A-LIGN’s New Ransomware Preparedness Assessment
Cybersecurity should never be an afterthought. Prepare your organization for the threat of ransomware with A-LIGN’s new Ransomware Preparedness Assessment.
With ransomware attacks on the rise, it’s crucial that your organization is prepared. A-LIGN’s Ransomware Preparedness Assessment puts an effective strategy in place to help prevent attacks and mitigate the potential damage if an attack occurs.
Cybersecurity threats aren’t new to organizations, but over the past year, one threat rose above the others: ransomware attacks. Though most malicious actors will seek out organizations that could have the greatest payout (or, in the case of the Colonial Pipeline attack, wreak the greatest havoc), it’s more likely that attackers look for known weaknesses they can easily exploit.
The reality is that ransomware is a growing threat. In fact, the ransomware global attack volume increased by 151% for the first six months of 2021 compared to the first six months of 2020.
And here are a few other sobering statistics from Sophos’ “The State of Ransomware 2021” report:
- 54% of organizations that were hit by ransomware in the last year said the cybercriminals succeeded in encrypting their data.
- On average, only 65% of the encrypted data was restored after the ransom was paid; only 8% of the surveyed organizations got all their data back.
- The average bill for rectifying a ransomware attack (which includes: The downtime, people time, device cost, network cost, lost opportunity, and ransom paid) is $1.85 million.
When it comes to cybersecurity preparedness, it’s not about “if” but “when” an incident will occur. And the world is starting to accept this as truth.
In fact, following the Colonial Pipeline incident in May 2021, President Joe Biden signed an Executive Order that introduced efforts to improve the nation’s cybersecurity. And many cybersecurity leaders recognize the value of a third-party risk management strategy that pulls best practices from NIST and ISO standards to perform regular audits and plan for third-party incident response.
But organizations need to do more than create plans. They need to consistently test those plans to ensure the people and processes in place function as they should.
A-LIGN’s Ransomware Preparedness Assessment
To help organizations ensure they are ready when a cybersecurity incident occurs, A-LIGN released the Ransomware Preparedness Assessment. The assessment provides organizations with a holistic strategy to evaluate preparedness for a potential ransomware attack. This is done through a three-phased approach that includes three distinct phases: Discovery & Maturity Assessment, Technical Assessment, and Recovery Capability Assessment.
The Discovery & Maturity Assessment
Phase one of A-LIGN’s Ransomware Preparedness Assessment, the Discovery & Maturity Assessment, includes two focus areas. The first is to gain a better understanding of the current environment and threat landscape within a company. A-LIGN does this by conducting discovery workshops to help identify potential areas of improvement in the company’s cybersecurity posture.
The Discovery & Maturity Assessment leans heavily on the methodology outlined through the NIST Cybersecurity Framework (CSF). The CSF evaluates an organization’s capabilities across five categories: Identify, Protect, Detect, Respond, and Recover.
Categories and NIST CSF Descriptions:
Identify
Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Protect
Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
Detect
Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
Respond
Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
Recover
Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
The second piece of the Discovery & Maturity Assessment is the Architecture Review. The purpose is to understand the company’s enterprise-wide architecture to identify where there are — or could be — vulnerabilities. A-LIGN does this through a series of workshops with relevant stakeholders to review current IT architecture, network segmentation, and any existing strategic plans for improvement of the architecture.
IT Security Tier Classification and Level Descriptions:
(based on NIST Security Maturity Levels)
Following the review, A-LIGN provides the organization with a Maturity Assessment report that identifies the organization’s ability to achieve various cybersecurity risk management practices. A-LIGN does this by assigning the company a Tier Classification that ranges from Level 1 to Level 4.
Level 1: Partial Implementation
- Cybersecurity risk management policies exist, though they are often reactive instead of proactive.
- There may be unreliable participation in the risk management program or there may be undefined areas in the policies where additional guidance to refine the policy is required.
Level 2: Risk Informed
- Cybersecurity risk management policies are likely approved and documented, though likely not consistently implemented throughout the organization.
- There is an awareness of cybersecurity efforts throughout the organization, and procedures may clearly define the IT security responsibilities and expectations across various roles, but there are likely informal methods used to mitigate risk.
Level 3: Repeatable
- Procedures are clearly defined and recognized as corporate policy. These guidelines are then communicated to individuals who are required to follow them.
- IT security procedures and controls are implemented in a consistent manner everywhere that the procedure applies and are reinforced through training.
- Procedures clarify where the procedure is to be performed, how the procedure is to be performed, when the procedure is to be performed, who is to perform the procedure, and on what the procedure is to be performed.
Level 4: Adaptive
- Policies, procedures, implementations, and tests are continually reviewed and improvements are made.
- Tests are routinely conducted to evaluate the adequacy and effectiveness of all implementations.
- Tests ensure that all policies, procedures, and controls are acting as intended, and they ensure the appropriate IT security level.
- Effective corrective actions are taken to address identified weaknesses, including those identified as a result of potential or actual IT security incidents or through IT security alerts issued by FedCIRC, vendors, and other trusted sources.
- A comprehensive IT security program is an integral part of the culture.
The Technical Assessment
The second phase of the Ransomware Preparedness Assessment is the Technical Assessment phase which includes Penetration Testing and Social Engineering, both designed to help organizations recognize that the human element plays a very significant role in cybersecurity risk.
Penetration Testing focuses on testing a company’s external and internal defense systems to assess its ability to effectively detect and respond to a malicious actor. This is done through the execution of internal, external, and web applicational penetration tests, as applicable, that simulate a real-world attack against the defense systems.
For Social Engineering, A-LIGN conducts a series of campaigns in an attempt to compromise the credentials of both privileged and non-privileged users to gain access to information systems. This could include phishing, spear phishing, pretexting, or vishing, among a variety of other options, and is based on the desired scope of the organization.
For both types of tests, A-LIGN works closely with the company to understand how they want to be tested based on their specific areas of concern and priorities. In addition, A-LIGN ensures they outline the rules of engagement before the test starts.
Following the completion of the Technical Assessment, the company will receive a Penetration Test report as well as a Social Engineering report that includes a summary of the tasks completed, the results, and the recommended actions that will enable the company to be in a more secure position.
The Recovery Capability Assessment
The final phase of the Ransomware Preparedness Assessment is the Recovery Capability Assessment phase which includes a review of the Business Continuity and Disaster Recovery (BCDR) Plans for an organization and a table-top exercise. During the BCDR plan review, A-LIGN will compare the company’s existing plan against industry best practices to identify potential gaps and areas of improvement.
The final component of the Recovery Capability Assessment phase is a unique table-top exercise that effectively tests team capabilities and the team’s ability to respond to a specific event. The goal of this exercise is to simulate a real-world scenario to assess the company’s capabilities to respond to any event that impacts the business.
This full-day workshop can include a variety of stakeholders from the organization, including the C-Suite (and specifically the CISO), business continuity manager, human resources, legal/compliance, and even steering committees.
Throughout the entire workshop, A-LIGN documents what needs to be fixed or adjusted in the BCDR Plan to ensure the organization is ready to efficiently and effectively respond to these events.
Is A-LIGN’s Ransomware Preparedness Assessment Right for My Business?
A-LIGN’s Ransomware Preparedness Assessment is designed for any organization that either wants to test its preparedness for the risk of a cybersecurity event or to determine if its planned response to a cybersecurity event is efficient.
A-LIGN will work with your organization to understand what the goals and intentions are for the use of the assessment to design a clear and well-defined scope.
The Additional Benefits
Undergoing A-LIGN’s Ransomware Preparedness Assessment is one of the most strategic cybersecurity actions an organization can take. Not only can many of the steps conducted as part of the Ransomware Preparedness Assessment be repurposed to help you meet other compliance requirements, but the insights provided around the gaps that exist across the organization inform the Enterprise Risk Management (ERM) strategy. There’s an affinity between business strategy and ERM. By keeping these closely aligned, it creates a stronger and more strategic organization.
Taking a proactive approach to assessing your readiness for cybersecurity threats shows your clients and customers that you take cybersecurity threats seriously and are taking the steps necessary to protect the data and information of your organization and that of your customers.
Mind the Gap
The growing cybersecurity threat landscape has made cybersecurity a requirement for organizations of all sizes and across every industry. The hard truth is that it’s not about if, but when a cybersecurity event will happen, and the financial and reputational harm is very real.
When an event does happen, you want your organization to be prepared to not only recognize it early on, but to have an effective strategy in place to respond to the event and mitigate the associated risks. This includes recognizing where gaps exist in your cybersecurity strategy, including the significant risk associated with your employees.
The Ransomware Preparedness Assessment from A-LIGN ensures your company is ready for an event when it happens.
Can ISO 27701 guarantee GDPR compliance? ISO 27701 can well position any organization for future GDPR compliance. While one is a management system and the other is a technically a legal framework, ISO 27701 helps to create a path on your journey to GDPR.
In 2019, the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) introduced ISO/IEC 27701:2019 (more commonly referred to as ISO 27701). This was done to provide organisations with an additional component to stack on top of ISO/IEC 27001:2013 (referred to as ISO 27001). But the availability of the combined adoption of ISO 27001 and 27701 raised a lot of questions in the privacy community. The biggest question: will the combination of ISO 27001 and ISO 27701 equate to GDPR compliance?
In short, the answer is “no,” but it can help you along the way toward GDPR compliance. ISO 27001 and ISO 27701 together offer a way for organisations to bolster information security management systems and become certified in a privacy standard. And though it’s a solid foundation for organisations working on fulfilling GDPR requirements, ISO 27001 and ISO 27701 don’t cover all aspects of the GDPR.
What is ISO 27001 and ISO 27701?
ISO 27001 is a longstanding cybersecurity framework that is used to build an information security management system (ISMS) within an organisation. The security standard was published by the International Organization for Standardization and the International Electrotechnical Commission in 2005, later to be revised in 2013 and expansion of ISO 27701 was published in 2019.
ISO 27701 was created as an additional component to complement ISO 27001 that introduced more privacy-specific controls. With ISO 27701, organisations can create a Privacy Information Management System (PIMS) and become certified in certain privacy practices. ISO 27701 was created in large part to provide guidance for complying with privacy regulations being introduced across the world, such as the GDPR (General Data Protection Regulation) and the CCPA (the California Consumer Privacy Act).
However, ISO 27701 is not a standalone standard. Rather, the original ISO 27001 information security management system standard serves as a foundational chassis, and organisations can add on additional standards, such as ISO 27701, that work well for the specifics of their business. By combining ISO 27701 and ISO 27001, organisations can build trust, prepare for privacy regulations, and more. In addition, many of the elements of ISO 27701 map directly back to aspects of the GDPR.
What is GDPR?
GDPR is a privacy and security regulation that was put into effect worldwide in May 2018. It imposes privacy and security standards on organisations anywhere in the world that intentionally target and process personal data of individuals located in the Union.
GDPR repealed and replaced the former Data Protection Directive (Directive 95/46/EC) and is based on the key principles outlined below:
- Lawfulness, Fairness and Transparency: Data is obtained lawfully, under valid grounds, and not in violation of any other laws. Organisations must be open and honest with individuals about how they plan to use their data, and it cannot be used in a way that is detrimental or misleading to any individuals.
- Purpose Limitation: Data is collected for a specific and legitimate purpose.
- Data Minimisation: Organisations should not collect more personal information than they need from data subjects.
- Accuracy: Every reasonable step must be taken to erase or rectify data that is inaccurate or incomplete. Individuals have the right to request that inaccurate or incomplete data be erased or rectified within 30 days. Worth noting, this time period can be extended to 60 days if the controller provides notice to the data subject, or if the request is cumbersome.
- Storage Limitation: Data is kept only as long as necessary for the purpose in which it is processed.
- Integrity and Confidentiality (Security): Appropriate security measures must be in place to ensure information isn’t accessed by hackers or accidentally breached.
- Accountability: Controllers and processors of the data can demonstrate compliance with all of the principles above. This specific principle is new to EU data protection standards.
How does ISO 27701 relate to GDPR compliance?
Knowing what we know of ISO 27701 and the GDPR, it’s easy to see how ISO 27701 could be confused as meeting GDPR compliance — especially when you consider how closely the controls tie back to the articles of GDPR.
The difference, however, is that ISO 27701 is a management system and not a regulation. A management system is essentially an outline for an organisation, and it falls on the organisation to follow and adapt the system in a way that makes sense. Management systems are intentionally vague and can’t be used interchangeably with a regulation like the GDPR. By achieving ISO 27701 certification, organisations can cover a lot of pieces from GDPR, but it’s impossible to fully correlate a standard and a regulation. Noteworthy- regulations that apply to the organisation are listed throughout the audit.
Another fundamental difference between GDPR and ISO 27701 is the ability to carve out your ISO 27701 scope to certain aspects of your business. You can implement ISO 27701’s management system to a particular department or service, for example, the software you provide to clients.
While ISO 27701 does not equal GDPR compliance, it’s a good start.
ISO 27701 helps organizations start the GDPR journey
Once the management system is in place throughout your organisation, it’s possible to expand on that management system to achieve GDPR compliance — with the proper advisory and consulting services.
For organisations seeking an internationally recognised framework, the ISO standards can provide a certification that is scalable to your needs. And in the absence of an official certification for GDPR (which is not yet available), ISO certification can demonstrate your organisation’s commitment to privacy and the maturity of your privacy posture.
With our experience in assessing organisation’s cybersecurity, compliance, and privacy, A-LIGN can provide your organisation with the experience and guidance needed to achieve an ISO certification.
The U.S.-based SOC 2 standard is starting to catch on in European businesses as well as other parts of the world. Although it’s a voluntary American standard, SOC 2 helps to raise cybersecurity maturity and increase business value.
While researching the latest trends and best practices in cybersecurity compliance, you may have seen increasing reference to the SOC 2 (System and Organization Controls) framework.
SOC 2 examinations were designed by the American Institute of Certified Public Accountants (AICPA) to help organisations ensure the protection of their data and the privacy of their client’s information. A SOC 2 assessment focuses on an organisation’s security controls that are related to overall services, operations, and cybersecurity compliance. SOC 2 examinations can be completed for many organisations of various sizes and across different sectors.
Although SOC 2 is typically a customer-driven compliance standard published by an American regulatory body, we are seeing a growing number of European organisations undergoing SOC 2 assessments. To help you determine if SOC 2 is right for your business, let’s examine why SOC 2 has started to catch on in Europe and the benefits it brings to non-American companies.
Why are SOC 2 assessments becoming more popular in Europe?
The rising use of SOC 2 in the U.S. over the past decade is largely due to the fact that many large companies wanted to be more proactive about their cybersecurity risk management. These organisations began setting forth requirements stipulating that their vendors must have a SOC 2 report ready as part of the due diligence process.
Over the past two years, a similar chain of events has started to play out in Europe: Increasingly, companies in certain key industry sectors want to review SOC 2 reports so they can determine that organisations along the supply chain have the necessary controls in place to protect the data of all parties involved.
There are three primary sectors in Europe (especially within the UK) where there is an increasing demand for SOC 2: banking, insurance, and, most recently, central government. It makes sense that these sectors are some of the first to promote a more wide-ranging approach to cybersecurity compliance since they are among the most regulated fields in the world.
The rise in popularity of SOC 2 in the U.S., and now, increasingly, in Europe and other parts of the world, has undeniably been driven by the widespread adoption of cloud computing. According to Flexera’s 2021 State of the Cloud Report, 97% of global organisations use at least one public cloud service such as Amazon Web Services.
Let’s explore two key benefits of leveraging SOC 2.
Moving from ISO 27001 to SOC 2
Right now, International Information Security Standard 27001 (ISO 27001) serves as the principal cybersecurity standard for much of the world, and is particularly favoured in Europe. However, we are noticing that an increasing number of European companies are embracing SOC 2 in addition to ISO 27001 to demonstrate a higher level of cybersecurity maturity. SOC 2 is even replacing ISO 27001 outright in some vendor contracts.
ISO 27001 certification is carried out against a strict controls framework that must be applied to the organisation, regardless of the size or sector, and the audit is pass/fail. With a SOC 2 report, the organisation gets to pick the categories of controls that are tested across five Trust Services Criteria (TSC): Security (required), Availability, Confidentiality, Processing Integrity, and Privacy. Ultimately, the independent assessor’s detailed SOC 2 report contains their expert opinion of how well the organisation meets the selected TSC to protect all aspects of its systems.
The SOC 2 report is more in-depth than an ISO 27001 pass/fail approach. In fact, the end result of a SOC 2 assessment (an extensive attestation report up to 100+ pages in length) tends to give a company’s partners and clients a higher level of assurance about their security posture compared to the end result of an ISO 27001 audit (a one-page certification letter). This is one of the leading reasons why the cybersecurity compliance norm in Europe is beginning to shift.
The SOC 2 historical lookback window
SOC 2 assessments can be carried out in one of two ways:
- A SOC 2 Type I assessment attests to the design and implementation of controls at a single point in time. The assessor reviews evidence from systems in their current state and produces a Type I report. This is not dissimilar to an ISO 27001 audit.
- A SOC 2 Type II assessment attests to the design, implementation, and operating effectiveness of controls over a period of time, usually between 3 and 12 months. In a Type II assessment, the assessor provides assurance that controls are not only designed and implemented, but that they have also operated effectively and as intended over the defined period.
The SOC 2 Type II report shows whether or not an organisation has historically been adhering to the controls they have in place. While a SOC 2 Type II assessment does take longer to complete, it offers an extra layer of trust to a potential customer or partner. A Type II report essentially says, “we didn’t have to scramble to reach this point. We’ve been taking cybersecurity seriously for some time now.”
Other benefits of a SOC 2 report
In addition to helping build trust with prospects, customers, and partners, there are other significant business benefits that a European organisation can unlock with SOC 2 compliance. Let’s take a look at a few of the biggest perks that should be considered.
A more competitive position
Possessing a SOC 2 report can give your European business a competitive edge over other organisations operating in your space. Not only can this help you increase revenue by closing more deals, but it can also help retain clients who may have otherwise explored a different company with proof of a more mature cybersecurity posture.
The ability to expand into the U.S.
As an American cybersecurity framework, SOC 2 adoption has become widespread in the U.S. over the past 10 years. SOC 2 is, in essence, required to do business with most large or well-known U.S.-based companies, even though it is voluntary and not required by law. In much of the same way that GDPR compliance (which is a law) has become key for American companies looking to sell in Europe, SOC 2 is now a unique selling point for European companies that want to expand into the U.S.
Future-proofing the business
The truth is that we are only going to see SOC 2 become more prevalent in Europe over the coming years. In addition to the three sectors mentioned above, the manufacturing and logistics sectors are starting to support SOC 2, especially in the UK. The assessment is also gaining traction in other parts of the world. Australia’s Consumer Data Right (CDR), for example, was introduced to the country’s banking sector in July 2020, and is now being gradually rolled out across other sectors, including the telecommunications and energy sectors. The Australian government has acknowledged that SOC 2 reports can be used as a means to achieve CDR accreditation.
Does your business need SOC 2?
So, does your business need SOC 2? The short answer is that, if your clients are starting to ask for it, or if you are planning to expand in the U.S., then you should begin planning for SOC 2 without delay. However, even if that’s not the case for your business, you would be well-advised to initiate conversations with stakeholders in your organisation to discuss how SOC 2 could help facilitate future growth.
The best way to begin your SOC 2 is to reach out to a reputable, licensed CPA firm in the U.S. This will help you acquire a clearer understanding of where you need to start and what changes need to be made, as well as potential timelines. To make the entire process as efficient and convenient as possible, it’s also wise to choose a firm that has personnel operating in a European time zone, such as in the UK.
If you’re interested in pursuing SOC 2, now or in the future, A-LIGN is here to help. We were the first-ever licensed CPA firm to focus on IT audits such as SOC 2, and we have clients in over 30 countries and on six continents.
An Exciting New Chapter for A-LIGN as We Welcome Warburg Pincus
It’s no secret that the cybersecurity compliance industry is in the middle of a big shift.
The demand for trusted, high-quality cyber assessments is skyrocketing, and organizations everywhere are looking for easier, more efficient ways to complete their audit cycles and leverage the process for increased security value at the same time. The opportunity for new ideas and innovation in the compliance industry is at an all-time high.
That’s why today I’m so excited to announce the next phase of our growth, as we welcome the team at Warburg Pincus on our journey. A-LIGN has always been at the forefront of cybersecurity compliance, relentlessly seeking ways to make audits and assessments more efficient while maintaining a high level of quality. The impact that the right strategic partner can have on a business like ours is undeniable. We experienced it over the last few years with FTV Capital – who remains an investor going forward – and we are fortunate to have Warburg Pincus at the table with us now.
Together, we will continue to innovate and meet the needs of this dynamic market by putting forward a bold vision for A-LIGN over the next few years. We will:
- Become the premier one-stop provider for fully integrated compliance solutions, from pre-audit readiness to final report.
- Extend A-SCEND’s software capabilities to help organizations simplify their audits through automation and consolidation.
- Expand our portfolio of cybersecurity assessments and services, including SOC 2, ISO 27001, HITRUST, FedRAMP, CMMC, penetration testing, privacy, and more.
- Reach more clients across the globe with the same customer-first approach that has always been at the core of A-LIGN’s recipe for success.
To our clients and partners: we are looking forward to finding new ways to help you navigate the complexities of cybersecurity compliance. This relationship will allow us to do even more for you, delivering new technologies and accelerating the value we can bring to your operations. Rest assured; we’ll continue to be committed to your success, providing the same services at the same level of excellence as we always have.
And finally, to our employees, or CLIMBERS as we call ourselves: I’m honored to work alongside you and proud of what we have accomplished together. I know you are all in on this adventure, and I appreciate the commitment you make every day to our clients and our team.
Let’s go climb together – the next mountain awaits!
Corporate Compliance Programs: Purpose and Benefits Explained
Is everyone in your organization on the same page? Our latest Compliance Benchmark Report uncovered the disparity between what boards and regulations require versus how internal teams perceive the strategy behind corporate compliance programs.
When helping organizations launch or refine their cybersecurity compliance programs, one of the first questions we ask is, “What is the primary purpose or driving force behind your corporate compliance program?”
In some industries, such as healthcare, financial services, and government contracting, cybersecurity compliance is a legal requirement, which means yearly audits are simply a reality of doing business in a carefully regulated space. But for industries where compliance is not a legal necessity, motivations can range from satisfying internal stakeholders to building trust with customers, prospects, and partners.
In our 2021 Compliance Benchmark Report, we asked more than 200 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs. We learned that even though the main impetus for compliance can vary, the one common thread is that organizations often pursue compliance audits to win new business.
Let’s take a closer look at some of the drivers for corporate compliance programs and the potential reasoning behind the distribution of responses.
The Purpose of Compliance is Subjective
We asked respondents to rank the primary drivers of their organization’s compliance program from a list of common motives. Interestingly, there was no clear-cut leading cause; answers for the “most important” driver were evenly distributed. Top responses included regulatory requirements (19%), meeting board-level mandates (16%), and establishing trust with potential and existing customers (15%).
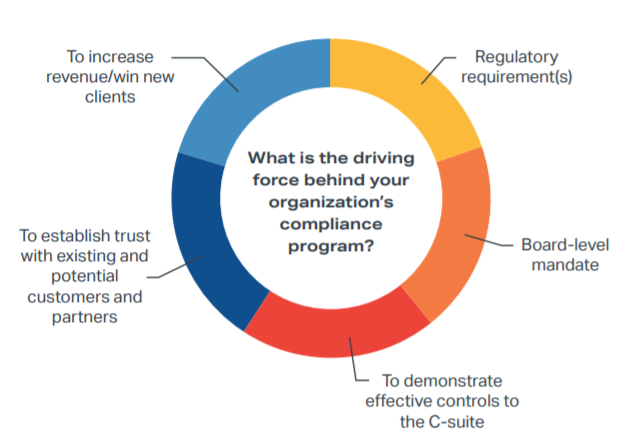
If you evaluate this data at face value, it’s easy to draw the conclusion that the key drivers of compliance are divided evenly and are, therefore, equally important. However, it’s worth noting that the audience for this survey encompassed different departments and job titles. It’s possible that employees serving in different functions and at various levels of an organization have unique perceptions about what is really driving these projects.
For example, an IT QA analyst may receive information about their role in an upcoming compliance project and assume it is being driven by a new law or regulation. At the same time, an executive who oversees the compliance program creation at a high level might view it as an effort to retain clients that could leave in favor of a company with a stronger cybersecurity posture.
In other words, members of an organization may not always be on the same page about the primary driver of their compliance programs.
Winning New Business Is Often a Major Benefit of Compliance
While our survey didn’t identify a clear leading cause for compliance programs, it did highlight a frequent benefit that organizations receive from conducting audits and assessments regardless of the motivation: winning new business. In fact, our survey data showed that 64% of respondents conducted an audit or assessment with the specific goal of winning new business. To that point, 14% of respondents said they lost a business deal because they were missing a certain compliance certification.
This data is indicative of the way many organizations approach audits and assessments: in a reactive manner. We often find that cybersecurity compliance audits and assessments come onto an organization’s radar when a customer, prospect, or partner requests proof of compliance with a specific framework, such as SOC 2 or HITRUST, during the sales process. From there, a request is typically sent to an IT or cybersecurity manager to start pursuing a certification or assessment badge, and suddenly personnel across all departments are scrambling to figure out what they need to do to help the organization pass the audit or assessment.
To be clear, leveraging cybersecurity compliance to win new business isn’t a bad idea. When audits and assessments are conducted in a reactive, non-strategic manner, however, it becomes an inefficient road to compliance that can cost organizations valuable time and resources.
Reactive Audits Prevent a Cohesive Compliance Strategy
When we asked survey respondents to identify the greatest challenge that hinders their organization’s compliance strategy, 23% reported that their audits are reactive and driven by customer requests rather than internal management.
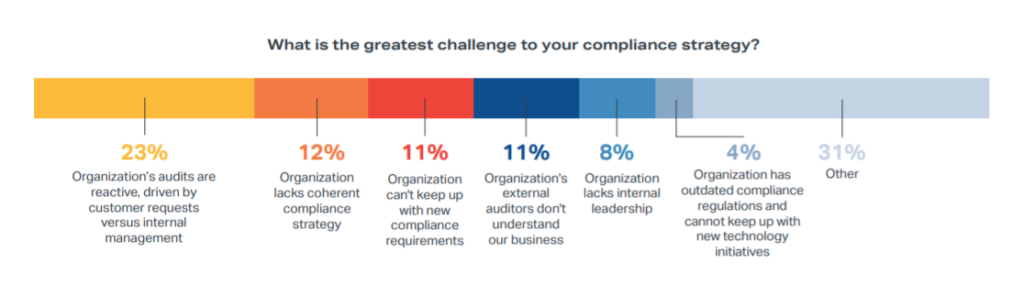
This bottom-up approach to cybersecurity compliance often results in disjointed, unnecessarily repetitive audits that don’t take advantage of a cohesive compliance strategy. Relatedly, our survey found that 85% of organizations conduct more than one audit each year, but only 14% consolidate audits into a single annual event. There are a number of benefits to implementing a Master Audit Plan (MAP) within an organizations, primarily because a MAP can alleviate the pain points that are traditionally associated with an audit process. Specific benefits of a MAP include:
- Combining efforts across audits to decrease workload
- Completing multiple audits in less time
- Optimizing evidence collection and usage
- Creating efficiencies
- Freeing up resources to concentrate on more strategic initiatives
- Streamlining costs
- Protecting your brand
- Allowing organizations to think of their program more holistically and systematically
- Better communication to internal stakeholders on progress and process
- Limiting the number of auditors to manage
Key Takeaways
Although modern business leaders are more aware than ever of the dangers of cybersecurity threats, employees may not be on the same page about the true purpose of their compliance programs. And though cybersecurity compliance is undoubtedly a great way to win new business, it can take a toll on productivity and profitability when audits and assessments are a reactive, customer-driven endeavor instead of a carefully planned effort that involves buy-in across all departments.
Organizations can greatly benefit from spending more time at the onset of a cybersecurity compliance initiative to ensure the right people, processes, technology, and/or partners are in place to facilitate long-term success. This means looking beyond the compliance projects that are on the immediate horizon to decide how to start laying the groundwork for future audit and assessment needs.
Download the 2021 A-LIGN Compliance Benchmark Report
Ready to refine your compliance program?
What is FISMA and How Is It Related to RMF?
Do you know the difference between FISMA and RMF? We’ve got you covered! Learn how FISMA is related to RMF, the certification process, and the benefits to your agency.
What is FISMA and how are the regulations related to RMF (the Risk Management Framework)? If your organization pursues federal contracts or works with a federal agency, the sheer number of security compliance certifications can seem overwhelming. Understanding the frameworks, processes, and benefits of these certifications can seem daunting. That’s why we’re here to help break down a well-known federal program, the Risk Management Framework (RMF), and the law that outlines the requirements that agencies must meet to achieve compliance, the Federal Information Security Modernization Act (FISMA).
FISMA requires federal agencies to develop, document and implement an agency-wide program to provide security for the information and systems that support the operations and assets of the agency. This includes assets provided or managed by another agency, contractor or other sources.
After its initial launch, FISMA was amended to include several modifications that modernize federal security practices to address ever-evolving security concerns. These changes resulted in less overall reporting, strengthened the use of continuous monitoring in systems, and increased focus on the agencies for compliance and documentation that is centered on the issues caused by security incidents.
What is RMF?
RMF was designed to effectively bring together all of the FISMA-related security standards and guidance to promote the development of comprehensive and balanced information security programs by agencies. According to NIST.gov, the stated goals are as follows:
- To improve information security
- To strengthen risk management processes
- To encourage reciprocity among federal agencies
More simply put, FISMA establishes the standards and requirements of an agency’s cybersecurity program and RMF helps determine how that program is implemented to meet those standards and requirements.
What is the RMF Process?
Essentially, RMF effectively transforms traditional Assessment and Authorization (A&A) programs into a more palatable six-step life cycle process that starts with preparation and consists of:
- The categorization of information systems
- The selection of security controls
- The implementation of security controls
- The assessment of security controls
- The authorization of information systems
- The monitoring of security controls
RMF has currently been implemented across the major sectors of the federal government, including:
- Federal “civil” agencies
- Intelligence Community (IC) agencies
- Department of Defense (DoD) components
If your agency falls under these parameters, it’s likely they rely on FISMA and RMF approved standards when it comes to your cybersecurity systems and procedures.
What are the FISMA Requirements within the RMF Process?
In order to comply with FISMA, an organization must go through the Assessment and Authorization (A&A) process with a Federal agency. To make this process as simple as possible, a Federal cybersecurity assessment can be divided into four general phases:
Phase I: Initiation Phase
- This phase includes preparation, resource identification and system analysis.
- This ensures that all senior officials are on the same page and agree with the drafted security plan.
- Testing should be performed before certain actions such as identifying key security officers, conducting an initial risk assessment, or an independent audit.
Phase II: Security Assessment Phase
- This phase includes security control Assessment and Authorization (A&A) documentation.
- Entities must verify that system controls are properly implemented as outlined during the initiation phase.
- Any discovered deficiencies in security must be corrected.
- At the end of the certification phase, risks to the agency, its systems and individuals will be obvious—which will allow for a clear decision-making process.
- When concluding this phase, the Authorizing Official will review any necessary security updates or adjustments.
Phase III: Security Authorization Phase
- This phrase includes a decision regarding authorization and documentation.
- Entities must determine if the remaining risks post-implementation of the security controls from phase 2 are acceptable.
- The information system owner, information system security officer, and security controls accessor (SCA) provide collaborative information to the authorizing official, who then determines if the final risk level is within the “acceptability of risk” boundary.
- The goal of this phase is to reach the required authorization to operate.
- A Federal agency may also issue an interim ATO at their discretion for a variety of reasons. Under this interim ATO, the agency outlines whatever actions must be completed to become fully authorized.
- If those actions are not completed by the agreed upon deadline, the Authorizing Official may deny authorization of the system.
- By the end of this phase, all documentation from phases 1 and 2 must be compiled into a final security authorization package—including an authority to operate decision letter.
Phase IV: Continuous Monitoring Phase
- This phase includes system configuration, security management, monitoring and reporting.
- Maintaining a high level of security through monitoring security controls, documenting any updates and determining if any new vulnerabilities develop is this phase’s focus.
- Detailed documentation is key, including tracking the current hardware, software or firmware version in use.
- Officers must also note physical modifications, like new computers or facility access changes.
The Benefits of FISMA/RMF Compliance
Although regulatory compliance is often viewed as a complicated undertaking for agencies, FISMA/RMF compliance is a completely different situation. RMF compliance by meeting FISMA requirements translates to heightened readiness for current and future cyber threats, with many benefits:
- Security: FISMA’s strict criteria and standards can greatly enhance an agency’s cybersecurity systems. Even physical disasters aren’t long-term setbacks—with FISMA’s regulations met, agencies can recover critical data almost instantaneously even after catastrophic damage to the tangible parts of their systems.
- Reputation Management: Reputation management and word-of-mouth are an integral part of business management. The general public is becoming increasingly knowledgeable on cybersecurity issues, such as data privacy, and a data breach could result in a negative outlook on your agency.
- Scalability: One of the benefits of FISMA is that it provides different implementation options depending on the levels of potential impact for an organization or individual if there were a security breach. A breach of security could be a loss of confidentiality, integrity, or availability. The three FISMA implementation levels are: low, moderate and high.
- Understanding the Competition. In the process of categorizing risks, you will gain a valuable understanding of the marketplace, giving you an advantage over your competitors.
Achieving RMF Compliance
For organizations looking to win government contracts, the RMF compliance framework provides clear requirements for the development, documentation and implementation of an information security system for its data and infrastructure.
Combine Multiple Audits to Save Time and Resources
Many organizations have a huge opportunity to combine multiple audits to save time and resources while completing compliance assessments.
Due to an increase in technology and the evolution of the cybersecurity compliance landscape, organizations of all sizes are finding themselves tasked with conducting various compliance audits throughout the year to show both their customers and their industry peers that they take the privacy and security of data seriously. In many cases, these audits are being conducted in a reactive manner, costing organizations time and resources.
There is a better way to conducting multiple audits.
In our 2021 Compliance Benchmark Report, we asked more than 200 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs. We learned that the majority of organizations, regardless of industry, do not have a strategy in place to reduce redundancies when completing multiple compliance audits over the course of each year.
In fact, 85% of respondents conduct more than one audit every year, yet only 14% consolidate audits into a single annual event. This means organizations are using their resources inefficiently and scrambling to execute on compliance programs.
Who Consolidates Their Audits? Not Many.
With so much revenue on the line, and so many compliance requirements in play, it seems logical that organizations would conduct multiple audits in a strategic, unified manner. But this is far from true.
Industry Can Drive Audits
It makes sense that many organizations look to industry-specific guidelines on which audits are required to ensure they remain compliant with industry regulations. When looking across every industry, we found that healthcare is the industry most likely to not consolidate audits. In fact, 94% of respondents within the healthcare industry stated they conduct multiple, individually-managed audits and assessments.
Companies in the technology sector not only conducted the highest number of audits, but also had the highest rate of consolidated audits at 26%. They were also the industry with one of the highest usage rates of technology, using software to help prepare audits and streamline the process 31% of the time, which plays a big role in the ability to consolidate audits.
Size [Also] Matters
The number of audits an organization conducts per year can be impacted by many factors including its size, industry, annual revenue, and more. In fact, we found that most organizations with more than $1 billion in revenue typically conduct more than six audits per year.
We found that 60% of organizations that surpass $5 million in revenue typically complete more than four audits each year. This far exceeds the 21% of organizations that earn less than $5 million in revenue and complete more than four audits per year.
Time & Resources Wasted
Did you know that 27% of respondents stated one of the biggest challenges associated with their audit process is evidence collection? When done as a manual process, it is tedious and takes up valuable resources, not to mention that teams or departments operating in a silo will often gather the same evidence to be used at various points over the course of the year. This not only creates redundancies in the efforts at an organization, but it wastes valuable time.
Organizations that work through multiple audits as disjointed projects often experience a stress-filled and frustrating audit situation for all parties involved. But this isn’t only felt during the audit process itself; it’s also felt during the preparation.
In fact, more than 50% of respondents stated they spend one to two months preparing for each audit or assessment, and 17% stated they spend six months or more preparing for an audit or assessment. The time spent preparing for every audit adds up quickly, especially when organizations are conducting more than one audit every year.
If, however, organizations consolidate audits into a single timeline, it can greatly ease the disjointedness of auditing. An added bonus? Because the audit is strategically planned and expected, it becomes less of a last-minute scramble.
Key Takeaways
The findings shared in our Compliance Benchmark Report illustrate the impact of not implementing a strategic, year-round approach to preparing for audits and assessments. Basically, the combination of a disjointed auditing process with the time and resources required to conduct manual evidence collection creates a perfect storm of chaos.
It comes down to this: Conducting multiple audits throughout the year is complex, but it doesn’t have to be chaotic. Taking a proactive approach to preparing for, and conducting, audits can create efficiencies that help an organization optimize evidence collection and streamline how that evidence is used. And perhaps the biggest benefit? It frees up resources to focus on the more strategic side of the business.
Download the 2021 A-LIGN Compliance Benchmark Report
Common SOC 2 Questions Answered
If you’re new to cybersecurity compliance, you’re probably wondering, “what is SOC 2?” The first step is understanding what information will be audited, what employees are involved in the audit, and what is included in the overall audit process.
Undergoing a SOC 2 can be complex, so we have provided answers to eight common SOC 2 questions on auditing and reporting.
Whether you have just started your business or you’re running an established organization, you know that handling the data of your client is very important. A SOC 2 report provides information about how effectively you are managing the security, privacy, and integrity of a client’s sensitive information.
1. Why is SOC 2 compliance important?
As you know, data privacy and security have never been more important. When working with large customers or those in regulated industries, you will likely be asked to provide proof of your SOC 2 controls, especially if you operate a cloud or services business. Below is a list of common risks related to delaying compliance assessments:
- Less competitive position: Many organizations are required by laws or regulations to ensure the security of their data or their customers’ data. Organizations and customers will typically work with partners and vendors who can demonstrate security controls, practices and compliance over a period of time through industry standard reporting and recognized frameworks, such as SOC 2.
- Drawn out sales process: At some point, a prospect will probably ask for your SOC 2 report before moving any further. Since SOC 2 is a rigorous framework, it is not something that can be completed overnight. Most often, an established SOC 2 framework can take several weeks, from start to finish, to demonstrate evidence of controls and perform the audit. It requires planning, thought, ongoing cybersecurity controls, and the help of an external auditing partner.
- Lack of consumer trust: A SOC 2 report sends a signal to customers that your organization prioritizes IT risk, ethics, security, and the protection of their information and data in delivering services. Obtaining a SOC 2 report indicates a level of maturity around IT security, technology and business. Without a SOC 2 report from a licensed certified public accountant (CPA), customers have no way of verifying that their data is being secured and well-placed. Without this trust, it is very difficult to do business.
- Vulnerability to security threats: One of the most valuable outcomes of pursuing a SOC 2 attestation is improving and maintaining the strength of your own organization’s cybersecurity posture. SOC 2 is comprehensive and covers a wide range of controls. A SOC 2 report can be leveraged to identify new potential risks, threats, security controls or processes to implement at your organization. These new processes cannot only strengthen security controls at your organization, but can also improve metrics, operations and service delivery to customers.
2. What are the Trust Services Criteria?
The scope of your SOC 2 audit report is dependent on how many of the Trust Services Criteria (TSCs) your organization needs to focus on to fulfill your client requirements. The TSCs that you can choose from, include:
- Security (Common Criteria) – The protection of information, data or systems throughout their lifecycle. Security controls are in place to protect against unauthorized access, unauthorized disclosure, and damage to systems that could affect other criteria beyond the Security Category. Security controls are designed to include a wide array of risk-mitigating solutions, such as endpoint protection and network monitoring tools that prevent or detect unauthorized activity. Entity-level and control environment topics are also considered to provide that the necessary controls are in place to govern organization wide security. Each SOC 2 report issued covers the Security category at a minimum.
- Availability – Considers controls that demonstrate systems maintain operational uptime and performance to meet stated business objectives and service level agreements. Availability does not set a minimum acceptable performance level, but it does address whether systems include controls to support and maintain system operation, such as performance monitoring, sufficient data backups and disaster recovery plans.
- Processing Integrity – Ensuring that data is processed in a predictable manner, reasonably free of accidental or unexplained errors. In other words, the information produced or manipulated by your systems needs to be complete, accurate, valid and reliable, to meet stated business objectives and SLAs. Due to the number of systems used by an organization, processing integrity is usually only addressed at the system or functional level of an organization.
- Confidentiality – Requires companies to demonstrate the ability to protect confidential information throughout its lifecycle, including collection, processing and disposal. The specific requirements for Confidentiality related controls may be defined by laws and regulations, as well as internal management or stated business objectives and SLAs. Confidential information may include personal information, as well as other information, such as trade secrets and intellectual property. Controls for Confidentiality include encryption and identity and access management.
- Privacy – Covers communication, consent, and collection of personal information, and verifies appropriate parties have access to that information and what can be done with it. Controls for Privacy include privacy policies and consent management mechanisms.
3. What is the difference between SOC 1 and SOC 2?
A SOC 1 audit is the ideal audit for organizations that handle, process, store or transmit financial information. SOC 1 reports demonstrate that you have the necessary quality controls in place to protect your customers’ financial reporting. These industries may include payroll processors, collections organizations, data centers and software as a service (SaaS) organizations.
A SOC 2 report highlights the security controls in place that protect and secure an organization’s system or services used by its customers. Unlike a SOC 1, the scope of a SOC 2 attestation tests the design and implementation of controls to protect the processing and storage of data that does not directly impact the financial statements of user organizations. Organizations of many sizes and industries can benefit from a SOC 2 assessment, as the audit can be performed for any organization that provides a variety of services to its customers.
4. What are the different types of SOC 2 reports?
When it comes to SOC 2 reports, two options are available: Type I and Type II. The best fit for your organization depends on your specific requirements.
- SOC 2 Type 1 – With this report, the service auditor can validate the presence of the organization’s description of their system and the sustainability of the design of control activities against the selected TSC. The auditor reviews and reports how well the organization has designed the system and its controls considering the selected TSCs as of a specific date in time.
- SOC 2 Type – With this report, the organization will receive a more comprehensive report as compared to Type 1. The report focuses on the description of your organization’s systems along with the operating effectiveness of controls with the service auditor’s test results included within the report. In addition, a Type 2 report gives a historical view of an organization’s environment to determine if the organization’s internal controls are designed and operating effectively over a defined period of time, ranging from three to twelve months typically.
5. What does a SOC 2 report focus on?
A SOC 2 report includes overall processes and controls as described by your organization and the auditor’s assessment either at a point in time (Type 1 Report), or over a period of time (Type 2 Report). This report will include a description of your system and the suitability of the design, and potentially the operating effectiveness of its controls relative to your security posture.
When you receive your SOC 2 report, you can share a version of the report with your customers, vendors, and stakeholders, when appropriate. This shows that your organization has the appropriate policies, procedures, and controls in place to manage and mitigate the key threats and vulnerabilities that pose a risk to their environment.
There are typically four sections to a SOC 2 report:
- Section 1: Assertion of Management – Management is attesting to the accuracy of information provided during the audit. This includes a summary of the details regarding the SOC 2 attestation.
- Section 2: Independent Service Auditor’s Report An independent, external Service Auditor provides an opinion, or summary, of the results of the audit performed.
- Section 3: Description of Client’s System Throughout the Review Period – Includes a number of descriptions about various organizational details associated with the system being reviewed, including but not limited to, company background, services provided, infrastructure, controls, processes, employees, policies and more.
- Section 4: Trust Services Category, Criteria, Related Controls and Test of Controls – Includes details of the organization-specific control activities specified by the service organization and tested by the Service Auditor.
- Section 5 (Optional): Other Information Provided by the Service Organization – Additional information provided by management, where applicable.
6. What areas are commonly reviewed during a SOC 2 assessment?
SOC 2 reports cover an assessment of an organization’s security controls against the in-scope TSC. The list of items and areas within your organization that will need to be reviewed typically requires the involvement of various organizational groups. Examples include entity-level, control environment, endpoint protection, network monitoring, unauthorized activity prevention controls and more. During a SOC 2 audit, document collection, review, and discussion can take several weeks from start to finish to demonstrate evidence of secure controls and perform the audit. The basic list below demonstrates the importance of starting your assessment preparation early as many different areas of your company will be involved and held accountable for providing their information.
For the requirements listed below, you will need to involve your human resources department:
- Organizational charts
- New hire processes
- Employee handbook
- Background checks
- Reporting relationships
- Service-level agreements (SLAs)
For other areas of the SOC 2 audit, the requirements will be the responsibility of your IT team, such as:
- Shared network drives
- Change approvals
- Master list of system components
- User access to systems
- VPN authentication
- Anti-virus software
- Network authentication and configuration
Many of your organization’s cybersecurity standards, settings and processes will also be evaluated, including:
- Information security policies
- The security of your company website
- Monitoring tools
- Incident response policy
- Risk assessment policy and risk assessment
- Network diagram and firewalls
- Encryption settings
- Internal controls matrix
- Third-party and vendor policy and assessment
7. What are some tips for companies as they prepare for an audit?
Before beginning the SOC 2 audit, it is important that your organization is well-prepared to avoid any delays in assessment or additional costs. To ensure you earn the SOC 2 report in a timely manner, it is important that you consider following a few basic guidelines
- Stay up-to-date on standards
- Review recent changes in organizational activity
- Create a timeline and delegate tasks
- Review prior audits (if applicable)
- Organize data and gather evidence ahead of fieldwork
- Review requests and ask questions
- Evaluate results
8. How do I select the right audit partner?
Ensure your audit partner has the right qualities and they:
- Are licensed
- Undergo audits themselves
- Are properly staffed
- Respond within 24 hours
- Offer premium audit software
- Provide a comprehensive suite of services
Next Steps
When beginning the SOC 2 compliance journey it is important to engage a professional and certified auditing firm to work with you.
Do you still have questions regarding a SOC 2 audit and report? Let our SOC 2 experts guide you through the process.
As a licensed CPA firm and one of the top issuers of SOC 2 reports in the world, A-LIGN has the people, process, and technology you need to help your organization reach the summit of your potential as it pertains to compliance.
A SOC 2 in 14 days? We’ve completed thousands of them and we can say with authority that this is misleading. As auditors, we believe in accuracy, so we wanted to share what it really takes to complete a SOC 2 and how to get it done as quickly as possible.
The other day I got a call from a fast-growing startup company in the data analytics space asking if we could do a SOC 2 in two weeks “like other companies do.” This isn’t the first time I’ve received this question – in fact, lately, it’s coming up more and more. The conversation that ensued went something like this…
Me: Two weeks? What’s driving that timeline?
Client: I see ads all the time about getting a SOC audit in 14 days. Are you doing that?
Me: Ahh, I’ve seen those too. I’m afraid the reality is a bit more complicated.
Client: Isn’t that the whole point of SOC 2 automation software – simplifying it?
Me: (shaking head) Ok, let me explain…
Setting the Record Straight: SOC 2 Audits Take More Than 14 Days
Here’s the thing. We’ve performed thousands of SOC 2 audits. In fact, A-LIGN is the top issuer of SOC 2 reports in the world. We’ve produced reports for companies of all shapes and sizes, across all industries and around the globe. We know the ins and outs of the process – where companies struggle, where they trip up, and where the opportunities are to move faster.
So, we can say this with a reasonable degree of authority: A SOC 2 can’t be completed in 14 days without any preparation.
Only Part of Your Audit Can Be Done in 14 Days
To help illustrate why – and where the confusion is likely coming from – here’s a little diagram:
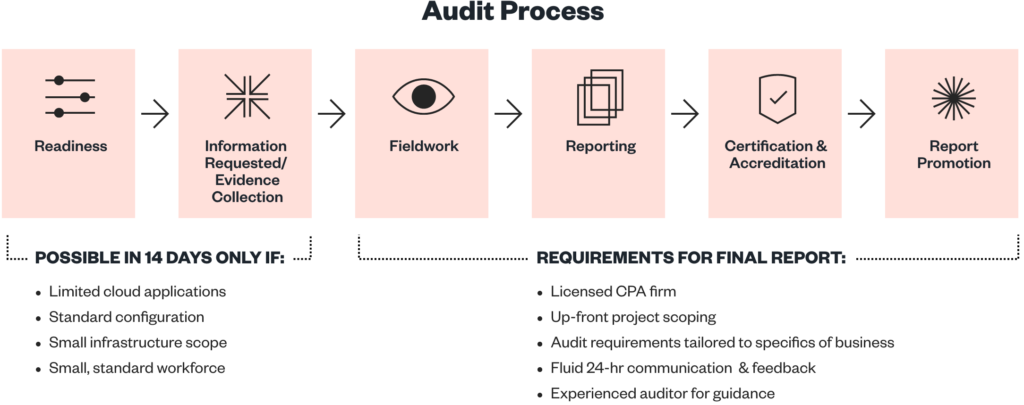
As this picture shows – when you see something that says, “14 days to SOC 2,” it’s actually only referring to the first part of the process. They aren’t talking about your completed SOC 2 report, which is your ultimate goal. The so-called “14-Day SOC 2” is a way of saying that, under certain circumstances, an automated system can get you a bunch of data that’s required to begin your audit in as little as 14 days. You won’t get a final report in that timeframe – you’ll only set the stage to get it produced.
Furthermore, that initial portion of your assessment can only be done if your environment meets a specific set of criteria. For example:
- You may need to be running your entire business from a limited set of cloud apps, such as AWS, Jira, GitHub, and a few others
- Those systems and the rest of your environment may need to be configured in a standard way
- Your infrastructure footprint probably needs to be small, simple, and consistent
- Your company probably can’t be too big – around 50 employees or under – and you’ll likely need a relatively standardized workforce in terms of roles and functions
The minute you start to introduce complexity at your company – in systems, processes, configurations, or your workforce – that’s when you’re going to see your SOC 2 take more time. Why? Because ultimately your auditor’s objective is to assess your cybersecurity practices, and the more complex your organization is, the more complex those practices will naturally be.
A more appropriate ad would read “14 days to gather information for your SOC 2” – or something similar. That’s not as catchy – but it is more accurate, and as auditors, we care deeply about accuracy.
Understand the Full Scope of Your SOC 2 with These 10 Questions
Alright, you’ve made it this far, and perhaps you are thinking that 14 days even to get ready for a SOC 2 sounds pretty good. And you’d be right – that would be fantastic. Just remember when something looks too good to be true, it often is. Do your due diligence by asking these questions:
1
After I’ve gotten through those 14 days, what else needs to be done – and by whom – so I can earn my final report?
2
Are there areas of my environment that can’t be instrumented or automated –– and who is responsible for populating this evidence? In particular, ask about:
- Legacy systems, data center systems, non-cloud systems
- Coverage across user workstations and mobile devices
- Differences between the health check that a tool provides and the evidence required to support it (for example, a report of where antivirus is supposed to be installed vs the actual evidence of the installation on each device)
- Observations for physical and environmental security concerns (including management of the maintenance records for applicable systems)
a. Legacy systems, data center systems, non-cloud systems
b. Coverage across user workstations and mobile devices
c. Differences between the health check that a tool provides and the evidence required to support it (for example, a report of where antivirus is supposed to be installed vs the actual evidence of the installation on each device)
d. Observations for physical and environmental security concerns (including management of the maintenance records for applicable systems)
3
For new policies that need to be developed – are templates provided enough for the context of your business? How will you customize them properly? What is the timeline required for implementation and training so I can show effectiveness against the policy control?
4
What is the process for instances when the data produced by the automation tool is not sufficient for the needs of the audit? Requirements fall through the cracks more often than you’d think, especially in more complex environments. This is commonly experienced when testing Sample Populations for Type 2 audits.
5
Who will project manage your SOC 2? When you have questions, who is available to address them? Does your software vendor know enough about SOC 2 to help in a meaningful way? What if their advice conflicts with your auditor? How quickly can you get questions answered with all those parties involved?
6
What is the process for evaluating, questioning, commenting on, and supplementing evidence when questions need to be addressed? Are those changes tracked in a software tool, or will you still need to rely on email and spreadsheets?
7
Who will my auditor be? How do I choose them and what is the transition like? Do they have a good reputation? Have they successfully published reports that stand up to demanding customers? Are they superior to the auditor used by your competitors?
8
Are there other assessments that need to be coordinated with your SOC 2, for example, penetration testing, vulnerability assessments, risk assessments, ISO 27001 certification, FedRAMP certification, etc.? Who will conduct these and how will information be shared?
9
How much evidence is needed to satisfy time-based requirements (particularly for SOC 2 Type 2 reports)?
10
Who is responsible for resolving disputes with the auditor?
Do the Right Thing, Always
One of A-LIGN’s core values is “Do the Right Thing, Always” – which is why we felt it was important to help people understand how the SOC 2 process actually works and what to expect from it, especially for those people going through it for the first time.
Our SOC 2 engagements are thoughtfully planned and professionally executed, leverage our expert auditors’ many years of experience, and include complimentary software and automation to get you through your SOC 2 as quickly and efficiently as possible.