Ransomware attacks are becoming more prevalent, more complex, and even more costly to businesses. According to The State of Ransomware 2022 report from Sophos, two-thirds of organizations across the world have been hit with ransomware in the past year, and 72% have experienced an increase in the volume, complexity, and/or impact of cyberattacks such as ransomware.
This is why it is imperative to have a comprehensive ransomware preparedness plan in place. But unfortunately, many businesses aren’t there yet. A-LIGN’s 2022 Benchmark Report showed that of those surveyed, only 39% of organizations have a plan in place, whereas 40% are “planning to develop” something in the future, and a full 10% said they don’t view ransomware as a main cybersecurity concern.
This is a large discrepancy and leaves many businesses extremely vulnerable. To help you kickstart your ransomware preparedness plan, we’re breaking down the top questions A-LIGN has received about ransomware preparedness.
Is My Organization Susceptible to Ransomware?
Any organization in any industry can fall victim to a ransomware attack, but the industries that are targeted the most include manufacturing, finance, healthcare, and education.
Ransomware attacks have caused significant impacts on organizations in multiple sectors. In December 2021, a ransomware attack caused Lincoln College to permanently shut down. The late-February Bridgestone attack earlier this year halted tire production at a Toyota factory for over a week, and it took the company more than four months to fully recover. In Costa Rica, an ongoing ransomware war has caused the government to declare a national emergency, with no end to the crisis in sight.
The severity of these attacks has raised alarms for many, driving the need for stronger ransomware preparedness plans.
“Ransomware has become as big or bigger than advanced persistent threats,” said retired Lieutenant General Cardon. “It was once believed that if you’re a small company, you have nothing to worry about. But, from the offensive side of cybersecurity, this simply isn’t true. A small company that doesn’t think it’s a target and does not have appropriate defensive measures, will more likely be a target because they are an easy victim. Believing you’re safe just because you’re a small company makes your organization a weak link and easy target.”
Why Should We Prioritize Ransomware Preparedness?
The examples above show how the aftermath of a ransomware attack can prove catastrophic for an organization, in terms of financial impact, reputational damage, and even legal repercussions.
As ransomware gangs become more sophisticated in their pressure tactics, organizations need to be prepared for a variety of attacks such as encryption, data hostage situations, or Distributed Denial of Service DDoS. Cyberattacks are costly for businesses, but also for the victims of attacks who have their personal information stolen. Organizations who lack a recovery plan run the risk of permanent reputational damage, along with fines if it was compliance failures that allowed the attack to take place.
Even though threats may be harder to detect, public empathy appears to be declining. Some believe organizations should be doing more to keep their sensitive data protected. A growing movement against paying ransoms has emerged, with some governments considering proposed legislation banning payments.
With so much at stake, organizations must make disaster recovery a core focus of their ransomware incident response.
What Does a Ransomware Preparedness Assessment Entail?
When it comes to creating a detailed preparedness plan, it helps to start with a complete ransomware preparedness assessment. A-LIGN’s industry-leading ransomware preparedness assessment service consists of three core components: identify, test, and prepare.
Identify Key Assets and Areas for Improvement
The first step in the preparedness assessment involves a key asset and risk profile identification. This is followed by a security capabilities maturity review based on the National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF). A-LIGN will also complete an enterprise-wide architecture review.
Maturity Assessment: To gain an understanding of the current environment and threat landscape, A-LIGN will conduct discovery workshops to help identify potential areas of improvement in an organization’s cybersecurity posture. A-LIGN will leverage the NIST Cybersecurity Framework (NIST CSF) to evaluate the organization’s capabilities against the five unique domains of the NIST CSF, including: Identify, Protect, Detect, Respond, and Recover.
- Architecture Review: A-LIGN will review the organization’s enterprise-wide architecture to identify potential design issues as well as areas of improvement. A-LIGN will conduct workshops with relevant stakeholders to review the current architecture, network segmentation, as well as any existing strategic plans for improvement of the architecture.
Test How Your Organization Reacts to Real-World Attack Scenarios
The test stage assesses an organization’s readiness to effectively respond to cybersecurity threats. It involves two types of adversarial simulations:
- Penetration Testing: As part of the Technical Assessment, A-LIGN will test both the external and internal defense systems of an organization through the execution of penetration tests (scope and tests to be determined by management). These tests will simulate a real-world attack to test the organization’s capabilities to detect and respond to a malicious actor.
- Social Engineering: A-LIGN will conduct Social Engineering Tests (methodology to be determined by management, however, this can include phishing, spear phishing, pretexting, vishing, etc.). A-LIGN will attempt to compromise the credentials of both privileged and non-privileged users to gain access to systems and data.
Prepare a Detailed Response So You Can Resume Operations ASAP
In some instances, the resulting organization-wide downtime can be as costly as the ransomware attack itself. The prepare stage is designed to close any gaps in an organization’s ransomware response and preparedness capabilities. It involves two components:
- BCDR Plan Review: To ensure organizations have the plans in place to recover from a cybersecurity event, A-LIGN will conduct a review of the organization’s existing Business Continuity and Disaster Recovery Plan against industry best practices to identify potential gaps and potential areas of improvement in the existing plan.
- Table-top Testing Exercise: A-LIGN will develop and facilitate a unique table-top test plan based on discussions with management on practical scenarios, unique industry risks, unique geographic locations, and our experience in Business Continuity Plan (BCP) test plan development. The goal of this exercise is to simulate a real-world scenario to assess the organization’s capabilities to respond in the event of a disaster.
What Are the Benefits of a Ransomware Preparedness Assessment?
Once your organization has completed a ransomware preparedness assessment, you gain the ability to:
- Identify gaps in your organization’s cybersecurity plan, based on the NIST CSF, and help your team to prepare for possible future cybersecurity events.
- Recognize and remediate the cybersecurity vulnerabilities discovered through penetration testing and social engineering.
- Validate the security investments that are working well, and identify those that are not working as intended.
- Have a better understanding of the quality of existing policies and procedures and determine how they can be improved to help with ransomware preparedness.
- Feel less stress, especially amongst internal stakeholders, knowing that the organization has a rock-solid plan in place to respond to an inevitable attack.
A strong ransomware preparedness plan doesn’t only benefit the internal members of an organization. Partners, prospects, and customers will also feel peace of mind knowing that your organization is prepared and can properly defend against and respond to cybersecurity events.
How Do I Get Executive Buy-In for a Ransomware Preparedness Assessment?
Deciding your organization is ready for a ransomware preparedness assessment is only part of the process: you will most likely need executive buy-in as well.
Fortunately, the numbers supporting this move rule in your favor. Without a strong cybersecurity system in place, an organization is at risk for loss of revenue, reputation, and customers, ultimately leading to a considerable drop in profitability.
According to Keeper’s 2021 Ransomware Impact Report:
- Nearly half (49%) of organizations pay the requested ransom during attacks
- 64% of organizations lost important login credentials or documents during attacks
- 64% of organizations believe their company’s reputation has declined post-attack
- 28% of system/network outages last at least one week — a significant amount of downtime that is very costly for businesses
Highlighting the risk an organization faces may increase the likelihood of your organization’s executive team supporting the completion of a ransomware assessment.
Getting Started
With the rapid increase in ransomware attacks, all organizations should have a thorough ransomware preparedness plan in place. Before creating this plan, an organization should complete a Ransomware Preparedness Assessment to gain a better understanding of current vulnerabilities and areas that require improvement.
Contact A-LIGN to learn more about our one-of-a-kind Ransomware Preparedness Assessment.
There are a variety of threats to information security for an organization, in the form of breaches, ransomware attacks, and other cybersecurity incidents. To safeguard data and information, organizations must implement proper security controls. For organizations whose services are likely to be relevant to their clients’ internal control over financial reporting, a SOC 1 audit can help accomplish this goal.
In this article, we describe the details of a SOC 1 audit and reveal the value it brings to organizations that undergo the process.
What Exactly Is a SOC 1 Audit?
A Service Organization Controls (SOC) 1 attestation examines and reports on a service organization’s controls over the services it provides to clients when those controls are likely to be relevant to the client’s internal control over financial reporting. A SOC 1 can also evaluate that an organization has the proper internal controls in place to secure important data and information, such as the necessary information technology controls supporting the system.
Who Should Undergo a SOC 1 Audit?
Organizations handling sensitive financial data, particularly those whose actions affect the financial reporting of their clients, should undergo SOC 1 examinations to demonstrate that their information is properly secured and processed accurately. These include payroll processors, payment processors, collections organizations, benefits administrators, Software as a Service (SaaS), managed-service providers (MSPs), and other similar organizations.
SaaS or cloud-service providers (CSPs) that are currently SOC 2 compliant may still be required by their customers to obtain a SOC 1 if their service directly impacts the financial statements of their customers.
What Is a SOC 1 Report?
Following the completion of a SOC 1 audit performed by a licensed CPA, the firm will issue a SOC 1 report that includes a detailed description of the system, the controls examined, and the auditor’s opinion. The SOC 1 report is an “attestation” whereby management at the organization being audited attests to the controls that have been implemented. The auditors will provide an opinion on the suitability of management’s assertion and the controls tested, and management may use the document to build confidence with clients and drive changes that are needed to bolster or maintain the robustness of the system of controls.
A SOC 1 report can be performed as Type 1 or Type 2. A SOC 1 Type 1 attests to the design and implementation of controls at a single point in time. Your auditor will review evidence from your system as it exists at a “moment in time”. A SOC 1 Type 2 attests to the design, implementation and the operating effectiveness of controls over a period of time, usually between 3-12 months. A Type 2 provides assurance of not just how your systems are designed, but the effectiveness of their operation on a day-to-day basis.
To help you best prepare for your SOC 1 audit, we recommend undergoing a SOC 1 Readiness Assessment to identify high-risk control gaps, giving your organization the opportunity to remediate any issues prior to the SOC 1 audit.
What Value Does a SOC 1 Audit Bring?
A SOC 1 audit can bring tremendous value to your business by enhancing internal procedures and positioning you favorably to partners and customers, Here’s how …
Builds Client Trust
A SOC 1 builds trust and may even be a requirement for doing business. If you are a B2B brand that seeks to sign or retain top-tier clients, a SOC 1 report will signal to those clients that their sensitive financial information is in good hands. It’s common for customers to request to see a SOC 1 report before they even engage with your business. If you are unable to provide a report, potential clients may walk away from a deal or opt to partner with a competitor.
For international brands looking to expand across their borders, a SOC 1 can easily be combined with an International Standards for Attestation Engagements (ISAE) 3402 as it grants greater peace of mind to foreign business leaders.
Builds a Better Brand Image
For newer businesses just starting out, building your brand image is important and could mean the difference between success and failure. This is true because the business landscape is fiercely competitive, full of established businesses that have been successfully operating for generations, and upstarts also looking to gain market share.
Larger, established organizations are likely to already have earned a SOC 1 attestation. When you don’t have much history to fall back on, you need to find ways to introduce your brand in the best possible light. A SOC 1 report does just this by demonstrating that your company takes information security seriously. Simply put, brands that earn their SOC 1 have a material competitive advantage over those that have not.
Builds Efficiencies
While a SOC 1 demonstrates compliance with an organization’s controls over the services it provides to clients when those controls are likely to be relevant to the client’s internal control over financial reporting, it can also assist organizations in identifying and monitoring the security controls they’ve implemented to safeguard sensitive data and information.
It is an internationally recognized standard that is familiar to organizations all over the world. By completing a SOC 1 annually, a company can confirm and signal the robustness of their system of controls. Organizations usually have their own audit process when signing clients or partners but will often allow a SOC 1 report in lieu. It’s a far more efficient process that saves time and money.
How Do I Complete a SOC 1 Audit?
Partnering with a licensed CPA is the first step in your SOC 1 journey. All audits are completed in accordance with the Statement on Standards for Attestation Engagements (SSAE) 18. As a requirement, your company will work with the CPA to define what the control objectives are in relation to the in-scope systems. In determining the proper control objectives, the auditor will do the following:
- Identify aspects of the organization’s controls that may affect the processing of the user organization’s transactions
- Determine the flow of significant transactions through the organization
- Assess whether the control objectives are relevant to the user organization’s financial statement assertions
- Evaluate whether the controls are suitably designed to prevent or detect processing errors that could result in material misstatements in user organization financial statements, and determine whether these controls have been implemented
Start Your SOC 1 Journey
A-LIGN is a security and compliance partner as well as a certified CPA firm that has completed over two thousand SOC 1 assessments. Get started on yours by contacting one of our experts and we’ll guide you through your journey to SOC 1 compliance.
With the rise in cybersecurity attacks comes wariness from customers — no one wants to work with an organization that has an increased risk of falling victim to an attack. And when it comes to the Federal government, that rings especially true.
The Federal government has put measures into place to help mitigate risk when working with partner organizations. In fact, these organizations are required to maintain certain cybersecurity standards and authorizations in order to do business with the Federal government.
One of those requirements is the Federal Risk and Authorization Management Program, also known as FedRAMP. In this post, we’ll provide you with everything you need to know about the FedRAMP authorization process.
What is FedRAMP?
With cyberattacks and cloud-based technologies on the rise, federal departments and agencies needed a cost-efficient and risk-based approach to cloud adoption.
This led to the creation of the Federal Risk and Authorization Management Program (FedRAMP) in 2011. FedRAMP provides a standardized approach to security assessment, authorization, and continuous monitoring specifically for cloud products and services used by federal entities that store, process, and transmit federal information.
What is the goal of FedRAMP?
As a government cybersecurity framework, the goal is to accelerate the adoption of secure cloud solutions through the use of assessments and authorizations. For organizations that achieve FedRAMP authorization, it’s a powerful validation of the security of the organization’s cloud solution.
Why is FedRAMP important?
FedRAMP increases confidence in the security of cloud solutions through continuous monitoring and consistent use of best information security practices and procedures. This streamlined, regulated approach helps mitigate the risk of cyberattacks.
Who needs FedRAMP Authorization?
Federal agencies that host their technology in the cloud are required to use a FedRAMP certified Cloud Service Provider (CSP). If you are looking to do business with the government and host federal systems, then FedRAMP applies to your environment, and you will need authorization.
What are the key benefits of FedRAMP Authorization?
Becoming authorized offers CSPs many benefits, including:
- Improved real-time security visibility
- A uniform approach to risk-based management
- Significant savings on cost, time and resources by de-duplicating efforts related to meeting federal cybersecurity requirements
- Increased re-use of existing security assessments across agencies
- Enhanced transparency between government and CSPs
- Improved trustworthiness, reliability, consistency and quality of the Federal security authorization process
Does FedRAMP apply to global organizations?
Yes. Many global organizations are seeking to secure new business deals to strengthen their customer base. If international businesses want to sell a cloud service offering to the U.S. government, they should pursue FedRAMP authorized status.
Why is FedRAMP Certification valuable to cloud service providers (CSPs)?
Federal cloud spending has seen a rise in recent years. In fact, analysis from Deltek found that federal cloud spending reached nearly $11 billion in FY 2021, up more than 40% from the $7.6 billion spent in 2019. CSPs looking to capitalize on this trend should seek to achieve FedRAMP Authorized status.
FedRAMP can also be reused to sell to multiple agencies. In fact, if you already have authorization, it can simplify the certification process for other federal and defense programs, like the DoD’s Cloud Computing Security Requirements Guide (CC SRG)
Who can perform a FedRAMP assessment?
Only accredited FedRAMP Third Party Assessment Organizations (3PAO) may perform FedRAMP assessments.
How do I get FedRAMP certified?
FedRAMP is an integrative standardized assessment designed to be a common one-stop-shop for CSPs seeking to do business with the U.S. government.
There are two paths CSPs can take to achieve authorization:
- Through an agency sponsorship when a government entity vouches for a CSP, streamlining their approval process.
- Through the Joint Authorization Board (JAB). The JAB is the primary governance and decision-making body for FedRAMP.
Although organizations are able to choose which process they’d prefer to take, most organizations choose to achieve certification via agency sponsorship. This is because the JAB path is very competitive as they only select 12 systems per year (specifically, three per quarter).
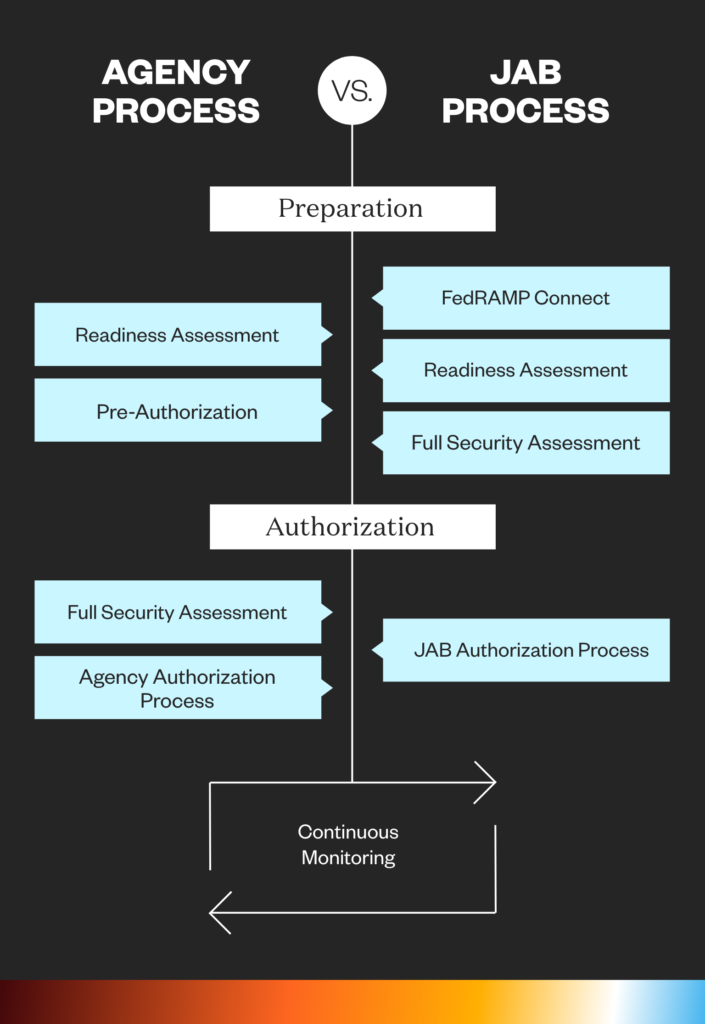
What is JAB P-ATO Status?
The JAB is the primary governing body for FedRAMP and includes the Department of Defense (DoD), Department of Homeland Security (DHS), and General Services Administration (GSA). The JAB selects approximately 12 cloud products a year to work with for a JAB Provisional Authority to Operate (P-ATO).
The JAB Authorization process involves:
- An evaluation via FedRAMP Connect
- Completing a FedRAMP Ready assessment
- Completing a full-security assessment
- Achieving authorization via the JAB
- Continuous monitoring post-authorization
What is Agency ATO Status?
In the Agency Authorization path, agencies may work directly with a CSP for authorization at any time. CSPs that make a business decision to work directly with an agency to pursue an ATO will work with the agency throughout the FedRAMP Certification process.
The Agency Authorization process involves:
- An optional, yet highly recommended, FedRAMP Ready assessment
- Pre-authorization
- Achieving agency authorization
- Continuous monitoring post-authorization
What are the key processes involved with a FedRAMP Assessment and Authorization?
Regardless of which method (agency sponsorship vs. JAB) you choose, the authorization process always involves:
- A Preparation Phase, where the provider completes a System Security Plan (SSP). After this, a FedRAMP-approved third-party assessment organization (3PAO) will develop a Security Assessment Plan.
- A Full Security Assessment, where the assessment organization submits a Security Assessment report and the provider creates a Plan of Action & Milestones PoAM). The security assessment involves evaluating a company’s policies and procedures against a set of requirements from the NIST 800-53 controls to test security authorizations. Once granted, continuous assessment and authorization guidelines must be in place to uphold authorization.
- Authorization, where the JAB/authorizing agency determines whether the risk as described is acceptable. If confirmed, they submit an ATO letter to the FedRAMP project management office. The provider is then listed in the FedRAMP Marketplace.
- Continuous Monitoring, where the provider sends monthly security monitoring deliverables to each organization using the service.
What’s the timeline of a FedRAMP Assessment?
Step 0: It’s recommended you complete a gap assessment to address any holes in your environment. This ensures a CSP is ready for the FedRAMP authorization assessment to be submitted for FedRAMP Authorized status.
Step 1. Pre-Assessment Review (1-4 Weeks)
Step 2. Planning Activities (4 Weeks)
Step 3. Assessment Activities (7 weeks)
Step 4. Reporting Activities (5 weeks)
Step 5. Sponsor Issues Authority to Operate (2-3 weeks) and listed in the FedRAMP Marketplace
Step 6. Maintain Authorization
How long is FedRAMP valid?
A FedRAMP Ready designation is only valid on the Marketplace for twelve months.
What are the impact levels of FedRAMP compliance?
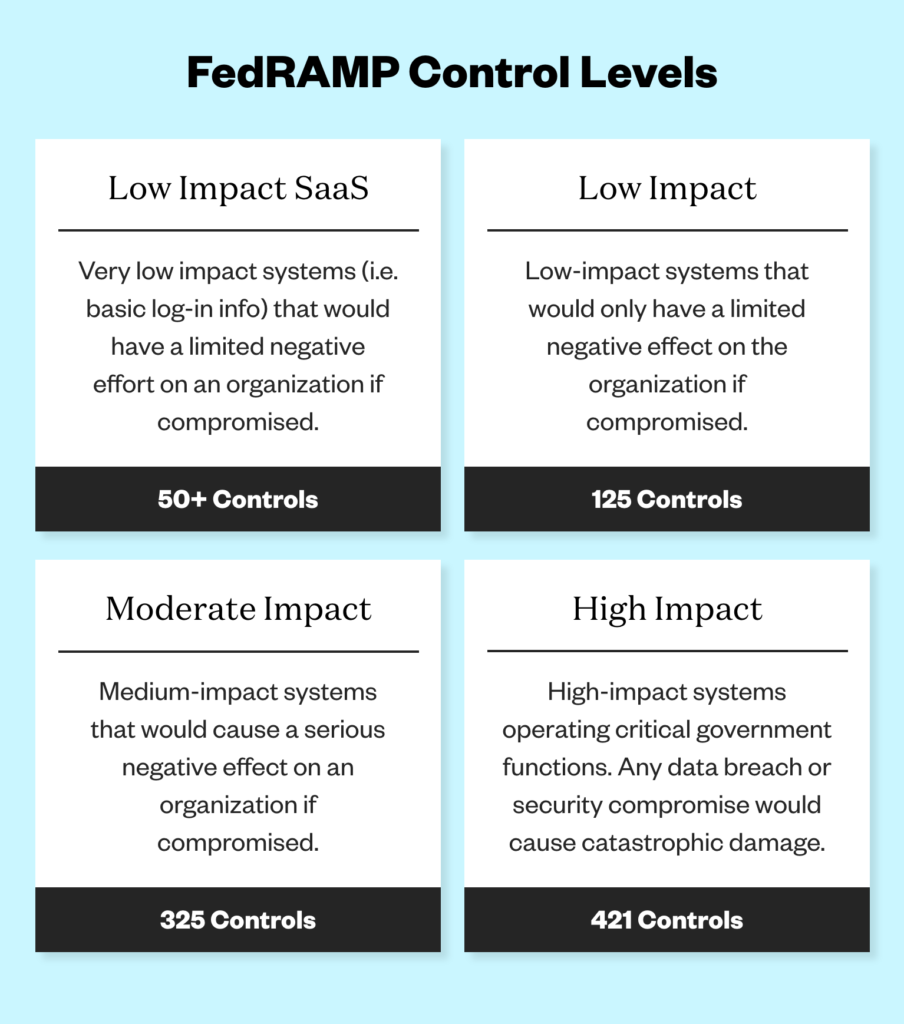
Low Impact SaaS (FedRAMP Tailored or Ll-SaaS): Ll-SaaS is a subset of low impact and typically includes 50+ of the controls to be independently assessed. This baseline accounts for SaaS apps that do not store personal identifiable information beyond basic log-in information, like usernames and passwords. Organizations that achieve the LI-SaaS level would experience minor adverse effects should a loss of confidential information occur. Information about the security controls required for this designation can be found here.
Low Impact Level: Low includes about 125 controls. Organizations that achieve the low authorization status would experience limited adverse effects if a loss of confidential information occur.
Moderate Impact Level: Moderate includes about 325 controls and the vast majority of organizations fall into this category. The loss of confidential information in this category would have a serious impact on an organization.
High Impact Level: High includes approximately 425 cybersecurity controls and mainly includes organizations that work in law enforcement and emergency services systems, financial systems, and health systems. Organizations should especially pursue High impact if any loss of confidential information could be expected to have a catastrophic impact.
Please note, the number of controls for each impact level are currently based on NIST 800-53 revision 4 and will change with the transition to revision 5. The transition plan and associated templates and guidance is expected to release by end of 2022.
For more information about the security controls required for each designation, click here.
FedRAMP vs. FISMA/NIST RMF
Prior to FedRAMP, the U.S. government introduced the Federal Information Security Modernization Act of 2014, or FISMA.
FISMA is the law directing government agencies to develop and maintain an information security program. FedRAMP is a cloud-specific implementation of NIST RMF. Even though FISMA and FedRAMP use the same standard, utilizing the same controls set within NIST 800-53, the two have different authorization processes.
In order to bring together all of the FISMA-related security standards, NIST created the Risk Management Framework. Whereas FISMA establishes the requirements of an agency’s cybersecurity program, RMF helps determine how that program should review, assess, and approve IT systems for use.
What’s the difference between FedRAMP and StateRAMP?
StateRAMP can be thought of as FedRAMP compliance for state and local governments, and it has a Security Assessment Framework that is based on the National Institute of Standards and Technology Risk Management Framework (NIST RMF).
StateRAMP offers a fast track to authorization for current FedRAMP authorized services.
Is continuous monitoring needed for FedRAMP?
Yes. Monthly updates (scans and POA&Ms) to the Agency Sponsor or JAB (based on authorization pathway) are important to ensure your organization has maintained compliance with FedRAMP. Annual assessments that include penetration testing, select control assessment, system scanning, and more are critical to your continued compliance standing.
If your organization has experienced any significant changes that will impact your compliance standing, you’ll need your agency or JAB to review and assess through a Significant Change Request Assessment.
What are FedRAMP key terms?
Check out our FedRAMP compliance glossary of terms to learn the definitions for Third Party Assessment Organizations (3PAO), authority to operate (ATO), cloud service provider (CSP), Federal Information Security Modernization Act (FISMA), joint authorization board (JAB), National Institute of Standards and Technology (NIST) and more.
What are the common challenges of FedRAMP authorization?
- CSPs Might Not Know Authorization Is a Detailed Process: FedRAMP security standards are more prescriptive than general security assessment and requires granular detail.
- CSPs Might Overlook the Benefits of Control Inheritance: Inheriting as many security controls as possible from your CSP organization’s underlying FedRAMP authorized infrastructure provider will save time and resources.
- Organizations Underestimate the Power of Automation: Compliance automation software can help automate and streamline your authorization process.
What’s new with FedRAMP?
The FedRAMP Rev 5 Baselines: The final Rev 5 baselines and transition plan to Rev 5 are expected in early 2023. The biggest difference between the Rev 4 and Rev 5 baselines is that FedRAMP has introduced a threat-based methodology to determine which controls should be added on to the established NIST 800-53 Rev 5 baselines.
The Updated Readiness Assessment Report (RAR): A RAR is what CSPs use to determine if they are ready to undergo the extensive FedRAMP certification process. In a thorough 19-page document, FedRAMP provided updated guidance as well as templates for 3PAOs evaluating CSPs for readiness.
Helpful FedRAMP Resources
Beginning the Authorization Process
FedRAMP can help organizations win more business and stand out from their competition, but the approval process is detailed.
As a CSP, you must implement the appropriate controls before you can begin the FedRAMP certification process. Whether you seek authorization via an agency or through the JAB, it is important to ensure you have a trusted resource to help guide you through the process.
A-LIGN is a top accredited FedRAMP 3PAO, having helped organizations worldwide achieve full authorization.
If you are a CSP currently providing, or seeking to provide, services to federal agencies, speak to an expert at A-LIGN about the FedRAMP authorization process.
At a time when cyber-attacks are occurring at unprecedented rates, maintaining information security is paramount. Organizations can demonstrate their commitment to data security by undergoing a SOC 2 audit, which assesses the controls designed to protect an organization’s system or services. There are two types of SOC 2 audits: Type 1 and Type 2. Many organizations elect to start with a Type 1 audit, and later move to a Type 2.
In this article, we explore the two types of SOC 2 audits, the process of moving from a SOC 2 Type 1 audit to a Type 2, and the value they each bring.
SOC 2: Type 1 and Type 2
Any SOC 2 audit will evaluate your internal security management system based on one or more of the following five categories: Security (required), Availability, Processing Integrity, Confidentiality, and Privacy. The difference between a Type 1 and Type 2 audit is largely (but not entirely) based on time.
- Type 1: This assessment evaluates the design of internal security controls at a single point in time – perhaps on a specific date: February 1.
- Type 2: This assessment evaluates the design and effectiveness of internal security controls over a duration of time – perhaps a 12-month period starting on February 1.
A Type 2 audit is more comprehensive because it seeks to examine not just the design of security controls, but how the controls work on a daily basis. A Type 2 report is more robust than a Type 1 report as it covers a span of time and tests an array of samples across the different high-risk areas.
So why might an organization that has undergone a Type 1 decide later to undergo a Type 2?
The Process of Moving from a SOC 2 Type 1 to a Type 2
Even if your organization previously completed a Type 1 audit, you should expect to invest additional time and resources into the process of completing a SOC 2 Type 2. The biggest difference in moving to a Type 2 is the quantity of sample evidence that is requested, as a Type 1 report only looks at one sample.
The first step in the SOC 2 Type 2 audit process is to determine the length of the review period. Type 2 audits typically cover a one-year period, but can vary based on contractual requirements between an organization and its clients. Once the review period has been determined, the organization and its auditor will have walkthrough meetings (similar to a Type 1 audit) to understand the security processes and procedures that have been put in place.
Each auditing firm has a sampling methodology that is used and is driven by AICPA (American Institute of Certified Public Accountants) guidance. Expect your auditor to request multiple samples, and for them to review various population pulls within the designated time period. Samples might be pulled from an annual, quarterly, monthly, or daily basis, depending on the frequency and nature (manual vs automated) of the controls being tested.
Moving from a Type 1 to a SOC 2 Type 2
While a SOC 2 Type 1 audit signals to partners and clients (both current and prospective) that you take information security seriously, there are instances where it would be beneficial to pursue a Type 2. These include:
- Contractual obligations – A customer might request that your company obtain a Type 2 report and might even define the length of the review period (six months, nine months, a year, etc.).
- To develop rapport with clients – Business is built on trust and moving to a Type 2 helps give assurance to your clients that their information is in good hands.
- To build brand recognition/competitive advantage – Undergoing a Type 2 audit is more time-intensive than a Type 1, and so completing the assessment demonstrates your company’s dedication to security. This can set your business apart from competitors.
What is the Value of Moving from a SOC 2 Type 1 to a SOC 2 Type 2?
While a SOC 2 Type 1 report confers benefits to organizations by demonstrating their commitment to information security, a SOC 2 Type 2 report has even greater value. This report shows that an organization has not only designed controls, but they were operating effectively through the determined review period. It can therefore be concluded that the organization is capable of maintaining information security.
Value can also be gained through building an environment that is focused on streamlining regulatory compliance efforts. Organizations that only undergo a Type 1 audit are likely to maintain defined controls once a year. But when going through a Type 2 audit, the organization must monitor and maintain controls throughout the full year. This helps in streamlining and reinforcing policies and procedures among team members on an ongoing basis.
Thinking about moving from a SOC 2 Type 1 to a Type 2? A-LIGN can help you navigate the process. We’re more than an auditor. We’re a partner that has completed over 5,000 SOC 2 reports and the top SOC 2 issuer in the world. Contact us to get started on your SOC 2 Type 2 journey.
Data breaches and ransomware attacks continue to dominate the news cycle. To protect data, and position themselves favorably among prospects and customers, companies need to demonstrate a commitment to cybersecurity.
Enter, SOC 2 (Service Organization Control 2), a popular audit that attests to a company’s ability to protect data and information. It’s a strong validator for any company looking to demonstrate its commitment to cybersecurity to partners and customers.
Pursuing a SOC 2 audit is a multi-step process, which can seem confusing at first glance given the fact that there are vendors that provide compliance software, and other vendors who are themselves certified SOC 2 auditors.
This blog will clarify the SOC 2 audit process, as well as explain the role of SOC 2 auditors and compliance software.
When and How to Use SOC 2 Software Tools
There are multiple steps to completing a SOC 2 audit. Many companies start with a readiness/gap assessment, which is the process of reviewing existing controls in place and identifying those that need to be improved or implemented. This process can be executed via an audit consultant, or through specialized software tools that help simplify this process (like A-SCEND).
Compliance software tools typically provide automated workflows and compliance templates, comparing your existing controls against the controls within a selected compliance framework — which, in this case, would be the SOC 2 framework.
Typically, this software allows you to visualize progress toward compliance goals, assign tasks related to evidence collection or policy updates, and collaborate all in one dashboard. Software tools provide a simple way to understand the framework requirements, assess them against your existing policies and procedures, and manage the process of updating policies. While these tools help to better prepare for an audit and streamline the assessment process, an experienced auditor is still a critical component of compliance.
When and How to Use SOC 2 Auditors
Software tools can only take you so far with SOC 2. They can help prepare a company for a SOC 2 audit, but not complete the audit itself. When the actual audit takes place, companies must turn to a SOC auditor.
SOC 2 audits are regulated by the American Institute of Certified Public Accountants (AICPA) and must be completed by an external auditor from a licensed CPA firm. This is the only way a company can receive an official SOC 2 report, whether it’s a Type 1 or Type 2 report.
An official SOC 2 report is valid for one year following the date the report was issued. Future annual audits must also be completed by an external auditor from a licensed CPA firm.
Working with SOC 2 Service Providers
A-LIGN is a SOC 2 audit provider that offers multiple benefits for organizations seeking to complete a SOC 2 audit:
- A-LIGN is a licensed CPA firm that can issue a SOC 2 report. In fact, we are the top issuer of SOC 2 reports in the world.
- With deep experience and expertise, A-LIGN also created A-SCEND, a modern SaaS platform for streamlining compliance and management activities.
If your organization plans to use software to prepare for an audit, it’s helpful to work with a software partner who can also conduct the official audit (as a certified CPA) because it provides an added layer of convenience throughout the SOC 2 process and results in a reputable report.
Organizations need to go beyond the data collection by their compliance software tool and conduct further due diligence, such as observations and walkthroughs (conversations) between the audit team and the client. SOC 2 auditors may also find that they need additional data or evidence necessary to validate the design and operating effectiveness of a complete control set. When you use the same company for a technology-enabled audit, and a SOC 2 report, the software is designed to request all audit materials needed, including manually operated controls and supporting evidence. In this convenient scenario, you can save time, resources, and money.
All-in-One SOC 2 Services with A-LIGN
A-LIGN provides an all-in-one solution for SOC 2. The A-SCEND platform can streamline the audit preparation process by centralizing evidence collection and simplifying the SOC 2 readiness assessment. To make life easier, it’s an “auditor-assisted” process with real experts standing by to help navigate you through your SOC 2 journey. Leveraging the A-SCEND platform sets you up for success when it comes time to completing the actual report with A-LIGN’s certified SOC 2 auditors.
Even better, A-SCEND is not limited to SOC 2. You can trust it to help achieve compliance across multiple security frameworks including SOC 1, HIPAA, PCI DSS and more.
This blog post is a recap of our Demystifying FedRAMP webinar, hosted alongside our partners at Anitian. View the full webinar recording here.
FedRAMP (The Federal Risk Authorization Management Program) was established in 2011 as a way to accelerate the adoption of cloud solutions, and increase confidence in the security of those cloud solutions, across the Federal government.
FedRAMP is an authorization program versus a certification program, meaning that businesses go through a rigorous security review process and are then granted an Authority to Operate (ATO) and listed in the FedRAMP Marketplace. The Marketplace is a comprehensive list of cloud products and services that are approved to work with federal agencies.
Prior to undergoing the FedRAMP authorization process, there are a few key things that organizations should keep in mind to prepare for FedRAMP success.
1. Executive Buy-in and Cooperation is Key
Federal agencies spent nearly $11 billion on the cloud in FY 2021, which spells huge opportunities for cloud service providers. But the journey to FedRAMP authorization is long. It involves many evidence requests, as well as lots of writing-heavy work to document policies and procedures. Before undertaking all of this work, it’s essential to get executive buy-in on the importance of FedRAMP authorization. Which, despite the monetary opportunities present in the federal market, isn’t always easy.
In our extensive experience helping organizations earn FedRAMP authorization, we’ve seen many expensive and time-consuming delays stem from misalignment over priorities within the overall corporate environment. This misalignment makes a long process even longer and will only cause your organization to miss out on opportunities to expand within the government sector.
2. Consider Automated Solutions
If management is hesitant to give buy-in on FedRAMP because of the numerous evidence requests and documentation requirements, consider a software solution that can automate and streamline tedious tasks and make the process significantly easier.
Anitian’s SecureCloud for Compliance Automation platform and A-LIGN’s audit automation and compliance management software, A-SCEND, helps to streamline compliance process. SecureCloud automates the documentation process with template libraries and reference architectures, as well as track progress toward FedRAMP authorization to help teams stay on track. A-SCEND centralizes evidence collection, standardizes compliance requests across multiple security frameworks, consolidates audits, and more.
With automated software solutions, organizations also benefit from a “enter once, populate everywhere” system, removing the need to upload the same documents and information to multiple places during the FedRAMP preparation and evidence gathering phase. This is hugely beneficial, as there are hundreds of pieces of evidence that must be reviewed in a typical FedRAMP authorization.
Both tools are also auditor-assisted, with real humans who can answer any questions you have and help you use the tools to their full potential.
3. Don’t Overlook the Benefits of Control Inheritance
Control inheritance is extremely useful on the road to FedRAMP authorization. Essentially, control inheritance is when your business automatically inherits certain security controls from an underlying infrastructure provider that is already FedRAMP authorized. A great example would be hosting your product on top of AWS or Azure Government — both of which are already FedRAMP certified.
If FedRAMP authorization is in your future, make sure to consider the benefits of control inheritance.
Get Started With A-LIGN
The experts at A-LIGN can assist you every step of the way toward FedRAMP authorization. We can help with implementing appropriate controls, completing a FedRAMP Readiness Assessment Report (RAR), and ensuring you meet FedRAMP requirements by using Federal Information Process Standard (FIPS) Models for low, moderate, or high-impact organizations.
In 2021, we saw cyberattacks and ransomware increase with vengeance and 2022 has proven to be even more challenging.
In our 2022 Compliance Benchmark Report, we surveyed more than 700 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs to gain a better understanding of their organization’s position when it comes to compliance, including strengths, weaknesses, and opportunities.
Here’s how organizations across industries are responding to increased threats and best preparing.
Ransomware Is at an All-time High
A third-party assessment firm like A-LIGN can help you discover where your cybersecurity posture currently stands. Our one-of-a-kind Ransomware Preparedness Assessment reviews your risk, security preparedness, and the strength of your existing controls, helping you determine if your planned response to a security event is acceptable.
Zero trust is an idea that has been gaining traction in the world of cybersecurity over the past few years. It is a key component of President Biden’s Executive Order (EO) on Improving the Nation’s Cybersecurity (issued in May 2021) and it is a trend that Gartner has been tracking closely. The analyst firm predicts that spending on zero trust solutions will grow from $820 million this year to $1.674 billion by 2025.
But what is zero trust? And, what makes it an effective solution to mitigate cybersecurity threats? Zero trust is an IT security model that focuses on restricting information access within an organization to only those who need it. The premise of zero trust is to assume that threat actors are present both inside and outside an organization — therefore no users or machines are trusted by default.
In our 2022 Compliance Benchmark Report, we surveyed more than 700 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs. Here’s what we learned about how organizations are thinking about zero trust strategies.
Zero Trust Priorities Vary Between Industries
While over half of our survey respondents (58%) agree or strongly agree that zero trust is a strategy they must implement in the next 12 months, 29% said they are not sure what they think about its level of importance.
Priorities vary between industries, with IT services (68%), manufacturing (65%), and technology (64%) companies providing the highest amount of agree/strongly agree answers. On the other end of the spectrum, finance (49%) and professional services (47%) had the lowest amount of agree/strongly agree responses.
It’s important to note that public sector organizations who hope to do business with the federal government — regardless of their industry — must prioritize zero trust as mandated by the EO previously mentioned. As we approach one full year since that EO has been in place, we’ll likely see more industries prioritize zero trust in the year to come.
Larger Companies Are Quicker to Adopt Zero Trust
Responses also varied by company size. Our survey found that 73% of organizations with $50M – $1B in annual revenue agree/strongly agree about the need to adopt a zero-trust security strategy. For companies with less than $5M in revenue, that percentage dropped significantly to 45%. These numbers indicate that larger companies believe they are a top target for cybersecurity attacks and are taking the initiative to plan ahead and protect systems and information.
Other Cybersecurity Initiatives Remain Top of Mind
Despite lower adoption of zero trust strategies among certain industries and smaller companies, many organizations across industries still noted they would complete other cybersecurity initiatives to mitigate threats. Vulnerability scans were the most popular initiative, noted as a priority by 52% of our survey respondents, followed by penetration tests (48%) and creating business continuity and disaster recovery (BCDR) plans (42%).
Interestingly ISO 22301 certifications — a renowned standard for BCDR planning — were a particularly high priority for IT services organizations and manufacturing companies.
A Strategic Approach to Implementing a Zero-Trust Architecture
Implementing a zero-trust architecture within any organization can feel like a daunting feat without the right preparation. To make this process more manageable, the experts at A-LIGN recommend a step-by-step approach.
Before you get started, it’s important to troubleshoot possible scenarios that may occur during the implementation process. From there, plan and implement zero trust in ‘zones’ throughout your organization’s infrastructure whenever possible. This strategy will allow you to keep key business operations up and running while mitigating the chance of downtime across too many areas of your business all at once.
With federal cloud spending at an all-time high, the government sector has become a lucrative market for technology companies. Analysis from Deltek indicates that federal agencies spent nearly $11 billion on the cloud in FY 2021, up more than 40% from the $7.6 billion spent in 2019.
Cloud service providers (CSPs), in particular, have a significant opportunity to capitalize on this meteoric rise in federal cloud adoption. However, in order to do business with the U.S. government, such companies must achieve Authorization to Operate (ATO) status under the Federal Risk and Authorization Management Program, also known as FedRAMP.
In the article below, you will learn:
- Why the U.S. government is prioritizing cloud technologies
- The current trajectory of federal cloud spending
- How your business can use FedRAMP to capitalize on this trend
The Cloud Smart Strategy (Formerly Cloud First Strategy)
A 2017 Executive Order (EO), Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, was a major catalyst in accelerating the federal agency adoption of cloud-based solutions. It declared that agencies must “show preference in their procurement for shared IT services, to the extent permitted by law, including email, cloud, and cybersecurity services.”
As a result, the U.S. government officially updated its Federal Cloud Computing Strategy from “Cloud First” to “Cloud Smart” in June 2019. The Cloud First strategy was more conceptual in nature and left many implementation questions unanswered. Cloud Smart, on the other hand, was designed to provide practical guidance to help agencies enhance the speed, security, and cost savings of their IT programs. A significant amount of this guidance focuses on brokering business relationships with CSPs based on the value their cloud technology provides.
More recently, the 2021 Executive Order on Improving the Nation’s Cybersecurity mandated that the head of each government agency “update existing agency plans to prioritize resources for the adoption and use of cloud technology.” This demonstrated that the U.S. Government remains dedicated to realizing the long-term mission of Cloud Smart.
Record-high Spending Across the Federal Cloud Market
Government agencies are currently experiencing broader, more intense pressure to adopt cloud-based solutions than ever before. But are they acting accordingly to fulfill the promise of Cloud Smart?
If you look at federal cloud spending data from the past few years, the answer is a resounding “yes.” As mentioned above, agencies spent an impressive $11 billion in FY 2021, outpacing several different projections from mid-2021 by an order of magnitude and suggesting that the market is growing even faster than many anticipated.
What’s more, the total value of cloud contracts awarded by federal agencies in FY 2021 was a staggering $23.3 billion, indicating that the government is committing to long-term relationships with CSPs, offering high-value solutions for their IT needs.
Even in the face of a looming recession, federal spending on technology has remained steady, and cloud remains a top priority that is firmly locked in the upper percentile of all federal contract spending.
Using FedRAMP to Capitalize on the Federal Cloud Boom
It has become abundantly clear agencies are steering their considerable purchasing power toward the adoption of cloud technologies. To streamline and standardize the security and procurement elements of the Cloud Smart strategy, the government is using FedRAMP.
In order to do business with government agencies, CSPs must demonstrate their ability to meet federal security requirements through FedRAMP assessment, authorization, and continuous monitoring. The program resulted in a robust marketplace of vetted CSPs for agencies to choose from when evaluating their technology needs and advancing their cloud maturity.
It’s also worth noting that the FedRAMP program continues to put a great deal of effort into making the authorization process more accessible to CSPs of all shapes and sizes. In 2018, six years into the program, there were 100 authorized products. In just a few years, that number has more than doubled to 260+ authorized products and counting.
Best of all, agencies have a great deal of trust in the security of FedRAMP-authorized cloud solutions and are leaning heavily on vendors from the FedRAMP marketplace. According to FedScoop’s recent Federal Perceptions of Cloud Security report, federal IT leaders believe FedRAMP is the number one way to maintain security control over their agency’s strategic data, above on-prem data centers and hybrid/commercial cloud environments.
Three Reasons CSPs Should Invest in FedRAMP Now
Are you a CSP considering doing business with the government? Here are four reasons you should get started on FedRAMP compliance ASAP.
The Ability to Sell to the Federal Government
FedRAMP is mandatory for all cloud services used by government agencies. Achieving authorization will allow you to tap into the booming federal cloud market.
Meet Multiple Government Agencies Requirements
A FedRAMP security authorization can be reused across multiple agencies: FY 2021 saw a 45% increase in the amount of FedRAMP-authorized security packages reused by agencies, indicating that the “certify once, use many” vision of the program has become a reality.
Differentiate with a Valuable Marketing and Sales Tool
FedRAMP is recognized as the pinnacle of cloud security certifications, which means it can be a valuable cybersecurity proof point when you are selling to the private sector, too. A news search of “FedRAMP authorization” yields countless press releases illustrating the pride CSPs take in this compliance achievement.
Achieve FedRAMP Authorization from a Top Assessor
For CSPs, there is no better time to earn FedRAMP authorization than right now. The federal cloud market is soaring with no signs of slowing down, as many agencies are still in the early stages of their cloud maturity journey.
As one of the top five FedRAMP assessors in the world, A-LIGN can help with any of your needs including advisory services or an official assessment paired with continuous monitoring.
Have a follow up question or would like to learn more about undergoing a FedRAMP assessment with A-LIGN? Reach out to one of our experienced FedRAMP specialists.