have in place to protect information across five categories called Trust Services Criteria. Your independent auditor evaluates the evidence you supply for the controls in each category, and when completed you receive your official SOC 2 compliance report that you can share with customers and business partners to assure them that their data will be handled securely.
What is SOC 2 cOMPLIANCE?
Your customers and partners want to know that you are going to protect their data, and they want to see that validated by an independent organization. A SOC 2 report provides that trust, allowing you to get the edge over your competitors, close deals faster, and win more business. Plus, doing a SOC 2 report now could save you hours upon hours of headaches and fighting fires down the road when an important business transaction depends on it.
HOVER OVER FOR MORE INFORMATION
Describe your organization’s system as a whole
Tests a specific point in time
Assesses the design of your organization’s internal controls
Decribes your organization’s system as a whole
Assesses the design of your organization’s controls, as well as their operating effectiveness
Focuses on a period of time in which the controls are operating
Features detailed descriptions of the auditor’s tests and test results of the controls
Benefits of SOC 2 COMPLIANCE
Demonstrates a commitment to corporate governance
Protects sensitive information stored in the cloud
Key benefits:
The SOC 2 Process
GETTING STARTED
The SOC 2 Examination
A readiness or gap assessment gives you a good idea of how much work you'll need to do to successfully pass your audit. This process reviews the controls you have in place and points out those that need to be improved or implemented outright. Gap assessments are a great way to start the compliance process because the pressure is off, so to speak – allowing you to take care of issues ahead of time, before that huge customer is on the line and your CEO is breathing down your neck.
In an ideal world, an organization would first go through a readiness assessment prior to completing a SOC 2 examination for the first time.
Why do a readiness assessment?
Identify high-risk control gaps
Get recommendations for improving controls
Remediate issues prior to the official SOC 2 examination
Readiness Assessment
Step 2
Step 4
Step 5
Step 1
Step 3
During the scoping phase, your auditor works with you to better understand your environment, the information you are protecting, and any controls you have in place. This is also a great time to take advantage of your auditor's expertise and get a better understanding of the SOC 2 framework and the Trust Services Criteria that comprise it.
Scoping
Top 12 Policies to Establish
Allows you to kiss the 500-question security questionnaire good-bye
Serves as a competitive advantage, winning trust and driving revenue
Provides assurance to customers and partners that your systems are secure
Satisfies requirements for organizational and regulatory oversight
The 5 Trust Services Criteria in a SOC 2
Want to get a head start on your SOC 2 examination? Start with these 12 policies. They are the most important to establish when undergoing your audit, and will give you the biggest bang for the buck across your overall security posture.
SOC 2 Compliance
The Definitive Guide
SOC 2 might be right for you if:
Organizations are satisfied with their ability to detect cybersecurity threats
Organizations encountering leaks of sensitive data and data spillage in the last 12 months
73%
SOC 2 is an extremely popular form of cybersecurity audit, used by a rapidly growing number of organizations to demonstrate they take cybersecurity and privacy seriously.
In a world filled with data breaches and information leaks, establishing trust is not only critical to your revenue stream, but it can be a competitive differentiator when closing new business. Customers and partners seek assurances that the companies they work with are doing everything they can to avoid exposing sensitive information and creating risk. That's exactly why SOC 2 compliance is important.
You process information in the cloud or in data centers
What is SOC 2?
Benefits of SOC 2
The SOC 2 Process
SOC 2 Type II audits attest to both the design and the operating effectiveness of those controls over a period of time, typically between 3-12 months. This type of SOC audit provides assurance of not just how your systems are set up, but how they are used on a day-to-day basis
A SOC 2 Type II will generally provide a greater level of trust to a customer or business partner due to the increased visibility of systems in action.
When it comes to SOC 2, you need a partner, not just an auditor. The A-LIGN team is available to assist you with your SOC 2 audit, or any of your cybersecurity and compliance needs. Complete the contact form and our team will reach out within 24 hours.
Talk to an
Expert
Type 2 Report
Did You Know?
46%
SOC 2 Type I audits attest to the design of controls at a single point in time. The auditor will review evidence from your systems as it exists at a “moment” and produce the Type I report based on that.
Type 1 Report
Benefits of
SOC 2 Compliance
Step 1
After the scoping phase is complete, your auditor will walk you through the SOC 2 Examination process and provide an Information Request List, or IRL. The IRL maps to standard requirements for a SOC 2 report, such as:
• Change Management
• Computer Operations – Backup
• Information Security
• Physical Security
• Vendor Management
• Risk Assessment
• Internal Controls
You should review each of the requests within the IRL to ensure you understand what is being requested, then begin to gather and provide the requested evidence to the auditors.
Audit Planning
Step 2
Once all evidence is collected, the auditor begins reviewing it and completes the required testing, which is either performed remotely, onsite or a combination of both. Remote SOC examinations have become particularly important during the COVID-19 pandemic.
During this phase, the following key activities take place:
• Overview of key process, procedures,
systems, and controls in place
• Review of all evidence provided and
observed
• Documentation of identified controls
• Reconciliation of any gaps in
documentation or unclear evidence
• Proactive notification of potential
exceptions or issues with the audit
Testing and Review of Evidence
Step 3
Once all your evidence has been shared with your auditor, tested, and reviewed to ensure nothing is missing, the auditor can officially accept your evidence and begin preparing your draft report. When you receive the draft report, you will have the opportunity to provide comments and suggest updates. Return the draft with a signed copy of the management representation letter that accompanies it, an important part of the independent nature of the auditor relationship.
Closing Meeting and Draft Report
Step 4
Are you ready to get started with your SOC 2?
Are you ready to get started?
Finally, your SOC 2 examination comes
to an end with the delivery of the final report. Your auditor will address any comments you had submitted in the draft, at which point the report is finalized and delivered to your organization electronically (a hardcopy can also be requested).
Because of the sensitive nature of the information contained in a SOC 2 report, it is generally advisable to require outside parties (customers or business partners) to sign a non-disclosure agreement (NDA) in order to view it. Alternatively, a SOC 3 report can also be produced which is based on the SOC 2 report but excludes any sensitive information. For that reason, SOC 3 reports are sometimes posted on publicly available websites and distributed broadly to anyone who has a desire to see it.
The Final Report
Step 5
Contact us

The Definitive Guide



You manage or store data for US-based customers and business partners
You’re looking to improve your overall security posture
You want to increase the valuation of your organization
You want to beat competitors, win more deals and accelerate growth
You want to demonstrate
your commitment to security and privacy
Controls that protect against unauthorized access, unauthorized disclosure, or damage to systems. Examples include endpoint protection and network monitoring.
Controls that keep systems operational and available at a level that meets stated business objectives. Examples include performance monitoring and disaster recovery.
Controls that ensure systems perform in a predictable manner, free of accidental or unexplained errors. Examples include software development lifecycle management and quality assurance.
Controls that protect confidential information throughout its lifecycle from collection and processing to disposal. Examples include encryption and identity and access management.
Controls specific to protecting personal information, especially that which you capture from customers. Examples include privacy policies and consent management.
Security
Availability
Processing Integrity
Confidentiality
Privacy

1
2
2
3
1
3
4
1
2
3
4
5
6
Contact us
1

After the scoping phase is complete, your auditor will walk you through the SOC 2 Examination process and provide an Information Request List, or IRL.
You should review each of the requests within the IRL to ensure you understand what is being requested, then begin to gather and provide the requested evidence to the auditors.
Audit Planning
2
Step 2
Step 1
• Vendor Management
• Risk Assessment
• Internal Controls
• Change Management
• Computer Operations – Backup
• Information Security
• Physical Security
The IRL maps to standard requirements for a SOC 2 report, such as:
Once all evidence is collected, the auditor begins reviewing it and completes the required testing, which is either performed remotely, onsite or a combination of both. Remote SOC examinations have become particularly important during the COVID-19 pandemic.
During this phase, the following key activities take place:
• Overview of key process, procedures, systems, and controls
in place
• Review of all evidence provided and observed
• Documentation of identified controls
• Reconciliation of any gaps in documentation or unclear evidence
• Proactive notification of potential exceptions or issues with
the audit
Testing and Review of Evidence
3
Step 3
Once all your evidence has been shared with your auditor, tested, and reviewed to ensure nothing is missing, the auditor can officially accept your evidence and begin preparing your draft report. When you receive the draft report, you will have the opportunity to provide comments and suggest updates. Return the draft with a signed copy of the management representation letter that accompanies it, an important part of the independent nature of the auditor relationship.
Closing Meeting and Draft Report
4
Step 4
Finally, your SOC 2 examination comes to an end with the delivery of the final report. Your auditor will address any comments you had submitted in the draft, at which point the report is finalized and delivered to your organization electronically (a hardcopy can also be requested).
Because of the sensitive nature of the information contained in a SOC 2 report, it is generally advisable to require outside parties (customers or business partners) to sign a non-disclosure agreement (NDA) in order to view it. Alternatively, a SOC 3 report can also be produced which is based on the SOC 2 report but excludes any sensitive information. For that reason, SOC 3 reports are sometimes posted on publicly available websites and distributed broadly to anyone who has a desire to see it.
The Final Report
5
Step 5
HOVER OVER FOR MORE INFORMATION
1
Information Security Policy
2
Access Control Policy
3
Password Policy
4
Change Management Policy
5
Risk Assessment
and Mitigation Policy
6
Incident Response Policy
7
Logging and Monitoring Policy
8
Vendor Management Policy
9
Data Classification Policy
10
Acceptable Use Policy
12
11
Information, Software
and System Backup
Business Continuity
and Disaster Recover
1
Information Security Policy
Ensures company assets and data are appropriately protected from unauthorized access and disclosure




2
Access Control Policy
Dictates how logical and physical access to company systems is provisioned, managed, and revoked
3
Password Policy
Describes the standards for creating strong passwords, protecting those passwords, and changing them frequently
4
Change Management Policy
Outlines how changes to IT infrastructure and applications are planned, documented, managed, and controlled
5
Risk Assessment and Mitigation Policy
Describes how periodic assessments are conducted to identify risks, analyze them, and determine mitigation strategies
6
Incident Response Policy
Controls the rules security personnel follow when a security incident occurs, such as malware or a DoS attack
7
Logging and Monitoring Policy
Describes how user activity is logged, as well as how those logs are monitored and reviewed
8
Vendor Management Policy
Highlights the risks posed by vendors that perform key processes, and how to mitigate those risks
9
Data Classification Policy
Establishes how data is classified based on its level of sensitivity, value and criticality to the organization
10
Acceptable Use Policy
Communicates how internal and external users should use information and company assets appropriately
11
Information, Software and System Backup
Defines requirements for backup of company data and systems, including frequency, location, and retention
12
Business Continuity and Disaster Recover
Outlines a plan to continue operations in the event of a disaster that disrupts the business's ability to function
1
Information Security Policy
Ensures company assets and data are appropriately protected from unauthorized access and disclosure
Contact Us

73%

46%
You want to demonstrate your commitment to security and privacy
You want to beat competitors, win more deals and accelerate growth
You want to increase the valuation of
your organization
You’re looking to improve your overall security posture
You manage or store data for U.S.-based customers and business partners
You process information in the cloud or in data centers
SOC 2 might
be right
for you if:


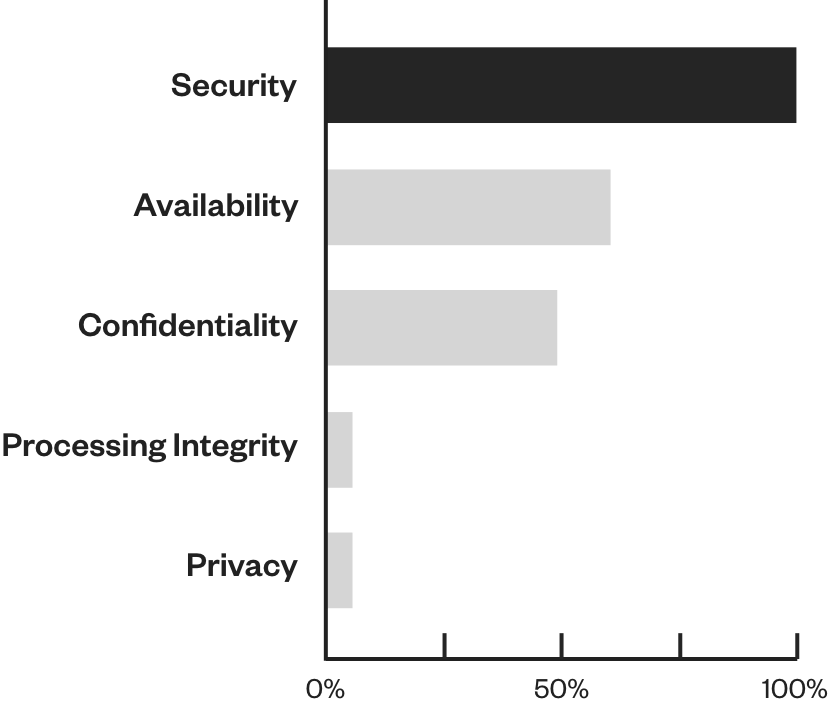
Percentage of A-LIGN's customers
that evaluate each criteria
Tap on each criteria to view more
Controls that protect against unauthorized access, unauthorized disclosure, or damage to systems. Examples include endpoint protection and network monitoring.
Controls that keep systems operational and available at a level that meets stated business objectives. Examples include performance monitoring and disaster recovery.
Controls that protect confidential information throughout its lifecycle. Examples include encryption and identity and access management.
Controls that protect confidential information throughout its lifecycle from collection and processing to disposal. Examples include encryption and identity and access management.
Controls specific to protecting personal information, especially that which you capture from customers. Examples include privacy policies and consent management.
Security
Availability
Processing Integrity
Confidentiality
Privacy

SOC 2 Type I audits attest to the design of controls at a single point in time. The auditor will review evidence from your systems as it exists at a “moment” and produce the Type I report based on that information.
Type 1 Report
Describe your organization’s system as a whole
Assesses the design of your organization’s internal controls
Tests a specific point in time
1
2
3
Allows you to kiss the
500-question security questionnaire good-bye
Serves as a competitive advantage, winning trust and driving revenue
Satisfies requirements for organizational and regulatory oversight
Provides assurance to customers and partners that your systems are secure
Demonstrates a commitment to corporate governance
Protects sensitive information stored in the cloud
1
2
3
1
Decribes your organization’s system as a whole
2
Assesses the design of your organization’s controls, as well as their operating effectiveness
3
Focuses on a period of time in which the controls are operating
4
Features detailed descriptions of the auditor’s tests and test results of the controls
SOC 2 Type II audits attest to both the design and the operating effectiveness of those controls over a period of time, typically between 3-12 months. This type of SOC audit provides assurance of not just how your systems are set up, but how they are used on a day-to-day basis. A SOC 2 Type II will generally provide a greater level of trust to a customer or business partner due to the increased visibility of systems in action.
Type 2 Report
5
6
4
Contact Us



TAP FOR MORE INFORMATION
12 Business Continuity and Disaster Recover
11 Information, Software and System Backup
10 Acceptable Use Policy
9 Data Classification Policy
8 Vendor Management Policy
7 Logging and Monitoring Policy
6 Incident Response Policy
5 Risk Assessment and Mitigation Policy
4 Change Management Policy
3 Password Policy
2 Access Control Policy
1 Information Security Policy
12
Business Continuity and Disaster Recover
Outlines a plan to continue operations in the event of a disaster that disrupts the business's ability to function
11
Information, Software and System Backup
Defines requirements for backup of company data and systems, including frequency, location, and retention
10
Acceptable Use Policy
Communicates how internal and external users should use information and company assets appropriately
9
Data Classification Policy
Establishes how data is classified based on its level of sensitivity, value and criticality to the organization
8
Vendor Management Policy
Highlights the risks posed by vendors that perform key processes, and how to mitigate those risks
7
Logging and Monitoring Policy
Describes how user activity is logged, as well as how those logs are monitored and reviewed
6
Incident Response Policy
Controls the rules security personnel follow when a security incident occurs, such as malware or a DoS attack
5
Risk Assessment and Mitigation Policy
Describes how periodic assessments are conducted to identify risks, analyze them, and determine mitigation strategies
4
Change Management Policy
Outlines how changes to IT infrastructure and applications are planned, documented, managed, and controlled
3
Password Policy
Describes the standards for creating strong passwords, protecting those passwords, and changing them frequently
2
Access Control Policy
Dictates how logical and physical access to company systems is provisioned, managed, and revoked
1
Information Security Policy
Ensures company assets and data are appropriately protected from unauthorized access and disclosure


Are You Ready?
Read more
View policy details



Before starting the SOC 2 audit process, it is important that you’re well-prepared to avoid any lengthy delays or unexpected costs.
Pre-audit
How to Start a SOC 2 Audit
Undergo a SOC 2 readiness assessment to identify control gaps that may exist and remediate any issues.
1
Decide which Trust Service Criteria to include in your audit that best align with your customer’s needs.
2
Choose a compliance automation software tool to save time and cost.
Pro Tip - select a licensed CPA firm that also offers compliance automation software for an all-in-one solution and seamless audit process that doesn’t require you to switch vendors mid-audit.
3
During the Initial Stage of the Audit
Review recent changes in organizational activity (personnel, service offerings, tools, etc.).
1
Create a timeline and delegate tasks (compliance automation software will make this activity much less time consuming).
2
Review any prior audits to remediate any past findings.
3
Organize data and gather evidence ahead of fieldwork (preferably with automated evidence collection).
4
Review requests and ask any questions.
Pro Tip - it’s important to choose an experienced auditing firm that’s able to answer questions throughout the entire audit process).
5
Choose a compliance automation software tool to save time and cost.
Pro Tip - select a licensed CPA firm that also offers compliance automation software for an all-in-one solution and seamless audit process that doesn’t require you to switch vendors mid-audit.
Undergo a SOC 2 readiness assessment to identify control gaps that may exist and remediate any issues.
Organize data and gather evidence ahead of fieldwork (preferably with automated evidence collection).
Read more
SOC, which stands for System and Organizational Controls, is a framework developed by the American Institute of Certified Public Accountants (AICPA) for the purpose of providing regular, independent attestation of the controls that a company has implemented to mitigate information-related risk.
There are three types of SOC audits: SOC 1, SOC 2, and SOC 3. When it comes to cybersecurity, SOC 2 has become the
de facto standard.
In a SOC 2 audit, you describe the policies, procedures, and systems you have in place to protect information across five categories called Trust Services Criteria. Your independent auditor evaluates the evidence you supply for the controls in each category, and when completed you receive your official SOC 2 compliance report that you can share with customers and business partners to assure them that their data will be handled securely.
Read More
Read More
Read More
Read More
Find out more
SOC 2 is an extremely popular form of cybersecurity audit, used by a rapidly growing number of organizations to demonstrate they take cybersecurity and privacy seriously.
In a world filled with data breaches and information leaks, establishing trust is not only critical to your revenue stream, but it can be a competitive differentiator when closing new business. Customers and partners seek assurances that the companies they work with are doing everything they can to avoid exposing sensitive information and creating risk. That's exactly why SOC 2 compliance is important.
SOC, which stands for System and Organizational Controls, is a framework developed by the American Institute of Certified Public Accountants (AICPA) for the purpose of providing regular, independent attestation of the controls that a company has implemented to mitigate information-related risk.
There are three types of SOC audits: SOC 1, SOC 2, and SOC 3. When it comes to cybersecurity, SOC 2 has become the
de facto standard.
In a SOC 2 audit, you describe the policies, procedures, and systems you have in place to protect information across five categories called Trust Services Criteria. Your independent auditor evaluates the evidence you supply for the controls in each category, and when completed you receive your official SOC 2 compliance report that you can share with customers and business partners to assure them that their data will be handled securely.