When the International Organization for Standardization (ISO) published a new version of ISO/IEC 27001 in 2022, compliance teams were left wondering: What is the difference between ISO/IEC 27001:2013 and ISO/IEC 27001:2022? As the deadline to transition is quickly approaching, companies need to ensure that the organization’s ISO 27001 certification is updated. Read on to learn the steps your organization should take now to transition to the newest ISO 27001:2022 standard.
What is ISO 27001?
ISO 27001 is the world’s leading information security standard, providing control requirements to create an information security management system (ISMS).
ISO 27001:2022 is a moderate update from the previous version of the standard: ISO 27001:2013. The bulk of changes are related to the Annex controls as the updates focused on revamping and better aligning to industry standards that we see today. The Annex controls have been grouped differently, new Annex controls have been added, and others have been merged or renamed.
Updates to Clauses 4-10
ISO 27001:2022 includes the same number of clauses as ISO 27001:2013, but the text has changed slightly. The changes help align ISO 27001 with other ISO management standards.
Significant changes largely revolve around planning and defining process criteria, as well as monitoring standards. Specifically:
Clause 4.2 Understanding the Needs and Expectations of Interested Parties: A new subclause was added requiring an analysis of which of the interested party requirements are going to be addressed through the ISMS.
Clause 4.4 Information Security Management System: New language was added that requires organizations to identify necessary processes and their interactions within the ISMS. Essentially the ISMS must include the processes underpinning the ISMS, not just the ones specifically called out in the standard.
Clause 6.2 Information Security Objectives and Planning to Achieve Them: Now includes additional guidance on the information security objectives. This gives more clarity about how objectives should be monitored regularly and formally documented.
Clause 6.3 Planning of Changes: This clause was added to set a standard around planning for changes. It states that if changes are needed to the ISMS, they shall be adequately planned for.
Clause 8.1 Operational Planning and Control: Additional guidance was added for operational planning and control. The ISMS now needs to establish criteria for actions identified in Clause 6 and control those actions in accordance with the criteria.
Additional minor changes include:
Clause 5.3 Organizational Roles, Responsibilities, and Authorities: A minor update to the language clarified that communication of roles relevant to information security are to be communicated within the organization.
Clause 7.4 Communication: Subclauses a-c remain the same. But subclauses d (who should communicate) and e (the process by which communication should be affected) have been simplified and combined into a newly renamed subclause d (how to communicate).
Clause 9.2 Internal Audit: This clause was changed, but not materially. It essentially just combined what already existed between Clause 9.2.1 and 9.2.2 into one section.
Clause 9.3 Management Review: A new item was added to clarify that the organization’s management review shall include consideration of any changes to the needs and expectations of interested parties. It’s important to note any changes, as they are instrumental to the scope of the ISMS that’s determined in Clause 4 (and based on those needs and expectations). For example, if an organization’s Board of Directors wants to go public, organizations must consider how the change in priorities would impact the ISMS.
Clause 10 Improvement: Structural changes to this clause now list Continual Improvement (10.1) first, and Nonconformity and Corrective Action (10.2) second.
Changes to Annex A control structure
In ISO 27001:2022 structural changes were made to the Annex A controls. Control groups have been reorganized and the overall number of controls has decreased.
At a high level:
11 new controls were introduced
57 controls were merged
23 controls were renamed
3 controls were removed
In ISO 27001:2013, controls were organized into 14 different domains. In the new update, controls are placed into the following four themes instead:
Organizational controls (37 controls)
People controls (8 controls)
Physical controls (14 controls)
Technological controls (34 controls)
The nomenclature change promotes a better understanding of how Annex A controls help secure information. The previous domain names were written for IT professionals — rather than management. Companies will need to update their Statement of Applicability to match this new structure, as they look to achieve certification under ISO 27001:2022.
Additional attribute values were also added to better describe the Annex A controls and help categorize them, but these are only available in ISO 27002.
New controls within ISO 27001:2022 Annex A
The largest change within Annex A is around the 11 new controls which were introduced. Organizations that are currently certified under ISO 27001:2013 will need to ensure proper processes are in place to meet these new requirements or will need to create new processes to incorporate these controls into their existing ISMS.
Notably “threat intelligence” requires organizations to gather and analyze information about threats, so organizations can take action to mitigate risk. Companies certified under ISO 27001:2013 may not have this element in place. This is a relevant change and speaks to the idea that threats are ever evolving. Therefore, mitigating risk is a continuous process, not a “one-and-done” task. This tracks back to an update in ISO 27002 which was introduced earlier in 2022. ISO 27002 can provide more clarity on this, as it includes additional implementation guidance.
Additional new controls within ISO 27001:2022 include:
A.5.7 Threat Intelligence: This control requires organizations to gather and analyze information about threats, so they can take action to mitigate risk.
A.5.23 Information Security for Use of Cloud Services: This control emphasizes the need for better information security in the cloud and requires organizations to set security standards for cloud services and have processes and procedures specifically for cloud services.
A.5.30 ICT Readiness for Business Continuity: This control requires organizations to ensure information and communication technology can be recovered/used when disruptions occur.
A.7.4 Physical Security Monitoring: This control requires organizations to monitor sensitive physical areas (data centers, production facilities, etc.) to ensure only authorized people can access them — so the organization is aware in the event of a breach.
A.8.9 Configuration Management: This control requires an organization to manage the configuration of its technology, to ensure it remains secure and to avoid unauthorized changes.
A.8.10 Information Deletion: This control requires the deletion of data when it’s no longer required, to avoid leaks of sensitive information and to comply with privacy requirements.
A.8.11 Data Masking: This control requires organizations to use data masking in accordance with the organization’s access control policy to protect sensitive information.
A.8.12 Data Leakage Prevention: This control requires organizations to implement measures to prevent data leakage and disclosure of sensitive information from systems, networks, and other devices.
A.8.16 Monitoring Activities: This control requires organizations to monitor systems for unusual activities and implement appropriate incident response procedures.
A.8.23 Web Filtering: This control requires organizations to manage which websites users access, to protect IT systems.
A.8.28 Secure Coding: This control requires secure coding principles to be established within an organization’s software development process, to reduce security vulnerabilities.
What should I do next?
The new ISO 27001:2022 standard must be fully implemented no later than October 31, 2025. For companies that are still operating under ISO 27001:2013, you will need to transition prior to the deadline to maintain certification.
Don’t panic. Creating a plan of action and moving quickly is essential to preventing a hack of valuable information. Enlist the help of a trusted audit partner to get you back on track. Our team of experts recommend that you:
- Conduct a gap assessment: An audit team can map your existing controls to the newly revised standard and determine what changes your company will need to make to achieve certification under the new version of the standard.
- Implement new controls: Once that assessment is complete, we recommend focusing on implementing new standards that align with ISO 27001:2022.
- Conduct a transition audit: To update your current certification, a transition audit is mandatory to move into the 2022 version. Get ready with our ISO 27001 checklist.
Choosing an auditor that prioritizes a high-quality report can assist with your transition to ISO 27001:2022. Menlo Security enlisted A-LIGN for its transition from ISO 27001:2013 to ISO 27001:2022 and appreciated the team’s attention to detail and responsiveness. “I have extensive experience with auditors, and working with A-LIGN has been refreshing,” said Rashpal Singh, Menlo Security Global Director of Governance, Risk, and Compliance. “I appreciate their approach, communication, proactive team, and how seamlessly audits are conducted with a no-surprises approach.”
Start the process of updating your ISMS to new standards. Contact us today.
As Artificial Intelligence (AI) continues to be adopted on a large scale, organizations are expected to show responsible usage and ensure their systems can be trusted with sensitive information. Our 2025 Compliance Benchmark Report, featuring insights from over 1000 compliance professionals worldwide, shows that 90% of organizations have an AI compliance policy in place or are working on one. This means that most organizations are thinking about the role AI plays within their operations and are working on documenting and training their teams on acceptable use and guidelines.
It’s a transformative tool for businesses, but CISOs and IT teams need to understand the risks and set requirements for responsible adoption. In this article, we’ll go through the risks of AI tools and provide practical tips to mitigate risks.
Key risks of AI tools
While AI offers significant opportunities, it introduces serious risks to data privacy and security. These are the major risks that your organization needs to be aware of:
AI learns from user input
By default, AI chatbots, like Chat GPT or Gemini, use a language learning model (LLM) to train themselves on information that is put into their system. When employees use personal accounts to access AI tools, they could inadvertently be training AI on sensitive client data or intellectual property.
AI reduces control over data
What happens to the data once it’s put into AI systems? Many AI tools, especially free versions, share information with third-party models without explicit consent, increasing the risk of data exposure and loss of control over the information.
AI threatens data privacy
If a user shares client data with an AI tool that doesn’t isolate data or ends up sharing it with a third-party model, the company is at major risk of violating privacy agreements, which can lead to its own set of legal problems.
AI complicates compliance efforts
Use of unregulated AI tools can cause inconsistencies in your organization’s compliance practices. Without policy and procedures to manage which tools are approved, it is easy for the problem to get out of hand quickly, leading to timely and costly overhaul down the road.
How companies can adopt AI responsibly
AI tools have risks, but there are effective strategies to manage them responsibly.
Establish an AI steering committee
Forming a steering committee is the key to guiding responsible AI adoption. A steering committee oversees both the internal and external use of AI tools, creating policies to mitigate the associated risks and educate its users.
The most effective steering committees are formed of stakeholders across the organization, and they work alongside AI initiatives rather than being gatekeepers of them. Including stakeholders from different departments helps drive the adoption of AI and ensures that all users understand how to mitigate the risks when using these tools. They support overall goals while ensuring new AI initiatives comply with regulatory standards. This keeps executives and investors happy and facilitates the strategic integration of AI across the organization.
Create an AI usage policy
It’s important to establish a policy to protect your company from liabilities that can come from using AI. This policy will serve as a guideline for how your company implements AI and ensures responsible usage. It’s also a crucial element for AI frameworks and regulations like ISO 42001 and the EU AI Act. Check out our AI Policy Template to learn the key elements and information to include.
Implement internal governance
Establishing governance around the tools used internally can help bolster AI security efforts. Here are steps you can take to proactively mitigate risks and get control over your company’s AI usage:
- First, get an inventory of all the AI systems that are being used throughout the company. Figure out what these tools are and what they do.
- Next, perform a basic AI impact assessment on each tool. This will help you determine the risks and benefits of each tool so you can decide if it’s worth keeping.
- From there, verify the security controls of each AI tool to determine if the service encrypts and isolates your company’s data from others. In many cases, you will need to purchase corporate licenses to enable security and privacy controls.
- Once you’ve gone through the first three steps, decide which tools will be sanctioned and which will be blocked. It’s highly recommended to establish a white-list only approach to new AI tools, meaning that by default all new AI tools are blocked unless they are requested by stakeholders, have a valid business justification, and undergo a required AI Impact Assessment.
- Finally, you should have an open conversation with the leadership team to get an understanding of which tools people use and value. Always be open to expanding the internal AI toolkit, as long as there is business justification as to why the sanctioned tools can’t be used.
Eventually, as your AI Usage Program matures, you can incorporate data loss prevention (DLP) to monitor the type of data that is being put into these systems. This involves classifying the data and defining what information is sensitive, confidential, and allowed to be inputted into the AI tools. This will allow you to safeguard your data and manage AI adoption at a high level.
Build your security around ISO 42001
ISO 42001 has become the leading standard for AI compliance, with major companies like Microsoft and Google racing towards certification. Even if your company isn’t planning on getting certified just yet, basing your security around ISO 42001 will facilitate faster certification if you start to receive pressure for it. Supply chains are already starting to favor those that have certification beyond just a simple trust document, so aligning with ISO 42001 can help give your organization a competitive advantage.
If you’d like to learn more about AI best practices and implementing ISO 42001, you can contact us here.
Compliance isn’t just a “nice to have,” but a “must have” to do business today. Which framework is top of mind for many organizations? ISO/IEC 27001:2022. This global leading certification is a common way to demonstrate trust, win new business, and drive results. Read on for a guide to your ISO 27001 audit.
What is ISO 27001?
ISO 27001 is an international standard for information security management systems. It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. The standard outlines requirements for establishing, implementing, maintaining, and continuously improving an organization’s ISMS.
Why should you conduct an ISO 27001 audit?
ISO 27001 isn’t a legal requirement but may be a prerequisite to customers doing business with your organization.
Some industries are more likely to need an ISO 27001 certification because of the type of data that companies store. These industries include:
- Information technology
- Healthcare
- Finance
- Consulting
- Telecommunications
Beyond a requirement of doing business, an ISO 27001 certification is a best practice for forward-thinking companies that care about cybersecurity. Successfully completing an ISO 27001 audit demonstrates to customers and other stakeholders that you care about protecting their data. Plus, it gives your organization a competitive advantage over similar vendors who might not have the same standards for data protection.
Preparing for your ISO 27001 audit
The prep work is just as important as the audit when it comes to compliance. Your organization should take the time to understand the standard, define your goals, and research certified third-party assessment organizations. You should also be willing to conduct a gap assessment and understand the state of your company’s compliance journey before jumping into an ISO 27001 audit.
How to select a certification body
Selecting a certification body is one of the most important parts of a successful ISO 27001 audit. This team will be responsible for evaluating and certifying your ISMS, so choosing a partner with experience and certifications is essential to a high-quality audit. Here are some things to consider before selecting a certification body:
- Accreditation: Your certification body must be certified by a recognized accreditation body to conduct an ISO 27001 audit and award your team a certification. For example, two top accreditation bodies include ANAB and UKAS. If your auditor does not have an accreditation, you will not have a valid certification after your ISO 27001 audit.
- Experience: Similarly, picking an experienced team is essential. You’ll be trusting this team to provide a high-quality ISO 27001 audit. Your chosen team should be trained and certified to provide a valuable audit experience.
- Technology-enabled audit process: Choosing an audit partner that uses technology to its fullest extent can help you get the most out of your audit. Technology keeps teams organized, projects on track, and sets your company up for success for future audits.
The ISO 27001 audit process: What to expect
There are several steps to your ISO 27001 audit. Your team should be prepared to identify gaps, work with your audit team, and implement changes based on any recommendations or findings to ensure a smooth process.
Pre-assessment
The ISO 27001 pre-assessment process is designed for companies that will undergo the certification process for the first time and is only performed on an as-needed basis. Organizations such as certification or implementation bodies, will simulate the actual certification audit by performing a review of your company’s entire management system including scope, policies, procedures, and processes to review any gaps that may exist and should be evaluated prior to conducting the ISO 27001 audit.
The pre-assessment phase can give your organization a head-start on the ISO 27001 audit process by revealing any oversights or potential weaknesses that your organization may have ahead of the certification audit so that you can act on areas that require remediation or attention.
Stage 1 audit
First, an auditor reviews an organization’s documentation to confirm it is following ISO 27001 requirements. The Stage 1 audit also checks to see if the required activities of the standard have either been completed or are scheduled for completion prior to starting Stage 2.
At the end of Stage 1, the auditor will determine if your company is ready to move forward to Stage 2 of the ISO 27001 audit process, or if there are any areas of concern regarding your company’s policies, procedures, and supporting documentation before proceeding. In rare cases where significant areas of concern are noted, you may be required to complete a second Stage 1 audit before moving on to Stage 2.
Stage 2 audit
The Stage 2 audit is performed to test the conformance of the system with the ISO 27001 standard. During this stage, the certification body will perform testing procedures including interviews, an inspection of documented evidence, and an observation of processes. Every audit is different in duration, and the time to completion is determined by several factors.
Upon completion of Stage 2, the certification body will determine if your organization is ready to be certified. If there are any major nonconformities, they will need to be remediated before a certificate can be issued. At this point, an organization is issued a certificate valid for three years, contingent on the continued successful completion of surveillance audits.
Surveillance audit
Obtaining ISO 27001 certification is not the end of the journey; it marks the beginning of a commitment to maintaining and improving information security practices. Surveillance audits are conducted annually after your initial ISO 27001 audit to ensure ongoing compliance with the standard’s requirements.
For the next two years, annual surveillance audits are required to ensure ongoing conformity with the ISO 27001 standard. These audits provide assurance that your systems and processes remain compliant over time. Surveillance audits are shorter in time and scope than the initial Stage 2 ISO 27001 audit and test a sampled set of controls. Typically, this process should take a few months to complete each year.
Recertification
Your ISO 27001 certificate is valid for three years after the issue date as long as the surveillance requirements are met. However, your organization will need to recertify before the expiration date, which will then restart the three-year certification process.
The recertification process differs from the initial certification, as organizations do not typically need to go through the Stage 1 audit again. Organizations begin recertification with a full system audit, which is similar to a Stage 2 audit. Upon completion of recertification, organizations will undergo further surveillance audits.
How long does an ISO 27001 audit take?
The duration of an ISO 27001 audit can vary depending on the size and complexity of your organization, the maturity of your information security management system, and your organization’s level of preparedness. Here’s a general overview of the time frame for each stage of the ISO 27001 audit process:
Pre-audit preparation
Before the actual audit begins, organizations typically spend several months preparing and implementing their ISMS. This phase includes conducting a gap analysis, developing and implementing security controls, and performing internal audits. The duration of this preparation phase can range from a few months to over a year, depending on the organization’s readiness and resources.
Stage 1 audit: Documentation review
The Stage 1 audit, also known as the documentation review, usually takes 1-2 days. During this phase, the auditor reviews the ISMS documentation to ensure it meets ISO 27001 requirements. The duration may vary based on the complexity of your ISMS and the thoroughness of your documentation.
Stage 2 audit: On-site assessment
The Stage 2 audit, or on-site assessment, will be dependent on the headcount supporting the ISMS, number of locations, and overall environment complexity. These factors will determine the number of days needed to perform the audit. During this phase, the auditor conducts interviews, examines records, and observes processes to verify that the ISMS is effectively implemented and maintained. The length of the on-site ISO 27001 audit depends on the size of your organization and the scope of the audit.
Post-audit activities
After the walkthrough portion of the audit, the auditor will provide a report detailing their findings. If there are non-conformities, your organization will need to address them within the defined timeline. The time required to resolve non-conformities and complete the follow-up audit can vary, but it generally takes a few weeks to a couple of months, depending on the severity.
The time it takes to complete an ISO 27001 audit will vary based on the size of your organization, how established your ISMS is, and the availability of your audit team.
Get started with your ISO 27001 audit
Navigating the ISO 27001 audit process can be challenging, but with proper preparation and commitment, your organization can achieve certification and reap the benefits of enhanced information security. By demonstrating your dedication to protecting sensitive data, you can build trust with customers, comply with legal requirements, and gain a competitive edge in the market. Contact us today to get started on your compliance journey.
More than 90% of organizations conduct at least two audits or assessments each year, and for larger organizations, that number continues to grow, according to A-LIGN’s 2025 Compliance Benchmark Report.
These days, compliance teams at large companies are spending their time tackling compliance challenges one by one, rather than developing a comprehensive strategy. This disjointed approach wastes time and money as duplicative audits and endless audit cycles strain compliance teams’ resources.
Enter audit harmonization: a premium service designed by A-LIGN’s industry experts to maximize efficiency and provide high-quality audits to enterprise organizations with three or more frameworks to consolidate. Throughout the process, A-LIGN will identify and consolidate overlapping requirements from audits across various vendors to reduce the complexity and burden on your internal resources.
Read on to learn how this strategy can alleviate the burden of your audit cycle.
What is audit harmonization?
Audit harmonization is a white-glove service for enterprises juggling multiple frameworks. Audit harmonization, at its core, is a service in which subject matter experts evaluate your current audit cycles and assessments and develop a plan that will streamline the process.
A-LIGN’s unique approach involves a three-step process to create a custom plan for your company that understands your goals, identifies overlapping requirements, and streamlines your efforts for an effective, high-quality audit. Our approach allows you to scale up to a robust suite of services. Enterprise customers can expect a dedicated team of highly experienced auditors who will support you throughout your compliance journey.
Why audit harmonization?
A-LIGN’s 2025 Benchmark Report found that the #1 challenge of the audit process for enterprise organizations is complexity in conducting multiple audits. These organizations are frequently conducting six or more audits per year to address their diverse compliance requirements and risk profiles. That puts some teams in a never-ending audit cycle. Audit harmonization consolidates the requirements where synergies can be achieved in both fieldwork and evidence collection, and keeps your team focused on the business, not the audits.
Beyond the time spent in audit cycles, enterprise organizations are also investing significant money on compliance. Large organizations in particular are making increased investments. The 2025 A-LIGN Compliance Benchmark Report found that 71% of enterprise companies spend over $100,000 on audits each year, whereas only 19% of small companies and 42% of medium companies say the same. Audit harmonization helps these businesses use a strategic approach for their cycles, reducing the number of duplicate tasks and saving money in the process.
Who is audit harmonization for?
A-LIGN designed the audit harmonization program with enterprise companies in mind. This service is best suited for large companies with three or more frameworks to adhere to.
Who will execute my audit harmonization process?
Your audit harmonization process will be led by a dedicated team who will offer tailored guidance to help you feel prepared and confident. This team will create a strong partnership focused on ongoing success and features A-LIGN’s expert team of auditors, including our leadership, to ensure you continuously receive the highest quality, white-glove service.
How does it work?
There are three steps to A-LIGN’s unique audit harmonization service: analyze, customize, harmonize. This process, handled by a dedicated team, ensures that your business and compliance goals remain top of mind throughout the audit cycle.
Here’s how it works:
Analyze: First is the discovery phase, where our team aims to understand the way your business operates, your organization’s objectives and the role of compliance in those objectives. A-LIGN identifies areas that may impact the audit scope, such as changes to the business, locations, headcount, processes, IT, software, and infrastructure.
Our information-gathering session results in a report that outlines the roadmap for your company’s audit. We’ll also determine the best time of year to conduct audits, recommendations, and provide a summary proposal.
Customize: After analyzing your existing program, our team presents recommendations and potential savings that can be realized in a master audit plan. This visual plan will:
- Identify audits with overlapping requirements to achieve synergies in fieldwork and evidence collection
- Recommend methods for strengthening your controls environment
Our subject matter experts will work closely with your team to deliver a strategy that is best fit for your team. After sharing our own recommendations, we’ll collaborate and adjust the plan as needed to ensure a customized path forward.
Harmonize: In accordance with your master audit plan, A-LIGN auditors review evidence, test it against the necessary compliance frameworks, and deliver a comprehensive final report upon conclusion of testing. Throughout the process, our team minimizes the amount of effort required and ensures you receive the highest quality audit.
During the process, you can expect to hear from your dedicated team regularly to ensure all plans are being upheld. The A-LIGN team will issue a final report and any follow-up items after completing field work. In addition, we will schedule annual business reviews to benchmark current projects against business objectives, to ensure you are successful in your compliance journey.
How to get started with audit harmonization
Interested in understanding how your company can benefit from audit harmonization? Contact us today to learn more.
Tampa, Fla. – Jan. 28, 2025 – A-LIGN, the leading provider in cybersecurity compliance, launched its fifth annual Compliance Benchmark Report. This year’s report features insights from more than 1,000 global respondents across diverse industries, making it one of the most robust perspectives on compliance priorities, challenges, and best practices available.
“A-LIGN’s 2025 Compliance Benchmark Report uncovers crucial insights into the evolving priorities and challenges facing compliance teams today, from AI compliance to growing audit complexities,” said Scott Price, CEO of A-LIGN. “The findings align with our mission to deliver high-quality audits that not only meet regulatory and market needs, but also build trust with customers and mitigate risk. This year’s report demonstrates the importance of A-LIGN’s unique ability to help our customers seamlessly manage their audit cycles with a single provider.”
Findings from the 2025 Compliance Benchmark Report highlight four key themes among respondents:
Audit quality reigns supreme
Companies continue to prioritize a high-quality audit above all. According to this year’s report, 70% of respondents say audit report quality is extremely important, with technical rigor driving this choice.
The most important factors for a high-quality audit include the number of controls tested (36%) and length of report (26%).
Artificial intelligence compliance is surging
A staggering 90% of respondents have an AI compliance policy or are working on one. Plus, many companies are taking things a step further with 76% of respondents planning to pursue an AI audit or certification in the next two years.
SOC 2 is not enough
According to our survey, SOC 2 has shifted from a competitive differentiator to a baseline expectation. Most organizations now recognize that they need additional frameworks and certifications to satisfy client and regulatory expectations. 92% of organizations conduct two or more audits and 58% conduct four or more.
Audit complexity is growing
This year’s report found that enterprise organizations are more than twice as likely (35% vs. 15%) as their smaller counterparts to conduct six or more audits per year.
As businesses grow, so does the complexity of their compliance needs. Growing companies are looking for solutions to manage the demands of modern compliance, driving demand for services like audit consolidation and harmonization
To download the full report and for more information about A-LIGN, visit www.a-lign.com.
About A-LIGN
A-LIGN is the leading provider of high-quality, efficient cybersecurity compliance programs. Combining experienced auditors and audit management technology, A-LIGN provides the widest breadth and depth of services including SOC 2, ISO 27001, HITRUST, FedRAMP, CMMC and penetration testing. A-LIGN is the number one issuer of SOC 2 and a leading HITRUST and FedRAMP assessor. To learn more, visit a-lign.com.
As AI governance grows in importance, many organizations are planning for compliance. Our 2025 Compliance Benchmark Report, which gathered insights from over 1000 compliance professionals across various industries, found that 76% of organizations plan to pursue AI compliance soon with a framework like ISO 42001. Although ISO 42001 isn’t yet the definitive standard due to the dynamic nature of AI governance, it offers a comprehensive solution, providing clear guidelines and best practices for AI compliance. By proactively implementing ISO 42001 with an Artificial Intelligence Management System (AIMS), organizations can streamline AI workflows, accountability, decision-making, and risk management.
Let’s explore the benefits of implementing ISO 42001 this year.
How does ISO 42001 bring value to businesses?
ISO 42001 drives innovation by providing clear processes for managing risks and documentation, helping teams balance creativity with accountability. It also includes performance monitoring and stakeholder alignment to ensure AI systems meet their goals. By embedding risk management and continuous monitoring throughout the AI lifecycle, ISO 42001 helps identify and mitigate risks early, keeping systems efficient, relevant, and cost-effective.
Check out our article Understanding ISO 42001 to get a comprehensive overview of the new AI standard.
The benefits of early adoption
While waiting to implement an AIMS until regulations and market demands become clearer may seem logical, it actually creates greater risk. Early adoption of ISO 42001 is crucial for staying ahead of new regulations and market expectations. This standard helps organizations align with compliance requirements, build stakeholder trust, and improve operational efficiency. By adopting ISO 42001 early, organizations can mitigate risks, avoid costly delays, and position themselves as leaders in AI governance, driving innovation and competitiveness.
Let’s dive deeper into these benefits.
Stay ahead of AI regulations
Governments and industry bodies are rapidly introducing new AI-related requirements. The EU AI Act now mandates risk management, transparency, and monitoring for high-risk systems. US states are creating laws to mitigate AI risks, while countries like Singapore and China are establishing ethical AI guidelines. ISO 42001 provides a unified framework to adapt to these new regulations while allowing organizations to maintain control over their AI systems. Its focus on trust, transparency, and resilience in AI systems goes well beyond meeting regulatory minimums, making it a highly viable standard.
Build trust and transparency
Customers, investors, and partners are expecting AI systems to be fair, reliable, and secure. An AIMS built on ISO 42001 demonstrates trust and accountability through clear communication (Clause 7.4) and transparency (Clause 7.5), building confidence in AI systems and fostering stronger stakeholder relationships.
Minimize financial risks
Delaying AI governance can lead to higher costs, with consequences like noncompliance fines, missed market opportunities, rushed implementations, and governance gaps. Early adoption of ISO 42001 allows organizations to protect themselves from penalties and gain a competitive edge as certifications become necessary. Additionally, by acting now, organizations can allocate the necessary time and resources to build an effective AIMS and complete audits properly.
Boost operational efficiency
An effective AIMS ensures AI systems operate ethically, predictably, and effectively. ISO 42001 enhances efficiency by identifying and mitigating risks, improving data quality, and enhancing oversight. Its lifecycle monitoring and stakeholder collaboration boost performance and trust, while its structured risk management minimizes disruptions. It’s adaptable to various organizational sizes and AI maturity levels, allowing it to align with innovation goals.
Strengthen AI governance
As regulations and market expectations evolve, it’s crucial for organizations to adopt a framework that supports continuous improvement. ISO 42001 integrates seamlessly with standards like ISO 27001 and ISO 27701, creating a unified governance framework for diverse compliance needs. This combined approach enhances data security, ensures traceable data inputs and outputs, and addresses privacy risks, strengthening the AI governance and operational efficiency.
Building your AIMS now with ISO 42001 ensures readiness for current regulations and future changes, reducing the need for reactive overhauls.
Debunking common myths
When considering ISO 42001, organizations often worry about its feasibility, necessity, and impact on operations. We’re here to address these concerns and show how ISO 42001 can be a strategic advantage rather than a burden.
Myth 1: ISO 42001 is too resource-intensive
A common concern is that ISO 42001 is too resource-intensive, especially for smaller organizations with limited budgets or staffing. However, ISO 42001 is designed to be adaptable, allowing incremental implementation, focusing first on high-impact areas. The resources invested in building a governance framework are minimal compared to the costs of regulatory penalties, lawsuits, or reputational damage from mismanaged AI systems. By embedding lifecycle monitoring and risk management early, organizations can achieve long-term savings and proactively avoid costly complications.
Myth 2: Existing compliance makes ISO 42001 redundant
Some organizations believe existing regulatory compliance efforts like GDPR, NIS2, and DORA, make additional standards like ISO 42001 unnecessary. In reality, ISO 42001 complements these efforts by creating a unified framework that aligns diverse compliance requirements, streamlining implementation. This holistic approach ensures organizations not only meet regulatory minimums but also build trust, transparency, and resilience in their AI systems. ISO 42001 helps organizations adapt to new requirements rather than reacting shortsightedly.
Myth 3: ISO 42001 will hinder innovation
There’s a misconception that ISO 42001 will slow down AI development with bureaucratic hurdles. In reality, it’s an innovation enabler. ISO 42001 provides the structure needed to innovate responsibly, ensuring accountability, trust, and scalability. Its flexibility and scalability adapt to organizations of all sizes and AI maturity levels, allowing teams to align quickly with innovation goals. It provides structured risk management and lifecycle monitoring, preventing disruptions from unexpected risks or ethical issues. By building trust with stakeholders, ISO 42001 gives organizations a competitive edge, speeding up the adoption of AI solutions.
Steps for ISO 42001 implementation in 2025
- Understand ISO 42001 and the regulatory landscape. Start by researching current and upcoming AI-related regulations like the EU AI Act, US state legislation, and global standards. It’s important to understand how these regulations impact your business and how ISO 42001 can help you comply. This ensures your AI systems are aligned with legal requirements and ready for future changes.
- Determine your scope and develop an implementation plan. Conduct a gap analysis to identify discrepancies between your existing AI governance framework and ISO 42001 requirements. Develop a step-by-step implementation roadmap to address these gaps, prioritizing areas that will have the greatest impact on your business. This streamlines the transition to ISO 42001 compliance.
- Define your desired outcomes. Utilize ISO 42001 to clearly define the desired outcomes for your AI systems. Align these with business objectives to ensure governance efforts directly support strategic goals.
- Communicate your commitment to responsible AI with stakeholders. Engage with customers, investors, and partners to communicate your commitment to responsible AI governance. Use Clause 7.4 (Communication) and 7.5 (Documented Information) of ISO 42001 to ensure transparency and traceability.
A-LIGN is at the forefront of ISO 42001 certification and has a team of experts ready to help you navigate the audit process and achieve ISO 42001 compliance. Reach out to us today to get started with ISO 42001 certification for 2025.
The CMMC Assessment Process (CAP) is the official guide used by C3PAOs (CMMC Third-Party Assessment Organizations) to conduct a CMMC Level 2 certification assessment. C3PAOs use the CAP to make sure the assessment maintains consistency and integrity when an Organization Seeking Certification (OSC) goes through the process of getting certified.
The Cyber AB recently released the official CAP guide for CMMC Level 2 assessments, so we’re here to break down what you need to know.
What is the purpose of the CAP?
The CAP is the procedural guide for C3PAOs conducting a CMMC Level 2 certification assessment. It’s used to ensure the consistency and integrity of CMMC assessments, ensuring C3PAOs and their CMMC Certified Assessors (CCAs) meet Cyber AB requirements.
While the CAP outlines the process to try to standardize all CMMC assessments, not all C3PAOs are created equal. Check out the CMMC Buyer’s Guide to learn more about choosing a C3PAO and get a list of questions to ask as you’re making your selection.
The four phases of the CAP
The CMMC assessment process consists of four phases that cover the steps before, during, and after the actual assessment:
- Phase 1: Conduct the pre-assessment
- Phase 2: Assess conformity to security requirements
- Phase 3: Complete and report assessment results
- Phase 4: Issue certificate and close out POA&M
Phase 1: Conduct the pre-assessment
The pre-assessment phase validates that organizations are prepared for the CMMC Level 2 assessment. This phase ensures that all the required documents, evidence, and resources are in place before starting the formal assessment. The C3PAO will review the System Security Plan (SSP), confirm the scope of the assessment, and assemble the assessment team. The C3PAO will then complete the Pre-Assessment Form, documenting key information such as the organization’s CAGE code, SSP title, contact details, and readiness determination. The goal is to make sure that the organization is fully ready for the assessment.
Phase 2: Assess conformity to security requirements
In this phase, the CMMC Level 2 assessment takes place, and the implementation of security requirements is evaluated. At the beginning of this phase, the lead CCA will facilitate an “in-brief” meeting, which is a kick-off meeting to align on assessment scope, procedures, and schedule. Then, the real work begins. The C3PAO assessment team will review implementation of security requirements and conduct assessment scoring. Throughout this process, the assessment team will meet every day with the organization to monitor progress, address challenges, and maintain quality and consistency. The goal of this phase is to verify that the organization meets the assessment objectives.
Phase 3: Complete and report assessment results
This phase focuses on finalizing and documenting the assessment results. A formal quality assurance review takes place by a CCA outside of the assessment team to check the accuracy and completeness of the results, which are then presented to the organization before being submitted into the CMMC system. This is also when the “out-brief” meeting occurs, where the lead CCA and assessment team present the assessment results briefing.
Phase 4: Issue certificate and close out POA&M
The fourth phase involves the final steps of the certification process. This is when the organization receives the official CMMC Level 2 certificate. In the case that the organization received a conditional certificate, they will need to address and close out any remaining Plan of Action and Milestones (POA&M) items. Once these items are closed out, the organization will be reassessed by a C3PAO to receive full CMMC Level 2 certification.
Getting certified in 2025
Understanding the four phases of the CAP will help ensure a smooth path to certification. At A-LIGN, we specialize in guiding organizations through this process. As an accredited C3PAO with over 1000 federal assessments completed, we are dedicated to being your partner in achieving and maintaining compliance.
Contact us today to secure your spot in our CMMC certification queue and learn how we can support all your compliance needs.
As new guidance is released and more organizations begin their journey to become CMMC certified, it’s important to understand the certification process and how it will impact your company. Read on to learn what the guidance means for you, what to look for in a C3PAO, and prepare for your assessment. Follow along and download the guide here.
What is CMMC?
CMMC stands for Cybersecurity Maturity Model Certification. The program requires all DoD defense contractors to meet cybersecurity controls and be certified by a C3PAO assessment.
CMMC 2.0 will be mandatory for all entities doing business with the DoD at any level who store, transmit, or process information that meets the standards for FCI or CUI. Prime contractors and their subcontractors will be required to meet one of the three CMMC trust levels and demonstrate that cybersecurity has been sufficiently implemented through the completion of independent validation activities. The initial award or continuance of a DoD contract will be dependent upon CMMC compliance.
Contractors will only be permitted to receive or share DoD information related to programs and projects if they have completed the CMMC process. At the time that a contractor’s contract is up for renewal, they must be CMMC compliant.
Defining the CMMC journey
To simplify the CMMC process, we’ve developed a five-step journey that will take your organization from understanding through certification and beyond.
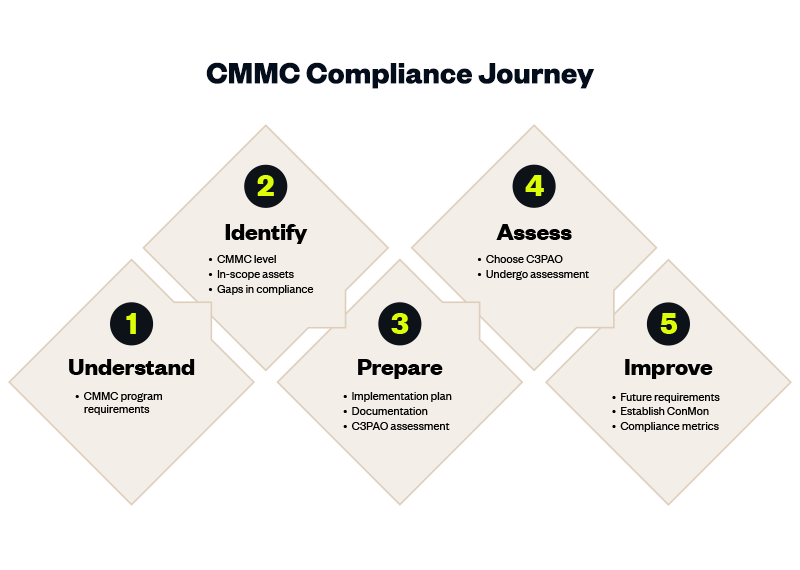
Understand
Read the CMMC final rule, understand program requirements, review DoD’s resources, and familiarize yourself with the practices outlined in the model for each of the CMMC levels.
Identify
First, you’ll need to identify your CMMC level. Later in this guide, we provide an overview of the levels so you can determine which is most applicable to your organization.
Based on your level, you must identify the assets in scope for your CMMC assessment. Refer to the Scoping Guidance from DoD for levels 1-3.
As a part of this step, you should also complete a gap assessment to identify any areas where there are gaps in your compliance.
Prepare
To prepare for the assessment, we recommend developing an implementation plan addressing any vulnerabilities found in the gap assessment to ensure compliance to the CMMC standard.
Complete the necessary documentation to outline your organization’s compliance with the CMMC standard including policies and procedures, and your System Security Plan.
Prepare for the C3PAO assessment by gathering all evidence needed and preparing for the interview questions that will be a part of your assessment.
A helpful way to ensure you’re prepared is to have a C3PAO perform a mock audit against applicable CMMC practices.
Assess
Now, for level 2 and 3 organizations, your C3PAO will complete the CMMC assessment for certification.
Following the CyberAB’s CMMC Assessment Process, the C3PAO will review your documentation and complete interviews with your team before putting together the final report.
If you’ve done the appropriate pre-work, gap assessments, and mock assessments, your team should be well prepared for this step in the process.
Improve
After receiving your certification, the work continues. Plan for continuous improvement and ensure you understand the next steps for future assessments.
Perform annual self-assessments attesting to meeting the CMMC practices for your categorization level.
Assessing your needs
Now that you understand the steps of the CMMC journey, it’s crucial to evaluate your organization’s readiness and preparation to set a clear roadmap.
Start by familiarizing yourself with the different CMMC levels and identifying where your organization stands. This is part of the “Identify” step.
If necessary, consider a partner to help you prepare for the assessment. Later in this guide, we outline the types of CMMC partners available so you can make the best decision for your organization’s needs. Download our CMMC Buyer’s Guide to follow along.
Explaining the CMMC levels
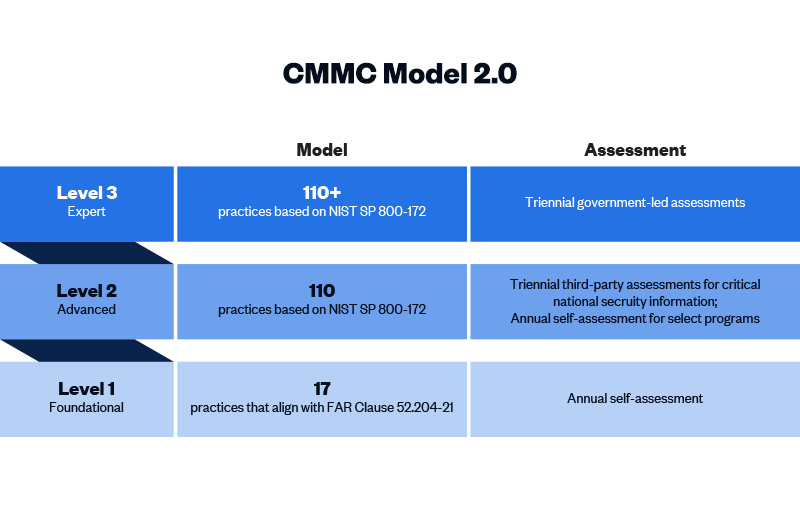
CMMC 2.0 Level 1 (“Foundational”) requirements
Level 1 contractors handle Federal Contract Information (FCI) but not CUI. One of the more significant changes from CMMC 1.0 to 2.0 is that Level 1 is now a self-assessment only, placing this responsibility on the organization itself. Level 1 includes the same 15 controls outlined in Federal Acquisition Regulation (FAR) 52.204-21.
CMMC 2.0 Level 2 (“Advanced”) requirements
Level 2 contractors are those that handle CUI. Processes at this level are maintained and followed, and there is a comprehensive knowledge of cyber assets. The DoD has pared down the 130 practices in the original CMMC Level 3 baseline to the 110 practices outlined in the National Institute of Standards and Technology (NIST) Special Publication 800-171. “Critical” handlers of CUI will need a third-party assessment by a CMMC Third Party Assessment Organization (C3PAO) for CMMC certification every three years. Level 2 processes must be documented and managed to protect CUI.
CMMC 2.0 Level 3 (“Expert”) requirements
Level 3 is for organizations with the highest-priority programs with CUI. The processes involved at this level include continuous improvement across the enterprise and defensive responses performed at machine speed. This level will replace what was formally known as CMMC Level 5. Level 3 will add additional requirements pulled from NIST 800-172 in addition to the Level 2 requirements. It is expected that organizations will be required to be assessed by the DoD directly every three years for Level 3 requirements.
Preparation and readiness
Once you understand your CMMC level, preparation for the assessment can begin. Many organizations seek assistance with preparation and readiness before taking the final step of the assessment for certification with a C3PAO.
There are different types of partner organizations that can help you prepare for CMMC.
MSSPs and consulting firms
Managed Security Services Providers (MSSPs) and consulting firms can assist with program development, policy and procedure development, implementation, and ongoing CMMC management.
RPs & RPOs
Registered Practitioner Organizations (RPOs) provide CMMC guidance and support to Organizations Seeking Certification in the DIB. Registered Practitioner (RP) is a certification for an individual who can provide CMMC guidance, advice, and support. Many MSPs/MSSPs are also RPOs.
GRC partners
Governance, Risk & Compliance (GRC) partners help organizations conduct risk assessments, develop and enforce cybersecurity policies, and provide continuous monitoring. GRC platforms can streamline and automate the preparation process and ensure ongoing compliance.
Selecting a C3PAO
What is a C3PAO?
The Cyber AB authorizes a CMMC Third Party Assessment Organization (C3PAO) to contract and manage CMMC assessments. Only authorized C3PAOs can conduct CMMC assessments.
Currently, ~60 C3PAOs can assess CMMC and more than 80,000 organizations need assessments. That means early adopters will have their pick of C3PAOs and will be first in line to receive certification.
A C3PAO will be an essential partner in your CMMC journey, so you must choose an organization that meets your needs. Although the Cyber AB authorizes all C3PAOs, each organization has different strengths and weaknesses.
Factors to consider when choosing a C3PAO
Expertise
Above all, you want to choose a C3PAO experienced in federal compliance, such as FedRAMP, NIST, and StateRAMP. Their deep understanding of the CMMC and NIST 800-171 frameworks ensures they can guide you through the necessary controls and requirements, helping you avoid common pitfalls and ensuring a smoother path to certification. You should consider how long the C3PAO has been in business, the experience of its employees, and its overall knowledge of cybersecurity compliance.
Quality
Not all assessment teams and final audit reports are created equal. While some organizations check the box, others go above and beyond to ensure quality at every step. High-quality C3PAOs bring extensive experience and a deep understanding of CMMC requirements, which helps identify and address potential compliance issues effectively. This reduces the risk of failing the assessment and ensures that your organization meets all necessary standards. Additionally, a quality C3PAO provides detailed feedback, helping you improve your cybersecurity posture and maintain compliance over time.
Efficiency
Efficiency directly impacts the time and resources required to achieve certification. The CMMC process can be cumbersome to navigate, but some C3PAOs offer technology to help streamline the process. This accelerates the certification process and minimizes disruptions to your operations. Additionally, efficient assessors help ensure that your organization remains aligned with CMMC requirements without incurring unnecessary costs. To further increase efficiency, consider a firm who can tackle additional frameworks such as SOC 2, ISO 27001, and more.
Timing
We expect to see CMMC as a requirement in DoD contracts in early 2026, meaning organizations must give themselves ample time to prepare for and complete the assessment. Because CMMC is a new rule, most organizations will need months to prepare the necessary compliance and documentation. Organizations will need 6-12 months of preparation before beginning the assessment. When choosing a C3PAO, timing should be a key consideration, so be sure to ask how soon you can get started and find out your place in the assessment queue.
Budget
While some affected organizations are used to budgeting for compliance, CMMC also covers businesses that may not have a compliance program or budget. Budget is an important consideration, but as with most things, you get what you pay for. Beware of budget C3PAOs that are offering assessments for under-market value. When looking at the budget, you should balance it with other factors that are important to you. Are you willing to pay more to expedite your timeline? Is the C3PAO you choose known for quality? Is it worth it to spend more to work with a trusted auditor instead of a brand-new firm?
Case Study: Network Coverage
Network Coverage is a managed service provider (MSP) that integrates technology and cloud solutions within business operations to improve productivity and security with as few issues and disruptions as possible. Network Coverage has been proactive in addressing the compliance needs of DoD subcontractors. Anticipating the impact of CMMC and the need for an assessor with federal compliance expertise, Network Coverage adapted from NIST 800-171 to CMMC 2.0 and engaged a reputable C3PAO for their federal compliance expertise.
A-LIGN’s skilled auditors and responsive team have been instrumental in preparing for CMMC compliance, validating Network Coverage’s control set formally, and enhancing its marketability as a reputable MSP. Network Coverage found A-LIGN’s visibility into control crossover among multiple frameworks, such as SOC 2 and ISO 27001, to be a significant time saver. Network Coverage emphasizes planning, budgeting, and continuous monitoring for CMMC readiness, advising subcontractors to review contracts, conduct needs assessments, and prepare for third-party certification, leveraging A-LIGN’s expertise to streamline the process.
“We’re seeing urgency around CMMC that we’ve never seen before. Contractors taking the wait-and-see approach need to have these conversations now. If they’re not having the conversations, now is the time to start.”
-Bridget Wilson, SVP Governance Risk & Compliance
Checklist: Questions to ask a C3PAO
Selecting a C3PAO is a vital step of the CMMC assessment process. It will significantly impact the assessment experience and your final report. This checklist outlines key questions to ask a C3PAO to ensure you’re choosing the best fit for your needs.
- What is your experience with CMMC/NIS 800-171 assessments?
- How many CMMC Certified Assessors (CCAs) and (CMMC Certified Professionals) CCPs do you have?
- Are your CCAs and CCPs full-time employees or contractors?
- Does your team have experience with other federal assessments?
- How many federal clients do you have?
- How many federal audits and assessments have you completed?
- Does your organization conduct assessments beyond CMMC?
- What other federal or non-federal assessments/attestations/certifications does your organization provide?
- What efficiencies can we gain by consolidating our audits with a single provider?
- What can I expect in the assessment process?
- What is your team’s standard response time?
- Do you utilize technology that drives efficiency and streamlines the audit process?
- How much will my CMMC assessment cost?
- What are your rates, and what do they include?
- What is the timeline for assessment?
- What is the lead time to begin the assessment?
- How long do you anticipate the assessment process will take?
- Do you have references and case studies from satisfied customers?
Ready to take the next step? Download the guide or contact us to learn more.
The responsibility of implementing and tracking the use of artificial intelligence at any company is growing more important every day as AI usage increases. In fact, in a survey from McKinsey, 65% of respondents say their organizations are regularly using generative AI in at least one business function, nearly doubling the survey’s last results.
Interested in developing an AI policy for your company? Read on to learn why it’s important and how to get started. Download the template to follow along.
Why is an AI policy important?
Beyond serving as a marker to progress with the trends—like 44% of companies who already have an AI policy in place, according to Litter—AI policies also protect your company from potential lawsuits and liabilities. Using AI-based technologies can put sensitive data at risk or inadvertently cause copyright infringement if not used properly. Plus, these policies are a crucial element for AI frameworks and regulations like ISO 42001 and the EU AI Act.
Who needs an AI policy?
Deciding whether your company needs an AI policy doesn’t have to be complicated. Consider whether your company fits into one of these groups:
- Your company or employees are using AI to some degree in their day-to-day
- Your company is developing technologies that use AI
- Your company needs to adhere to frameworks and regulations like ISO 42001 and the EU AI Act
What should an AI policy include?
Cover your bases. If you’ve developed company-wide policies before, you might have a framework in mind. Regardless, keep these key elements top of mind:
- The purpose and scope of the policy
- Alignment with company goals
- Process for deviations
- Risk management
- Monitoring and reporting
- External communication and transparency
Your company’s AI policy should be personalized to your company’s current and future usage of AI. Not every policy will look the same. Plus, this isn’t an exhaustive list. You might want to include monitoring and reporting information or required trainings for your company.
How can I get started?
For more, download this AI policy template developed by A-LIGN’s expert auditors to help you get started.