Now that the Department of Defense (DoD) has finalized the Cybersecurity Maturity Model Certification (CMMC) 2.0 framework, businesses within the Defense Industrial Base (DIB) must act swiftly to ensure they are compliant with the updated standards. The 32 CFR rule for CMMC 2.0, which was published in October 2024, introduces a streamlined framework with three control levels designed to safeguard sensitive data including Controlled Unclassified Information (CUI).
Why should you get in line for a CMMC 2.0 assessment now, and what are the risks if you wait? Keep reading to find out.
The urgency of CMMC 2.0 compliance
CMMC 2.0 is a non-negotiable requirement for all entities engaged with the DoD, including prime contractors and their subcontractors. Contractors must obtain CMMC certification under one of the three trust levels to demonstrate that they have adequately implemented cybersecurity measures. For organizations that fall into CMMC Levels 2 and 3, an audit is not just a recommendation — it is a necessity.
The stakes are high. Because CMMC certification will be required to continue working with the DoD, non-compliance could result in a catastrophic loss of business. Delaying action could jeopardize your organization’s ability to secure future contracts and maintain existing ones.
Why you shouldn’t wait to get in line for a CMMC 2.0 assessment
1. Bypass the mad dash to find an available C3PAO.
There are currently less than 60 accredited CMMC Third Party Assessment Organizations (C3PAOs) available to assess the roughly 80,000 organizations that will need certification. As the demand for these assessments increases, it’s likely that C3PAOs will be overwhelmed with audit requests, creating long waitlists and potential delays. If you secure your spot in the assessment queue now, you can avoid the rush and ensure that your organization isn’t left scrambling to find an available assessor.
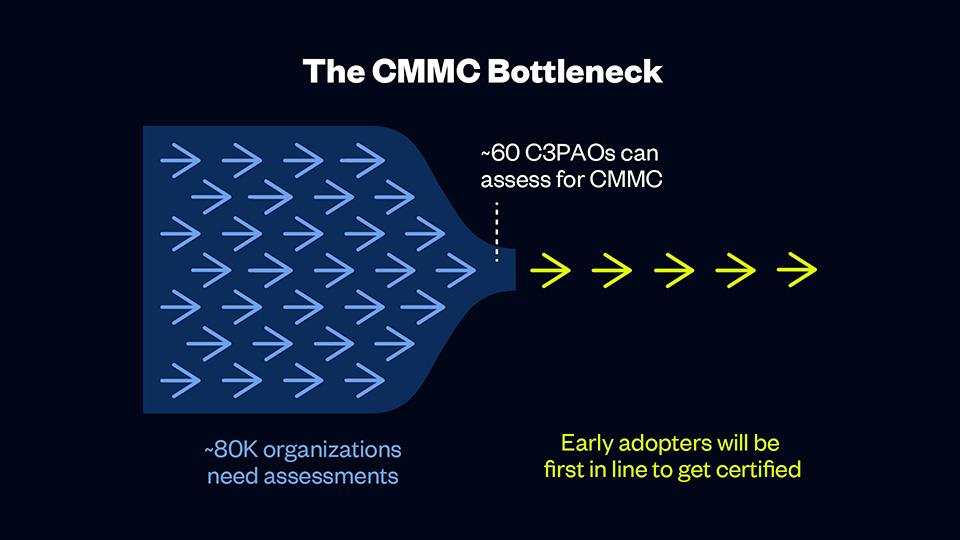
2. Pick the best assessor.
Acting early allows you to choose an experienced, high-quality assessor rather than settling for whoever is available. Working with a seasoned assessor increases the likelihood of a smooth certification process and ensures that your organization’s unique compliance needs are fully addressed. Companies like A-LIGN can provide comprehensive support beyond just CMMC certification, acting as a single provider for all your compliance needs.
3. Lock in a favorable price.
As demand for CMMC assessments rises and the number of available assessors decreases, the ability to negotiate pricing will diminish. By getting ahead of the curve, you can lock in a competitive price for your assessment and avoid the financial strain of last-minute certification efforts.
4. Ensure complete CMMC readiness.
The process of preparing for a CMMC 2.0 audit is complex and time-consuming, potentially taking up to 12 months depending on the current state of your cybersecurity practices. Starting early gives you time to undergo a CMMC readiness assessment. This mock audit allows you to identify and remediate any gaps in your cybersecurity framework before the formal assessment, increasing the chances of passing on the first try.
5. Gain a competitive advantage.
Achieving CMMC 2.0 certification before your competitors not only secures your position within the DoD supply chain but also enhances your reputation as a reliable partner. Prime contractors will likely prioritize subcontractors who have already secured their certification, reducing project risks associated with non-compliance. Early certification can give you the upper hand in winning contracts and retaining existing business.
6. Avoid business disruption and contract losses.
Delaying your certification could lead to significant business disruptions, particularly as CMMC 2.0 becomes a contract requirement. Prime contractors will begin demanding proof of compliance from their subcontractors, and failure to provide this could result in lost contracts or delays in renewals. Acting now minimizes the risk of these disruptions and ensures that your business remains competitive and compliant.
Get in the CMMC queue with a top federal assessor today
The transition to CMMC 2.0 marks a significant shift in the cybersecurity landscape for DoD contractors. Now that the final rule has been published, the time to act is now.
A-LIGN is here to guide you through the complexities of CMMC 2.0 compliance. As one of the first authorized C3PAOs with extensive experience in federal assessments, we can help you navigate the path to certification.
Contact us today to secure your spot in our CMMC certification queue and learn how we can support all your compliance needs.
The rapid growth of artificial intelligence (AI) has brought many privacy, ethical, and security concerns to the forefront of business operations. ISO/IEC 42001 is the world’s first AI management system standard created to address these concerns, providing the necessary guidelines to safeguard AI systems and ensure ethical AI practices. With many organizations new to the world of AI compliance, we developed an ISO 42001 checklist to help you evaluate your organization’s readiness for certification.
Download the ISO 42001 checklist
Why ISO 42001 and AI compliance matters
With the widespread adoption of AI across numerous industries, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) developed ISO 42001 in 2023 to provide guidance to organizations providing, producing, or using AI systems.
Ensuring the ethical and secure deployment of AI solutions is critical, so ISO 42001 can be essential for organizations to ensure there are correct controls in place to safeguard sensitive data.
Achieving ISO 42001 certification and upholding the highest AI security practices can help your business demonstrate trust with key stakeholders, gain a competitive edge in the market, and foster a culture of security within your organization.
Understanding the ISO 42001 readiness checklist
Before you start your ISO 42001 compliance journey, it’s imperative you have a comprehensive understanding of the framework to adequately prepare for certification. From there, your security team can start to determine if the proper controls are in place to adhere to the standard and safeguard data.
Follow the ISO 42001 checklist below to demonstrate your dedication to AI compliance and prepare your team for certification.
Getting started with ISO 42001
The first step on the road to AI compliance is to adequately prepare your team by understanding the critical documents and policy requirements highlighted in the standard.
Understand the standard
Buy the standard(s) from ISO and understand each of the annexes needed to meet the object of the certification:
- Annex A: Serves as a control framework for meeting organizational objectives by addressing AI related risk
- Annex C: Highlights AI related risk sources
Understand critical documents
Gain a well-rounded understanding of the required documents outlined in the standard to build a responsible management system that aligns with your business goals.
- ISO 22989: AI Concepts and Terminology
- ISO 23894: AI Risk Management
- ISO 31000: Enterprise Risk Management
- ISO 42005: AI Impact Assessments
- ISO 5338: AI System Lifecycle Processes
- Others:
- ISO 24368: AI Overview of Ethical and Societal Concerns
- ISO 38500: Governance of IT
- ISO 38507: Governance Implications of the use of AI
Understand policy requirements
Ensure policies are fit for purpose and fit for use in the context of your specific organization and is applicable when needed.
Examples of policy categories include appropriateness, framework for objectives, documentation and accessibility, review and adaptation, and more.
Initial analysis and planning
Once your team understands critical documents and policy requirements, then you can perform an initial analysis of your management system and identify any gaps or corrective actions ahead of the external audit.
Perform a gap analysis
Via self-assessment, independent certification body, or compliance software tool, complete a gap assessment. Make sure to involve various department heads in the analysis to ensure comprehensive coverage.
Develop an implementation plan
Prioritize action items based on the gap analysis findings and assign responsibilities/deadlines for each action item.
Engage with an advisory or consultant partner to ensure your management system is built appropriately in the context of your organization.
Implement management system
Organize training sessions for employees on new processes and controls and set up a monitoring system to track the implementation progress.
Undergo internal audit
Train internal staff to perform audits or hire external auditors for an unbiased review ahead of the official certification.
Conduct management review
Document all management review meetings and decisions for audit purposes, including feedback mechanisms and staff insights on the AI management system.
Identify corrective actions
Develop a standardized form and tracking system for reporting and resolving non-conformities and corrective actions.
Ensure proper documentation
Create, review, and update a centralized repository for all ISO 42001-related documents to ensure ongoing compliance.
Engage with auditors for ISO 42001
Interview and engage a certification body that understands your context to assess and certify your management system so you can offer additional levels of assurance to your customers.
Choose a certification body
Evaluate multiple certification bodies to compare expertise, costs, and reputation and choose a quality audit partner that aligns their goals with yours.
Ensure certification body is compliant with their accreditation body and International Accreditation Forum (IAF) requirements. Check references from other companies certified by the body.
Hold pre-audit meeting
Prepare a list of questions and clarifications regarding the audit process and discuss the scope of the audit in detail to ensure full preparedness.
Ensure audit readiness
Conduct a pre-audit checklist review with the internal team responsible for ISO 42001 compliance. Simulate audit scenarios to prepare staff for the actual audit.
Undergo the external audit process
Designate a team member as the point of contact for auditors to streamline communication. From there, undergo assessment with interviews of key personnel and review of documentation.
Identify follow-up actions
Schedule a meeting to discuss audit findings and plan for immediate, short-term, and long-term actions based on the audit report with your internal team.
Ensure continuous improvement
Establish a continuous improvement team to oversee progress post-certification and integrate ISO 42001 compliance metrics into regular management reviews.
Partner with A-LIGN to achieve ISO 42001 compliance
Obtaining certification and upholding compliance with ISO 42001 is crucial for organizations leveraging AI. By utilizing this readiness checklist and collaborating with quality partner like A-LIGN, organizations can effectively navigate the standard, build brand reputation, and foster trust in your AI systems with key stakeholders.
Be one of the first to achieve ISO 42001 certification and set your team up for ISO 42001 certification success by downloading our readiness checklist now.
Establishing a solid foundation in information security is essential for leveraging artificial intelligence (AI) effectively. ISO/IEC 27001 provides the crucial framework for information security management and sets the groundwork for the new standard for AI, ISO/IEC 42001. By adhering to the principles of ISO 27001, organizations can create robust management systems that not only meet security standards but also pave the way for successful and secure AI implementation. This blog post will explore how ISO 27001 serves as the foundation for ISO 42001, offering a path to compliance.
1. Scope of ISO 27001 and ISO 42001
ISO 27001 focuses on information security management systems (ISMS). It provides a framework to protect sensitive information through risk management processes.
ISO 42001 deals with AI management systems. This standard includes responsibilities specific to AI, such as ethical considerations and impact assessments.
Work required
To align your organization with both standards, build upon your ISMS and create an AIMS. Integrate responsible AI practices to ensure comprehensive scope coverage.
2. Normative references in ISO 27001 and ISO 42001
ISO 27001 references various information security management standards. These guidelines help organizations maintain data integrity, confidentiality, and availability.
ISO 42001 incorporates AI-specific standards, like ISO/IEC 22989. These references focus on ethical AI use, risk management, and system integrity.
Work required
Integrate AI-specific normative references into your compliance framework. Ensure that your organization adheres to both information security and AI-specific standards.
3. Terms and definitions
ISO 27001 includes terms related to information security, such as risk, policy, and controls. These terms are essential for implementing a robust ISMS.
ISO 42001 introduces AI-specific terms, including AI risk, AI policy, and AI objectives. Understanding these terms is crucial for effective AI management.
Work required
Update your organization’s documentation and training materials to include AI-specific terms. This will help employees understand the nuances of both standards.
4. Context of the organization
ISO 27001 requires organizations to understand the context of their information security needs. This involves assessing internal and external factors affecting information security.
ISO 42001 extends this concept to AI. Organizations must understand the specific context of their AI systems, including stakeholder expectations and potential impacts.
Additionally, ISO 42001 requires organizations to understand their role in the AI ecosystem as provider, producer/developer, or user.
Work required
Analyze AI-specific issues and assess stakeholder needs. Document these findings to align with the requirements of both ISO 27001 and ISO 42001.
5. Leadership commitment
ISO 27001 emphasizes leadership commitment to information security policies. Top management must demonstrate their dedication to maintaining a secure environment.
ISO 42001 similarly requires leadership commitment but focuses on AI management. This includes defining roles and responsibilities specific to AI.
Work required
Ensure that your organization’s leadership demonstrates a commitment to both information security and AI policies. Assign roles to manage AI-specific responsibilities effectively.
6. Planning for risks and opportunities
ISO 27001 involves planning to address information security risks and opportunities. This includes risk assessments and treatment plans.
ISO 42001 extends these requirements to include AI risk assessment and impact evaluation. Organizations must identify and mitigate AI-specific risks.
Work required
Implement AI risk and impact assessment processes. Adapt your existing risk management frameworks to include AI-specific considerations.
7. Support resources and competence
ISO 27001 mandates the allocation of resources, competence, and awareness for information security. This ensures effective implementation and maintenance of the ISMS.
ISO 42001 requires similar support for AI management. Organizations must provide resources, training, and communication channels specific to AI.
Work required
Allocate resources for AI management and provide necessary training. Establish communication channels to facilitate information flow regarding AI policies and practices.
8. Operational planning and control
ISO 27001 focuses on operational planning and control for information security. Organizations must have processes in place to manage and monitor security controls.
ISO 42001 extends these requirements to AI systems. This includes planning and controlling AI operations, as well as conducting regular risk and impact assessments.
Work required
Develop operational controls specific to AI systems. Conduct regular assessments to ensure compliance with both ISO 27001 and ISO 42001.
9. Performance evaluation
ISO 27001 requires organizations to monitor, measure, analyze, and evaluate information security performance. This involves regular audits and reviews.
ISO 42001 similarly mandates performance evaluation but with a focus on AI systems. Organizations must establish specific metrics and criteria for AI performance.
Work required
Establish performance metrics for AI systems and conduct regular evaluations and audits. This will help you maintain compliance with both standards.
10. Continual improvement
ISO 27001 emphasizes continual improvement of the ISMS. Organizations must address nonconformities and implement corrective actions.
ISO 42001 also focuses on continual improvement but in the context of AI management. This includes addressing AI-specific nonconformities and applying corrective actions.
Work required
Implement processes for continual improvement of your AI management system. Address nonconformities and apply corrective actions to maintain compliance with ISO 42001 and ISO 27001.
Conclusion
Understanding the overlap between ISO 42001 and ISO 27001 can streamline your compliance efforts. By integrating AI-specific requirements into your existing information security framework, you can ensure comprehensive and efficient management of both systems.
By following the steps outlined in this blog, your organization can stay ahead of the curve with robust security and ethical AI practices. If you need further assistance, experts at A-LIGN can guide you through the compliance process.
Brand reputation is everything in the digital age. Many consumers refuse to do business with brands they don’t trust. One of the sure-fire ways customer trust can be broken? Mishandling or inadequately protecting their data.
It’s no surprise then that corporate compliance teams have become critically important. They identify and mitigate risks for the organization, including risks with direct legal and financial consequences of noncompliance. Additionally, these teams can avoid or minimize the impact of security incidents, safeguarding the brand’s reputation.
Data from A-LIGN’s fourth annual Compliance Benchmark Report shows that establishing customer trust and validating IT controls are increasingly important drivers of compliance programs. Rather than merely checking off the minimum regulatory requirements, companies are building a robust security-focused culture throughout the organization to stay relevant.
In this post, we’ll dig into the data from this year’s report and share how companies can adapt their compliance strategies in response.
What the data says about the “why” behind compliance
A-LIGN’s 2023 survey data showed pressure from above and on the bottom line when it came to the motivations behind compliance. One of the top reasons organizations pursue a cybersecurity audit was a board-level or C-suite mandate (23%), hinting that team members responsible for compliance saw it as a top-down order rather than an ongoing, continuous process within the organization. Another big driver of compliance in 2023 was increasing revenue and winning new clients (23%). This data points to a reactive approach toward compliance, with companies embarking on a new audit when an executive or prospective customer asks for one.
Beyond mandates: A focus on IT controls
In 2024, executive mandates and new business were the least popular responses to the question, “What is the driving force behind your organization’s compliance program?” On the other hand, the importance of establishing trust with customers and partners rose by 36% from the previous year. Additionally, 55% more companies stated that validating IT controls drove their compliance programs in 2024 compared to 2023.
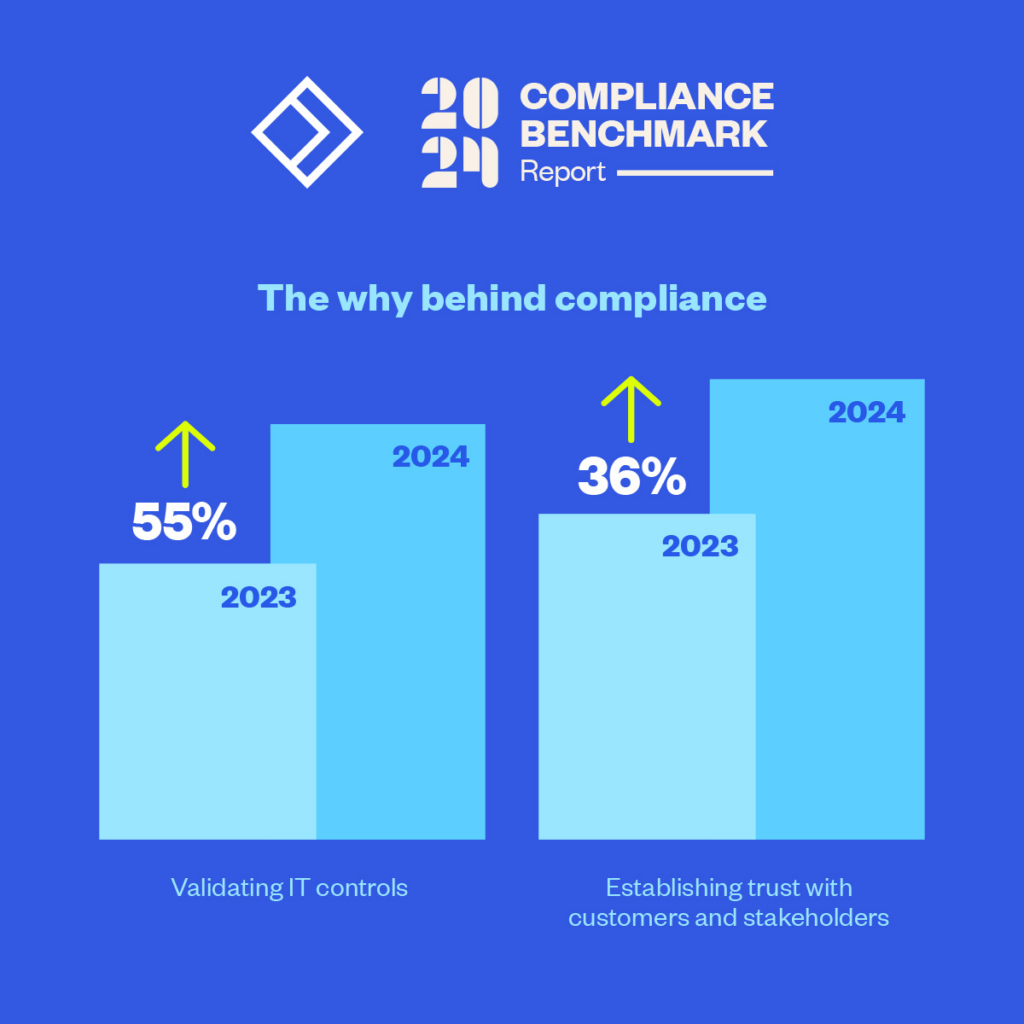
These findings indicate a growing emphasis on trust and security — and an overall maturation in how organizations approach security compliance. Instead of waiting for C-suite mandates to tell them what must be done, compliance teams are taking a more proactive and strategic stance that focuses on what can be done.
Why did this shift occur? As we covered at the beginning of this article, brand reputation is more important than ever. Proactively improving your security posture and publicly sharing your successes can bolster your brand reputation. It’s also possible that businesses have seen — or, worse, experienced themselves — the pitfalls of reactive compliance: lost business, security breaches, and expensive fixes.
How businesses can build a culture of security
As the importance of data security continues to rise, so too will the need for comprehensive and forward-thinking compliance programs. Businesses must prioritize transparency and robust security practices to maintain trust with stakeholders and ensure their internal controls are up to par.
Becoming more proactive toward compliance isn’t easy, but some tweaks to internal processes and attitudes can help get you there. Here are some ways your organization can take steps toward fostering a culture of security.
Regular audits and assessments
- Internal audits and continuous monitoring: Conduct regular internal audits to identify and address vulnerabilities before they come up in external assessments. These periodic internal audits, combined with continuous monitoring of your IT systems, will help you detect and mitigate issues promptly.
- Third-party assessments: Be proactive about engaging third-party auditors instead of waiting until a customer, executive, or investor asks for an audit report. You can also be more strategic about external audits by consolidating all your annual audits into a single compliance event.
A comprehensive compliance strategy
- Leadership commitment and internal collaboration: Leadership should prioritize security and compliance, as they set the tone for the entire organization. The leadership team can then encourage collaboration between IT, legal, compliance, and other departments to create a cohesive approach to security.
- Promote your compliance efforts: When you complete audits and certifications successfully, flaunt them! Celebrate the news internally, and display certifications prominently on your website and in marketing materials to build customer confidence.
Adapting to regulatory changes
- Stay informed: Keep up with changes in regulations, industry standards, and security best practices by subscribing to relevant industry newsletters. Check the websites of governing bodies, like the AICPA Auditing Standards Board (ASB) and the International Organization for Standardization (ISO), regularly for updates. Popular resources for security and compliance news include Infosecurity Magazine, SC Magazine, and Compliance Week.
- Practice agile compliance: Be prepared to adjust your compliance strategies quickly in response to new regulations or emerging threats. If your organization stays sufficiently informed about changes, you can use internal audits and continuous monitoring tools to identify potential gaps and adapt your controls and processes accordingly.
Get more insights in A-LIGN’s Compliance Benchmark Report
What does it really mean to build a culture of security? How many audits are companies doing, and what does that translate to in dollars? The 2024 edition of A-LIGN’s annual Compliance Benchmark Report includes insights like these, gathered from a survey of nearly 700 business leaders and compliance experts. It also offers benchmarks related to compliance audits, enabling companies to assess their existing strategies against industry standards.
See the highlights and download the full report here.
We’ve written before about the importance of balancing audit cost and report quality to ensure the report you get is actually useful to you. In this year’s Compliance Benchmark Report, we asked nearly 700 professionals about their compliance programs and found that companies care about quality, too:
- 69% of survey respondents said the quality of compliance reports is extremely important.
- 22% said report quality was their top reason for choosing an auditor.
But even if you know that quality is important, how can you tell the difference between a thorough audit report and a deficient one? Some auditors may rely on their clients’ lack of compliance knowledge to help them skate by with superficial reports, but you don’t have to be an expert to spot some common red flags.
Here’s what to look out for.
High-level audit report red flags
Here are a few basic factors that should make you think twice while reviewing your audit report:
- Perfect report (no exceptions): Many organizations think a “clean” report with no exceptions is ideal, but that can be a sign that your auditor isn’t being thorough. In a SOC 2 report, for example, it’s possible to receive an unqualified opinion that still contains some exceptions. Exceptions help you understand where you can make changes to improve security. So, if you receive an unqualified opinion with no exceptions, take an extra minute or two to check for some other red flags before you accept the result.
- Vagueness: Are there any specific references to your organization’s security environment? If the report looks like it could have been written about any company, your auditor might be cutting corners to get reports out faster. A vague, cookie-cutter report is a waste of money — you can’t act on it, and customers or partners who read your report may find it inadequate.
- Short report: If it has appropriate and sufficient management controls and respective auditor tests, the report will be long – sometimes 100 pages or more. The length will depend on the report’s scope and the complexity of the controls tested, but you should give a short report a second glance to ensure it is comprehensive.
- Uncooperative auditor. Aside from the report itself, it’s a red flag if your auditor is unwilling to answer questions asked by other auditors or stakeholders about the report. The auditor may be hiding shoddy work or lack of expertise.
Technical red flags
Once you’ve done a quick first read of the report and your auditor’s opinion, review it a second time and keep an eye out for these issues:
- Unclear system scope: The name and scope of the system being audited should be clearly defined — for SOC 2, this should be in sections 1 and 2 of the report. The system description (section 3) should be thorough, addressing all five components of your organization’s internal controls per the COSO framework: control environment, risk assessment, control activities, information and communication, and monitoring activities.
- Undefined subservice organization controls: Most companies use subservice organizations, which the AICPA defines as vendors that “perform some of the services provided to user entities that are likely to be relevant to those user entities’ internal control over financial reporting.” Common examples are third-party IT providers, some SaaS vendors, cloud service providers, or data centers. Any relevant subservice organization controls should be clearly described in the report. The auditor should also cross-reference the subservice organization’s own audit report to verify responsibility for the control lies with that organization and not a fourth-party provider.
- Undefined user entity controls: Similarly, as a service organization, your company likely requires users to take responsibility for some controls to properly and securely use your product or services. These “complementary user entity controls” should be explicitly described in the report in a way that readers of the report will understand.
- Lack of follow-up testing: If exceptions are found, the auditor should inform management personnel at the service organization (in other words, your company’s leadership or compliance/advisory team), record their response, and perform subsequent testing. If none of this is documented in the report where exceptions are found, it does not meet quality standards.
What to do if you find red flags in your audit report
If you’ve noticed several of these red flags in your most recent audit report, you may wonder what to do next. The first step is to reach out to the auditor about your concerns. If they followed compliance best practices correctly, they should be able to answer your questions thoroughly. As we discussed earlier in this post, it’s a bad sign if the auditor refuses to engage with you about the report. A compliance partner acting in good faith should be happy to help you understand the audit report.
In the event that your auditor does not provide sufficient answers, it may be time to look for a new one.
The best way to obtain a high-quality audit report
A-LIGN’s 2024 Compliance Benchmark Report found that a trusted auditor with positive market perception is the top factor companies look for to ensure a high-quality audit report. A reputable auditor should:
- Have a large team of expert auditors
- Have many years of experience in compliance audits
- Be licensed to perform the specific audit you need
- Regularly undergo and pass peer reviews as well as quality reviews by governing bodies (such as HITRUST, the PCI Council, or the ANSI National Accreditation Board)
See how your compliance strategy stacks up
Wondering what other companies look for in an auditor? How many audits are other companies doing each year? How much do they spend on audits? What challenges are compliance teams facing right now? The fourth edition of A-LIGN’s Compliance Benchmark Report uncovered key themes in the world of compliance, including report quality, audit efficiency, a culture of security, and the importance of partnership.
Download the report now to see where your compliance program stands.
In cybersecurity and compliance, one certification stands out as the gold standard for information security management: ISO/IEC 27001. Achieving ISO 27001 certification demonstrates a company’s commitment to protecting its information assets and mitigating cyber risks. But what exactly is the ISO 27001 process, and how can your organization seamlessly attain this certification? Let’s delve into the steps of the ISO 27001 process.
Understanding the ISO 27001 process
The ISO 27001 process is a systematic approach to establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS) within an organization. It involves a series of steps that are carefully crafted to ensure the confidentiality, integrity, and availability of information assets. Here’s a breakdown of the key stages of the ISO 27001 process:
1. Initiation and planning
The journey towards ISO 27001 certification begins with a clear understanding of your organization’s context, scope, and objectives. During this phase, management’s commitment to information security is crucial, as it sets the tone for the entire process. Planning involves defining the ISMS scope, conducting a risk assessment, and establishing information security policies and objectives.
2. Selecting a vendor
Once your organization decides to pursue ISO 27001 certification, it must select a certification body to help navigate the audit process.
It’s important to look for an accredited certification body. To become accredited, organizations must undergo a rigorous evaluation process to ensure that the certification audit is performed in accordance with the ISO 27006 and ISO 17021 requirements. The evaluation process assesses the competence of the audit team, the audit methodology, and the quality control procedures in place to ensure that the audit and report are completed properly.
3. Pre-assessment
The ISO 27001 pre-assessment process is designed for companies that will undergo the certification process for the first time and is only performed on an as-needed basis. Certification bodies will simulate the actual certification audit by performing a review of your company’s entire management system including scope, policies, procedures, and processes to review any gaps that may exist and should be evaluated prior to undergoing the certification process.
The pre-assessment phase can give your organization a head-start on the certification process by revealing any oversights or potential weaknesses that your organization may have ahead of the actual audit so that you can act on areas that require remediation or attention.
4. Stage 1 audit
First, an auditor reviews an organization’s documentation to confirm it is following ISO 27001 requirements. The Stage 1 audit also checks to see if the required activities of the standard have either been completed or are scheduled for completion prior to starting Stage 2.
At the end of Stage 1, the auditor will determine if your company is ready to move forward to Stage 2, or if there are any areas of concern regarding the company’s policies, procedures, and supporting documentation before proceeding. In rare cases where significant areas of concern are noted, you may be required to complete a second Stage 1 audit before moving on to Stage 2.
5. Stage two audit
The Stage 2 audit is performed to test the conformance of the system with the ISO 27001standard. During this stage, the certification body will perform testing procedures including interviews, an inspection of documented evidence, and an observation of processes. Every audit is different in duration, and the time to completion is determined by several factors.
Upon completion of Stage 2, the certification body will determine if your organization is ready to be certified. If there are any major nonconformities, they will need to be remediated before a certificate can be issued. At this point, an organization is issued a certificate valid for three years, contingent on the continued successful completion of surveillance audits.
6. Surveillance audit
Obtaining ISO 27001 certification is not the end of the journey; it marks the beginning of a commitment to maintaining and improving information security practices. Surveillence audits are conducted annually to ensure ongoing compliance with the standard’s requirements.
For the next two years, annual surveillance audits are required to ensure ongoing conformity with the ISO 27001 standard. These audits provide assurance that your systems and processes remain compliant over time. Surveillance audits are shorter in time and scope than the initial Stage 2 audit and test a sampled set of controls. Typically, this process should take a few months to complete each year.
5. Recertification
Your ISO 27001 certificate is valid for three years after the issue date as long as the surveillance requirements are met. However, your organization will need to recertify before the expiration date, which will then restart the three-year certification process.
The recertification process differs from the initial certification, as organizations do not typically need to go through the Stage 1 audit again. Organizations begin recertification with a full system audit, which is similar to a Stage 2 audit. Upon completion of recertification, organizations will undergo further surveillance audits.
The benefits of ISO 27001 certification
Embracing the ISO 27001 process and obtaining certification bring a multitude of benefits to organizations, including:
- Enhanced security posture: By identifying and mitigating information security risks, organizations bolster their defenses against cyber threats.
- Improved customer trust: ISO 27001 certification demonstrates a company’s dedication to safeguarding sensitive information, earning trust from customers and stakeholders.
- Legal and regulatory compliance: Compliance with ISO 27001 helps organizations meet legal and regulatory requirements related to information security.
- Competitive advantage: Certification differentiates organizations in the marketplace, giving them a competitive edge over non-certified competitors.
Partnering with A-LIGN for ISO 27001
Navigating the complex landscape of ISO 27001 certification can be daunting, but with the right partner by your side, the journey can be efficient and seamless. A-LIGN, a trusted global leader in compliance and cybersecurity solutions, offers comprehensive services to support organizations in achieving ISO 27001 certification.
With A-LIGN’s expert guidance, cutting-edge technology, and commitment to quality, companies can embark on their ISO 27001 journey with confidence. From initial assessment to certification audit and beyond, A-LIGN caters to diverse compliance needs, ensuring a smooth and successful certification process.
The ISO 27001 process is not just a certification but a commitment to excellence in information security. By following a structured approach, leveraging expert guidance, and embracing a culture of continuous improvement, organizations can elevate their cybersecurity posture and build a foundation of trust and reliability in today’s digital world.
Are you ready to embark on your ISO 27001 journey? Partner with A-LIGN – contact us today to take the first step towards cybersecurity excellence.
The launch of HITRUST CSF v11.3 represents a significant advancement in healthcare information security frameworks. This latest version not only aligns with current cybersecurity needs but also anticipates future requirements with an emphasis on AI compliance, ensuring organizations are well-equipped to protect sensitive data as the threat landscape continues to evolve.
The key updates of HITRUST CSF v11.3
By addressing the latest regulatory requirements, enhancing protections against sophisticated cyber threats, and streamlining the assessment process, HITRUST CSF v11.3 shows that HITRUST continues to demonstrate its commitment to supporting organizations in their quest for robust data protection and compliance.
1. Integration of authoritative sources
The inclusion of FedRAMP r5, and TX-RAMP into HITRUST CSF v11.3 is a strategic move to standardize the approach towards compliance for entities engaged with government contracts. StateRAMP r5, and TX-RAMP r5 into HITRUST CSF v11.3 is a strategic move to standardize the approach towards compliance for entities engaged with government contracts. The NIST SP 800-53 R5 mapping also underwent slight improvements reflecting updates from NIST SP 800-53 Release 5.1.1, encompassing the addition of one new control (IA-13) and enhancements to three existing controls.
These additions underscore the importance of a unified framework that addresses specific regulatory requirements, facilitating a smoother pathway to compliance for organizations navigating the complex landscape of government information security standards.
2. Enhanced protections with NIST SP 800-172
With cyber threats becoming more sophisticated, the integration of NIST SP 800-172 into the HITRUST framework enhances protections for Controlled Unclassified Information (CUI). This update is particularly beneficial for organizations with high-risk profiles, offering a tailored approach to the HITRUST r2 Assessment that is both rigorous and relevant.
3. Foundation for CMMC Level 3 requirements
Preparing for compliance with the Cybersecurity Maturity Model Certification (CMMC) Level 3 requirements is now more attainable with HITRUST CSF v11.3. This serves as a foundation for organizations to meet stringent NIST standards, positioning them to address future compliance needs effectively.
4. Security for AI systems with MITRE Atlas Mitigations
Acknowledging the growing role of artificial intelligence in today’s technology landscape, HITRUST has included MITRE Adversarial Threat Landscape for Artificial-Intelligence Systems (MITRE Atlas) mitigations. This ensures that security measures keep pace with the advancements of AI.
This transition towards incorporating advanced AI security measures through the inclusion of MITRE Atlas mitigations in HITRUST CSF v11.3 seamlessly complements the HITRUST AI Assurance Program launched in October 2023, further strengthening the framework’s capacity to secure AI-powered systems in the healthcare sector.
5. Streamlined assessment process
Efficiency is at the heart of the updated framework, with a significant reduction in redundancy across requirement statements. This streamlining effort has led to a decrease in the average r2 assessment size, making the certification process more manageable for organizations without compromising on control coverage.
6. Alignment with PCI DSS 4.0
The latest framework update aligns closely with the evolving landscape of cybersecurity and data protection, echoing the robust standards set forth by PCI DSS 4.0. Both frameworks prioritize the security and integrity of sensitive data within organizations, emphasizing comprehensive risk management and compliance measures. HITRUST CSF v11.3’s enhancements integrate elements that mirror the updated requirements of PCI DSS 4.0, ensuring that organizations adhere to stringent guidelines for safeguarding payment card data and other critical information.
Impact on organizations
The updates in HITRUST CSF v11.3 bring about several key impacts for organizations pursuing HITRUST CSF compliance in the evolving threat landscape, including:
- Staying ahead of regulations: Organizations can now remain compliant with the latest industry standards and requirements, addressing current and future regulatory challenges.
- Adapting to the cyber threat landscape: With the inclusion of new authoritative sources and enhanced protections, organizations are better equipped to tackle the dynamic cyber threat environment.
- Efficiency in compliance efforts: The streamlined assessment process reduces the time and effort required for HITRUST Certification, enabling organizations to focus on critical business operations while maintaining high security and compliance standards.
Transitioning to HITRUST CSF v11.3.0
Starting April 16, 2024, the option to generate new e1 and i1 assessment objects, including i1 rapid recertification assessments, using CSF v11.2 in MyCSF has been deactivated. From now on, all new e1, i1, and rapid recertification assessments must be initiated with CSF v11.3. While existing e1 and i1 assessments created with CSF v11.2 remain eligible for submission post April 16, 2024, HITRUST will provide a 90-day notice prior to announcing the submission deadline for e1 and i1 assessments using v11.0.0, v11.0.1, v11.1.0, and v11.2.0. This transition period provides an opportunity for entities to assess their readiness and make necessary adjustments to align with the updated standards.
For organizations navigating these changes, A-LIGN offers diagnostic and gap assessments to bridge the gaps between previous HITRUST versions and v11.3. These services are designed to guide entities through the framework’s intricacies, ensuring a smooth and effective transition.
Learn more about pursuing HITRUST Certification with the latest framework updates by visiting https://www.a-lign.com/service/hitrust.
In July 2023, FedRAMP released the guidance for Cloud Service Providers (CSP) to transition from NIST 800-53 Revision 4 to Revision 5. The FedRAMP Rev 5 transition ranks as one of the biggest changes for CSPs in FedRAMP compliance and requires significant updates to all FedRAMP related processes, controls, and documentation.
For more information on the differences from Rev 4 to Rev 5 see our blog post Understanding the New FedRAMP Rev 5 Baselines.
As CSPs already on the marketplace are beginning to progress through their 2024 Annual Assessments for the first time since Rev 5 became a requirement, our assessors are seeing general pain points emerge for CSPs first assessment against the Rev 5 standard. Below is a summary of key challenges for cloud service providers (CSPs):
Ambiguity in requirements: Not defining parameters appropriately
Challenge: Revised controls in Rev. 5 introduce new parameters and updated requirements. This includes controls that already existed under Rev. 4 with additional requirements and adjustments in language. Their parameters will have to be updated as well. These controls are easy to overlook when focusing on the entirely new controls that Rev. 5 has introduced.
Solution: CSPs should collaborate closely with their security teams, assessors, and compliance officers. Clear communication and documentation are crucial. Detailed guidance on parameter definitions, use cases, and examples can mitigate this challenge. Begin with existing controls that have updated parameters for Rev. 5, then move onto the entirely new controls introduced in Rev. 5.
Privacy controls gap: Lack of incorporation within the framework
Challenge: While Rev. 5 integrates privacy controls throughout the catalog, CSPs may overlook their inclusion. Privacy is now a central theme, but some providers continue to focus solely on traditional security controls, neglecting privacy-related aspects.
Solution: CSPs must actively map their existing controls to the integrated privacy framework. Training and awareness programs can help bridge the gap. Additionally, leveraging tools and templates provided by NIST and FedRAMP can streamline the process.
Incomplete supply chain risk management implementation
Challenge: The new Supply Chain Risk Management (SR) control family demands robust supply chain risk assessments. CSPs, especially those new to the cloud space, grapple with building comprehensive SR plans. Incomplete implementation can jeopardize the security of the entire ecosystem.
Solution: CSPs should establish checks and balances within their supply chains. Collaborate with vendors, assessors, and third parties to ensure thorough risk assessments. Documentation of processes and transparent communication are essential.
Control objective misalignment: New controls falling short
Challenge: Implementing the new controls doesn’t always align perfectly with their intended objectives. CSPs may struggle to fully meet the control goals due to operational constraints or resource limitations.
Solution: CSPs should conduct thorough gap analyses. Identify areas where control objectives are not fully met and prioritize remediation efforts. Regular assessments and continuous improvement are critical.
Red team exercise: Relying on 3PAO penetration tests
Challenge: Control CA-8(2) introduces a new red team exercise requirement. However, some CSPs mistakenly rely solely on the 3PAO FedRAMP guided penetration testing to fulfill this requirement. However, penetration testing and red teaming are two unique exercises.
Solution: While FedRAMP is still finalizing requirements for red teaming, CSPs must recognize that the organization’s red team exercises are essential. They provide context-specific insights and simulate real-world scenarios. A balanced approach, combining both internal and 3PAO assessments, ensures comprehensive security testing. A-LIGN offers independent red team assessments apart from our FedRAMP services that can help management better assess their security posture and meet the requirements of Rev 5.
In summary, the transition to NIST SP 800-53 Rev. 5 demands careful attention to detail, proactive practices, precise implementation statements, and a robust security approach. By addressing these challenges, CSPs can enhance their security posture and successfully navigate the evolving landscape of information security and privacy.
ISO 42001 has sparked significant interest among organizations that currently use – or plan to use – artificial intelligence (AI) in their businesses. As organizations figure out how to leverage AI ethically and effectively, they are looking to this new standard for guidance.
We’ve compiled frequently asked questions about ISO 42001 and consulted industry experts for their insights. Below is a distilled Q&A guide all about implementing ISO 42001.

Watch our on-demand webinar, ISO 42001: The Future of AI Security with Patrick Sullivan, VP of Innovation and Strategy at A-LIGN and Kim Lucy, Director of GRC Standards at Microsoft.
What is ISO 42001 and why is it gaining attention?
ISO 42001 is a standard that outlines the requirements for establishing, implementing, maintaining, and continually improving an AI Management System (AIMS). Its significance stems from the increasing reliance on AI technologies across various sectors and the need to ensure these technologies are developed and used responsibly. ISO 42001 helps organizations align their AI practices with ethical, legal, and technical standards, facilitating trust and safety in AI applications.
Who were the architects behind ISO 42001?
The development of ISO 42001 was a collaborative international effort, involving experts from tech industries, academia, and public sectors. Contributors like those from Microsoft and other leading technology firms played pivotal roles, leveraging their expertise to ensure the standard reflects the latest in AI governance and management practices. This diversity ensures ISO 42001 is broad in scope and applicability, making it relevant across industries and regions.
How does ISO 42001 relate to existing management systems, such as ISO 27001?
While sharing high-level structures with other ISO standards like ISO 27001, ISO 42001 incorporates unique elements specific to AI, such as detailed risk management focused on societal and individual impacts of AI systems. This includes the requirement for AI impact assessments, setting it apart from other standards that may focus more on organizational risks. The inclusion of sector-specific requirements underlines the standard’s focus on the unique challenges posed by AI technologies.
Can adopting ISO 42001 aid in regulatory compliance, like the EU AI Act?
ISO 42001 was designed with an eye towards facilitating compliance with emerging regulations, including the EU AI Act. By aligning its provisions closely with such legislative frameworks, ISO 42001 serves as a valuable tool for organizations navigating the complex landscape of AI regulation. It offers a robust foundation that can help meet current and future legal requirements, positioning organizations favorably in a regulated environment.
Is ISO 42001 applicable to both large corporations and startups?
Yes, one of the strengths of ISO 42001 is its scalability and flexibility, making it suitable for organizations of all sizes, from global corporations to startups. The standard’s applicability regardless of an organization’s size is a testament to its thoughtful design, emphasizing the importance of defining the organization’s context and management system scope effectively. Properly scoped, ISO 42001 can guide any organization towards responsible AI use.
What assessments are mandated by ISO 42001 for AI systems?
ISO 42001 requires organizations to conduct AI impact assessments and AI risk assessments, emphasizing the effects on individuals and society. This approach marks a shift from traditional enterprise risk assessments, directing attention towards the broader implications of AI technologies. These assessments are critical for understanding and mitigating the potential negative impacts of AI systems on society.
How does ISO 42001 enhance trust within the AI supply chain?
By establishing a certification process for responsible AI use, ISO 42001 helps create a trust chain within the AI supply chain. This is particularly crucial in industries where AI components are integral to products, such as medical devices. Certification signifies that an organization has met stringent criteria for responsible AI development and use, providing assurances to partners and consumers alike.
Are there additional resources that complement ISO 42001?
For organizations seeking to thoroughly implement ISO 42001, resources such as ISO 23894 for AI risk management and ISO 42005 for guidance on AI impact assessments are invaluable. These documents provide deeper insights and practical advice on adhering to ISO 42001, offering a more comprehensive understanding of managing AI systems responsibly.
What challenges might organizations encounter with ISO 42001?
Adopting ISO 42001 requires a commitment to deep engagement with the standard’s requirements. Organizations should be prepared for a process that is more involved than simply applying a set of prescriptive measures. Successful implementation necessitates a nuanced analysis and adaptation to the organization’s specific context, goals, and the regulatory environment.
How does ISO 42001 prepare organizations for future AI regulations?
ISO 42001’s close alignment with current regulatory trends, such as the EU AI Act, and its proactive incorporation of AI impact assessments position organizations well for future AI regulations. It serves as a foundational step, enabling organizations to adapt to new legal requirements more seamlessly and ensuring continued responsible AI use.
For businesses considering venturing into AI or seeking to enhance their AI governance, ISO 42001 provides a comprehensive framework that supports ethical, legal, and efficient AI use. By adopting ISO 42001, organizations can better, and more proactively, navigate the challenges of AI implementation, foster innovation, and build trust among stakeholders.
How do I get started with ISO 42001?
With a new framework, it is especially important to have an experienced audit partner on your side. The team at A-LIGN is on the forefront of ISO 42001 certification and has a team of experts ready to help you navigate the audit process and achieve ISO 42001 compliance.