What is StateRAMP and How Does It Relate to FedRAMP?
StateRAMP provides a comprehensive security framework designed to improve cloud security for state and local governments. Learn the ins and outs of the StateRAMP compliance framework, its relationship with FedRAMP and how StateRAMP could impact your business.
As cyberattack attempts carried out against state and local governments continue to become more prevalent, government agencies are in dire need of a way to modernize and systematize their cybersecurity practices — especially regarding cloud technologies. That’s where the State Risk and Authorization Management Program (StateRAMP) comes in.
According to Comparitech, various ransomware attacks cost the U.S. government close to $19 billion in 2020. And recent ransomware attacks on state-run facilities have highlighted the importance of increased and improved cybersecurity measures for state and local governments.
StateRAMP provides a comprehensive security framework designed to improve cloud security for state and local governments. It delivers a uniform approach to verifying that cloud service providers (CSPs) meet the standards and regulations needed to do business with state and local governments.
As I outline the details of the StateRAMP compliance framework and its relationship with the Federal Risk and Authorization Management Program (FedRAMP), you will see how, and if, this could impact your business.
The StateRAMP and CSP Relationship
As mentioned above, StateRAMP was created to help state and local government agencies manage and verify the cybersecurity posture of third-party vendors that provide cloud technology solutions, also known as CSPs. This is important because CSPs have been replacing on-premise information technology (IT) solutions at a rapid rate over the past 10+ years.
CSPs offer government agencies cloud computing solutions and services like Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS), all of which are designed to improve an organization’s agility and scalability. Gaining advanced storage, computing, and analytics capabilities has become essential for many government agencies to increase collaboration and remote accessibility while gaining deeper insights into their data.
As government agencies adopt StateRAMP to enhance their cybersecurity posture, CSPs that respond to RFPs in those states will need to prove they are StateRAMP authorized. This will be a requirement for any CSP proposals to be considered by certain local government agencies.
StateRAMP’s Solution for State-based Cybersecurity
The StateRAMP framework was created by the StateRAMP non-for-profit organization in response to the encroaching cyber threat crisis that stands to disrupt modern life in unprecedented ways. According to StateRAMP, the program’s purpose is to:
- Help state and local governments protect citizen data.
- Save taxpayer and service provider dollars with a “verify once, serve many” model.
- Lessen the burdens on government.
- Promote education and best practices in cybersecurity among those it serves in industry and government communities.
Protecting Citizen Data
In the recent onslaught of ransomware attacks, it is frequently citizen data that’s held hostage by threat actors who demand a payout. This data is often personal identifiable information (PII) that, if exposed, can allow hackers to commit identify theft or monetize the stolen data on the dark web.
Because state and local government officials are elected to serve the needs of their citizens, keeping personal data safe is a major priority.
Verify Once, Serve Many
StateRAMP makes things easier for CSPs by allowing them to transfer their credentials and certifications across a set of uniform standards. The “verify once, serve many” model was designed so CSPs only need to have their cloud offering or product authorized once to confirm its cybersecurity standards are adequate. This authorization is then enough to be recognized by other government agencies that adopt StateRAMP.
Government employees and officials are able to join StateRAMP at no cost as the program is entirely vendor-funded. This ensures enhanced cybersecurity is accessible for all state and local government agencies, regardless of size or budget.
Lessening the Burden on Government
Related to the last point, the StateRAMP model alleviates strain on state and local governments by removing the need for them to conduct redundant security assessments. In addition to being cost efficient because StateRAMP removes the need for repetitive CSP security assessments, it saves countless hours and staffing needs that could be better utilized elsewhere.
For example, before StateRAMP, a government agency might have to review a dozen CSP vendors that responded to an RFP, even if they knew only a few of them would likely have acceptable cybersecurity standards in place. With StateRAMP, governments don’t have to waste valuable resources doing assessments for organizations that are severely lacking in cybersecurity maturity.
Promoting Cybersecurity Education and Best Practices
In the constantly evolving landscape of cybersecurity and compliance, it can be tough to stay up to date on the latest developments and regulations. StateRAMP aims to be as transparent as possible about policies and procedures, making cybersecurity knowledge available for anyone who wants to learn. In fact, the StateRAMP website provides a wealth of documents, templates, and other resources related to StateRAMP compliance.
After all, StateRAMP was designed to ensure government agencies and CSPs truly understand the reasoning and mechanisms behind the StateRAMP framework.
How Does StateRAMP Work?
Much like FedRAMP was created to provide a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services that store, process and transmit federal information, StateRAMP was designed to do the same for state and local government agencies.
StateRAMP’s Security Assessment Framework process is modeled after the National Institute of Standards and Technology (NIST) Risk Management Framework. Its primary requirements for CSPs seeking authorization include:
- Compliance with the security standards listed in NIST Special Publication 800-53 Rev. 5.
- A relationship with a Third-Party Assessment Organization (3PAO) that serves as a partner and educator throughout the entire process.
- Producing an in-depth security report in collaboration with a 3PAO that proves the organization has all the necessary controls in place and meets all requirements for authorization.
- Participating in continuous monitoring to demonstrate that the organization continues to maintain StateRAMP compliance.
To have a cloud offering or product become StateRAMP authorized, CSPs must work with their 3PAO to identify their impact level category based on the type of government data they handle, and the consequences that would result if a breach were to occur.
Each of the four categories corresponds with a defined set of security controls which align with familiar FedRAMP impact levels:
- Category 1 – This is the baseline any CSP has to meet. It maps to systems that involve publicly available data. Category 1 aligns with the “low” impact level in FedRAMP.
- Category 2 – This category covers data that is not available to the public, such as PII. Category 2 aligns with the “low” impact level in FedRAMP and contains some elements of the “moderate” impact level control baselines. Category 2 will continue to be developed and validated throughout this year.
- Category 3 – This category involves confidential data and systems that are of high criticality to the continuity of government. Category 3 aligns with the “moderate” impact level in FedRAMP.
- Category 3+ – This category is reserved for FedRAMP High authorized systems for reciprocity with StateRAMP.
StateRAMP also provides an official data classification tool that includes a brief survey to help government agencies determine what StateRAMP security category requirements they need to include in their RFPs. This tool can also help CSP better understand the StateRAMP security categories and what they entail.
Why Is StateRAMP Necessary?
With so much overlap between StateRAMP and FedRAMP frameworks, you may be thinking, “Why doesn’t a CSP just seek FedRAMP authorization for their products and achieve the same security outcome?”
It’s a fair question. FedRAMP built a reputation as a model security program over the past 10 years and has authorized hundreds of cloud products. Prior to this year, many CSPs that offered cloud solutions to state and local government agencies found themselves using FedRAMP security guidelines, but were still unable to achieve official FedRAMP authorization. This is because FedRAMP was specifically designed for federal agencies. This means organizations cannot obtain FedRAMP authorization without doing business with the federal government.
For this reason, a coalition of industry members decided to form the StateRAMP not-for-profit organization to bring FedRAMP’s standardized cloud security approach to state and local governments. As a growing number of states plan to join StateRAMP (the StateRAMP organization is in talks with hundreds of government officials across 35 states and counting), it would be wise for CSPs to start preparing for StateRAMP authorization sooner rather than later.
In addition to enhancing cybersecurity by providing a uniform approach to risk-based management, accomplishing StateRAMP authorization can help CSPs save time and resources by allowing them to re-use their security authorization across multiple government agencies. StateRAMP also increases transparency and trust between government agencies and CSPs, reducing the likelihood of any miscommunication, oversights, or errors that could affect potential contracts or working relationships.
Note: For CSPs that do business with both federal and state/local government and are already FedRAMP authorized, a reciprocity program is in process that will allow these organizations to take an accelerated path to StateRAMP authorization.
Get Started with StateRAMP
In a time when the public and private sectors are realizing they must work together to keep out threat actors, StateRAMP is a significant milestone for transparency, standardization, and community in cybersecurity.
If your organization requires StateRAMP authorization to do business with a state or local government agency, A-LIGN can help put you on the right track. Drawing from our extensive experience as a 3PAO for FedRAMP, A-LIGN is one of the only StateRAMP-registered assessors on the market today. Contact us to learn more about how you can get started with StateRAMP.
If your organization currently serves, or is seeking to serve, cloud products or solutions to a federal agency then you already know you must undergo a Federal Risk and Authorization Management Program (FedRAMP) assessment. The experts at A-LIGN have put together a comprehensive FedRAMP Authorization guide to help you prepare for the assessment.
Created in 2011, FedRAMP provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services relied upon by federal entities that store, process, and transmit federal information. The goal of FedRAMP is to provide a set of agreed-upon standards to be used for cloud product approval.
Once you’ve secured agency sponsorship and developed a System Security Plan (SSP) based on your defined categorization level (Low, Moderate, or High), it’s time to work with a FedRAMP 3PAO to perform your Security Assessment. That’s where A-LIGN comes in. A-LIGN is an accredited FedRAMP 3PAO (third-party assessment organization) and one of the top 3 FedRAMP assessors in the world.
Here is a look at the step-by-step process you’ll need to complete to earn FedRAMP authorization with A-LIGN.
Before you begin
This article is intended for companies that have already secured a sponsor and developed an SSP. If you haven’t yet done that, we recommend you take some time to research the FedRAMP process and potentially conduct a FedRAMP readiness assessment.
Research
At A-LIGN, we recommend organizations review the following materials to ensure they have a baseline level of knowledge to help prepare for the FedRAMP assessment process:
- Everything You Need to Know About FedRAMP
- 3 Tips to Prepare for FedRAMP Authorization
- FedRAMP: Understanding the Fundamentals (FAQ)
- FedRAMP for Cloud Service Providers – Top 4 Questions Answered
- CSP Authorization Playbook: Getting Started with FedRAMP
- FedRAMP Security Controls Baseline
- FedRAMP Marketplace Designations for Cloud Service Providers
- FedRAMP Initial Authorization Package Checklist
Readiness assessment
Organizations that are familiar with the controls within NIST 800-53, and are FISMA certified, can jump right into the FedRAMP process. If you are not familiar with FISMA or FedRAMP, and have never written a system security plan, we recommend that you perform a FedRAMP readiness assessment, or gap assessment, to determine your level of readiness for the 3PAO assessment.
A-LIGN can conduct a readiness assessment for you, in which we will review your environment and determine if it is technically capable of meeting FedRAMP requirements. This is a great way to get a pulse on your current environment before investing time and resources into a full assessment.
Step 1. Pre-assessment review (1-4 weeks)
If you are ready for an official assessment and have signed a contract with A-LIGN, then we’ll kick off our work with a pre-assessment review phase. During this phase, you will finalize the Cloud Service Offering System Security Plan — which you previously developed — and provide the SSP package (including all attachments) to A-LIGN for review.
We will use that information to perform a FedRAMP Pre-Assessment Review. During this review, we’ll ensure we have everything we need to proceed with the assessment without any delays. Keep in mind that the quality of the evaluation is dependent on the accuracy and volume of information you provide to us. The more you can provide, the better.
Once the review is complete and it has been determined you are ready for the FedRAMP assessment, we will schedule a kick-off meeting with you, and our team at A-LIGN to plan out the full assessment.
Step 2. Planning activities (4 weeks)
After the Pre-Assessment Review phase, you will need to submit responses to the initial Information Request List (IRL) that A-LIGN provides. While you are working on the IRL responses, we will submit a few materials to your sponsor to review. These include:
- An Authority to Test (ATT) – This is part of our penetration test planning.
- A Security Assessment Plan (SAP).
Step 3. Assessment activities (7 weeks)
This is the longest phase of the FedRAMP process and consists of fieldwork. The fieldwork is split into phases where we interview members of your team about your cloud service offering and the security controls implemented and review the evidence confirming the proper implementation of FedRAMP security requirements. Keep in mind that we do not begin our evidence review until at least 90% of the IRL evidence is provided by your team. It’s important to plan ahead, so we can stay on schedule throughout the assessment process and avoid delays.
We will also conduct a penetration test at this time. The penetration test is required for all FedRAMP Authorization assessments for Moderate and High impact systems. Although the penetration test is not a requirement for FedRAMP Ready assessments, it is recommended as a safety net to eliminate any surprises we may encounter during the actual authorization testing.
Once we conduct the penetration test and get through a majority of the evidence review, we will analyze and discuss the findings with your team via a draft risk exposure table (RET). Once that draft RET is provided to your team, you can create a plan of action and milestones (POA&M) to remediate these issues.
Step 4. Reporting activities (5 weeks)
Upon completion of our full evidence review and penetration test and any remediation to correct findings outlined in the draft RET, a draft Security Assessment Report and penetration test report will be provided for review.
We will analyze and discuss the findings with your team after the remediation period and before drafting a report for you. Once the final report is complete, it will be sent to your Sponsor who will review the SSP and the SAR together.
Step 5. Sponsor issues authority to operate (2-3 weeks)
After the Sponsor completes their review, the Sponsor will issue an ATO and the FedRAMP Authorization Package will be sent to FedRAMP to review. Once FedRAMP’s review is complete, you will get your cloud solution offering’s official designation as a FedRAMP Authorized. FedRAMP will list your cloud solution offering as “Authorized” on the FedRAMP marketplace.
Step 6. Maintain authorization
It’s important to remember that FedRAMP authorization is not a set-it-and-forget-it process. Ongoing assessments are required to maintain FedRAMP authorization, as annual assessments are required along with meeting FedRAMP continuous monitoring requirements with your Sponsor.
The A-LIGN team can provide annual assessments (including penetration testing, control assessments, systems scanning, and more) to ensure your cloud solution offering maintains FedRAMP compliance.
We can also conduct one-off assessments to ensure compliance after your organization undergoes major changes (like an acquisition). During a “Significant Change Request Assessment,” we will review and assess any significant changes that may impact your compliance with FedRAMP requirements.
Get Started with A-LIGN
At A-LIGN, we are one of the top FedRAMP assessors in the world, with a 96% satisfaction rating from our customers. Our experts can help you through every step of the process — from a readiness assessment to final authorization.
Contact A-LIGN today to learn more about our FedRAMP services.
There are four different baselines and impact levels of FedRAMP authorization: Low Impact SaaS (FedRAMP Tailored or LI-SaaS), Low, Moderate, and High impact. These categories differ based on the number of control sets each has as its baseline.
The majority of FedRAMP-authorized organizations pursue Moderate authorization. But today, more and more cloud service providers (CSPs) are looking to move from their Moderate authorization to a High authorization. This higher authorization allows organizations to work with government entities that require more stringent protocols to protect the Federal government’s most sensitive unclassified data.
Along with opening the door to more business opportunities, higher impact levels can make an organization look more attractive to clients. A higher impact level highlights an organization’s stringent adherence to specific cybersecurity controls, which can provide an extra level of reassurance for clients.
Here’s how organizations can move from the Moderate impact level to the High impact level.
FedRAMP Impact Levels Explained
The Federal Risk and Authorization Management Program, or FedRAMP, is the U.S. Federal government’s internal approach to securing the cloud services that its agencies use. FedRAMP grants authorizations at four impact levels: Low Impact SaaS (FedRAMP Tailored or LI-SaaS), Low, Moderate, and High. Each level has different control sets as its baselines:
- Low Impact SaaS (FedRAMP Tailored or Ll-SaaS): Ll-SaaS is a subset of low impact and typically includes at least 50 of the controls to be independently assessed. This tailored baseline accounts for SaaS applications that do not store personal identifiable information beyond what’s required for login capability, such as usernames and passwords. Therefore, organizations that achieve the LI-SaaS level would only experience minor adverse effects should a loss of confidential information occur. Information about the security controls required for this designation can be found here.
- Low Impact Level: Low includes approximately 125 controls. Organizations that achieve the low authorization status would only experience limited adverse effects should a loss of confidential information occur. Information about the security controls required for this designation can be found here.
- Moderate Impact Level: Moderate includes approximately 325 controls. Nearly 80% of organizations that receive FedRAMP authorization fall into this category. The loss of confidential information in this category would have a serious — but not catastrophic — impact on an organization. Information about the security controls required for this designation can be found here.
- High Impact Level: High includes approximately 425 cybersecurity controls. Organizations that should seek a High ATO most commonly include those working in law enforcement and emergency services systems, financial systems, and health systems. However, any organization can achieve the High impact level authorization, and they should especially pursue this level if any loss of confidential information could be expected to have a catastrophic impact on the organization. Information about the security controls required for this designation can be found here.
The Process of Moving from FedRAMP Moderate to FedRAMP High
The process of moving impact levels is relatively straightforward and is also simpler than achieving initial FedRAMP authorization. The three main steps that organizations need to take to move up an impact level include:
- Receive approval from your sponsor. To begin the process of moving to a higher impact level, you first need permission from your sponsor. Identify a new sponsoring agency if the existing sponsor does not want to maintain sponsorship for a High authorization.
- Complete the Significant Change Request (SCR) Form. This document, which is published on the FedRAMP website, outlines all of the additional control requirements that would need to be met to move up an impact level. The form includes a checklist of the new controls required when changing from Moderate to High impact levels and identifies those Moderate controls that change under a High impact level.
- Undergo a Significant Change Assessment. Finally, an organization should complete a Significant Change Assessment with a third-party authorization organization (3PAO). It is suggested, if applicable, to perform the Significant Change Assessment during your Annual Security Assessment for continued Authorization. This would help reduce audit fatigue that can result from doing an out-of-cycle assessment and help control time and cost.
How A-LIGN Can Help You Move from FedRAMP Moderate to FedRAMP High
Even if an organization isn’t actively handling federal data, it can still use FedRAMP’s impact levels as a baseline to evaluate cloud security standards. Moving from FedRAMP Moderate to FedRAMP High means an organization has increased the number of controls it uses to keep sensitive information secure — something that can be attractive to clients.
As an accredited 3PAO, A-LIGN is one of the top FedRAMP assessors in the world. We help organizations achieve FedRAMP Authorized and move to a higher impact level.
8 Questions to Ask Your SOC 2 Auditor Before Signing a Contract
A SOC 2 is a third-party review that attests to an organization’s ability to protect data and information. In a world where data breaches and cyberattacks are on the rise, a SOC 2 report is a valuable tool to:
- Increase insight into your organization’s security posture
- Understand opportunities for control improvements
- Position your company more competitively in your market (prospects want to ensure your organization takes security seriously)
There are a lot of vendors out there that cater to different aspects of the SOC 2 process — from software providers who help you get audit-ready to certified auditors from CPA firms who can test your environment and issue a final SOC 2 report. Ideally you will want to find a firm that can take you all the way from SOC 2 readiness to report.
Use this checklist of important questions to vet your SOC 2 auditor before signing a contract. Following this checklist will help you complete a thorough due diligence process to ensure that you partner with the right team and get the most out of your audit.
1. Are you a licensed CPA firm?
SOC 2 audits are regulated by the American Institute of Certified Public Accountants (AICPA) and must be completed by an external auditor from a licensed CPA firm. This is the only way a company can receive an official SOC 2 report. It’s important to confirm that the SOC 2 vendor you are considering working with has the proper accreditation.
2. Can you provide us with a final report?
If you are considering using a SOC 2 compliance software provider, it’s important to confirm that they also provide audit services that will result in a SOC 2 report, ideally without having to shift your information to another vendor in the middle of the audit process.
As discussed above, a final report can only be issued by an auditor from a licensed CPA firm. Many SOC 2 software providers only offer a solution to assess your readiness to complete a SOC 2 audit — they cannot perform and/or issue the SOC 2 audit and report itself.
If you choose to work with a software provider, you must ensure that they also have certified auditors on-staff. Otherwise, you’ll need to sign on a secondary vendor to complete the actual audit. This is not recommended, as it leaves too much room for things to be “lost in translation” between the two entities leading to wasted resources and delayed audit and report timelines.
A-LIGN offers an end-to-end compliance solution — with a SaaS automation compliance platform to help you complete a readiness assessment and streamline the entire audit process, as well as certified auditors to produce a final report. This creates efficiencies while maintaining control of your environment.
3. Do you offer SOC 2 readiness services?
A SOC 2 readiness assessment is a valuable tool to help you understand your company’s position before completing an official audit. A readiness assessment can help you identify gaps in your cybersecurity procedures (and the severity of those gaps) that need remediation before a SOC 2 audit. This will ultimately help you save time, set priorities, and put your company in a better position to perform well during the SOC 2 audit.
Companies like A-LIGN provide readiness services via automated software — which offers easy-to-read dashboards outlining gaps and priorities, and provides tips to navigate the audit process better.
4. What is the timeline of a SOC 2 examination?
Many software providers tout they can complete a SOC 2 audit in 14 days. It’s important to clarify this statement before signing a contract. A lot of times, the two-week timeline is an estimate for an expedited evidence collection process — but evidence collection is only one step in the SOC 2 audit process and does not result in a full audit or final report.
Ask your vendor for a complete timeline and have them outline their step-by-step process for moving through the SOC 2 audit. This is essential for you to resource appropriately. It’s also crucial to know when you can expect to have a report in hand so you can properly communicate with prospects who ask about a SOC 2 report during the sales process.
5. What does the evidence collection process entail?
The evidence collection process varies significantly based on the scope of your audit. Often it can include hundreds of requests for evidence.
We recommend using compliance automation audit software to streamline the evidence collection process and organize assets. Ask your vendor if they provide software to assist in this process.
At A-LIGN, our A-SCEND platform automatically collects evidence via cloud integration APIs.
Once collected, A-SCEND creates readable reports that are mapped to corresponding evidence requests from the “information request list” (provided earlier in the audit process). This helps you see what information is already collected and what else your team still needs to gather and provide.
Automated software significantly reduces the time it takes to collect, share, and analyze evidence. With A-SCEND, this information can also be stored and re-used to help complete other audits, saving your organization’s money and resources.
6. How many SOC 2 audits have you completed to date?
There is no substitute for experience. Choosing a seasoned SOC 2 auditor will be the difference between a fast and painless audit process that results in a reputable final report and being issued a piece of paper that no one accepts.
In addition to asking about the number of audits completed to date, you can also get a sense of a company’s experience based on the resources and information they provide about the SOC 2 process on their website. A trusted, experienced partner will be able to provide you with plenty of information to educate you about the SOC 2 process and detailed information about their services and tools.
7. In what industries do you have experience?
You’ll want to ensure your SOC 2 auditor is familiar with the ins and outs of your industry, so they understand how the SOC 2 criteria fit your organization. Plus, many elements of SOC 2 overlap with those of other necessary, industry-specific audits. If your auditor has experience in the healthcare sector, for example, they’d be familiar with the overlap between SOC 2 and HIPAA (Healthcare Insurance Portability and Accountability Act) compliance. They may be able to offer you a SOC 2 + HIPAA combined security assessment. This would allow you to complete both audits simultaneously while saving time and resources.
8. What other services do you provide that could help as we continue to grow as a company?
SOC 2 is just one of the many important audits and assessments in the world of compliance and cybersecurity. It’s common for companies who complete a SOC 2 audit to pursue other compliance priorities as well.
Plus, as mentioned above, SOC 2 overlaps with other audit criteria. Completing a SOC 2 audit positions you well to pursue other complementary certifications. Look for a vendor that offers other audits, attestations, and assessments so you can create a long-term partnership that meets all your cybersecurity and compliance needs. It’s advantageous to build a relationship with one vendor, so as not to duplicate efforts related to evidence collection and fieldwork.
From Readiness to Report with Trusted SOC 2 Auditors
A-LIGN is a licensed CPA firm and the top issuer of SOC 2 reports in the world. We have completed more than 5,000 SOC 2 audits and employ over 170+ SOC 2 auditors located around the world.
In addition to the expertise of our auditors — and our deep experience — we also offer a compliance automation software solution. A-SCEND streamlines the evidence collection process and provides you with all of the tools you need to successfully complete a SOC 2 audit, from readiness to report.
Contact us today to learn more about A-LIGN’s SOC 2 services.
In today’s security landscape, it’s crucial you assure your customer and partners that you are protecting their valuable data. SOC 2 compliance is the most popular form of a cybersecurity audit, used by a growing number of organizations to prove they take cybersecurity seriously. A SOC 2 report will provide you with a competitive advantage in the marketplace while allowing you to close deals faster and win new business.
Below we provide everything you need to know about a SOC 2 audit and final report. Let’s jump in!
What is SOC 2?
A Service Organization Controls (SOC) 2 audit examines your organization’s controls in place that protect and secure its system or services used by customers or partners. The security posture of your organization is assessed based on the requirements within the SOC 2 framework, known as the Trust Services Criteria (TSC).
What is the AICPA and why does it matter in SOC 2?
The American Institute of Certified Public Accountants (AICPA) organization is the governing body of the SOC framework and set the U.S. auditing standards that auditors use for SOC 2 examinations. When you complete the SOC 2 attestation and receive your final report, your organization can download and display the logo issued by the AICPA.
Why is SOC 2 compliance important?
It’s important for customers and partners to know that your organization will protect their data and the best way to demonstrate this is through an independent, reliable source. In today’s landscape, a SOC 2 is considered a cost of doing business because it establishes trust, drives revenue and unlocks new business opportunities.
Bonus- Oftentimes, a SOC 2 report is an acceptable alternative to the time-consuming, 500-question security survey!
What are the key benefits of SOC 2 compliance?
Organizations who complete a SOC 2 assessment will benefit from the following:
- Valuable insight into your security posture
- A strategic roadmap for cybersecurity investments and initiatives
- Increased competitive positioning in the marketplace
How can a SOC 2 report help small businesses scale?
Your startup or small business will need a SOC 2 report to go upmarket and close large deals. Below are some of the benefits you will notice after earning a SOC 2 report.
- Development of strong policies and procedures
- Increased credibility with investors and partners
- A strong competitive advantage
- Saved time, money and resources on a potential data breach
Who uses a SOC 2?
Service organizations that process, store, or transmit data for their clients or partners. While SOC 2 applies to almost any organization, it’s particularly important to data centers, software-as-a-service (SaaS) companies, and managed service providers (MSPs).
Who can perform a SOC audit?
All SOC 2 audits must be completed by an external auditor from a licensed CPA firm. If you plan to use a software solution to prepare for an audit, it’s helpful to work with a firm who can provide both the readiness software, perform the audit and produce a reputable SOC 2 report.
What are the SOC 2 Trust Service Criteria?
The security posture of your organization is assessed based on SOC 2 requirements, known as the Trust Services Criteria (TSC). You can decide which of the five (5) TSC you would like to include in your audit process as each category covers a different set of internal controls related to your information security program. The five TSC categories are as follows:

Security (required)
- The Security Category is required and assesses the protection of information throughout its lifecycle and includes a wide range of risk-mitigating solutions.
Availability (optional)
- The Availability Category reviews controls that show your systems maintain operational uptime and performance to meet your objectives and service level agreements (SLAs).
Confidentiality (optional)
- The Confidentially Category examines your organization’s ability to protect information throughout its lifecycle from collection, to processing and disposal. This is particularly important if you’re storing sensitive information protected by Non-Disclosure Agreements (NDAs) or you’re required to delete information after processing.
Processing Integrity (optional)
- The Processing Integrity Category ensures the data your organization processes is free of accidental or unexplained errors.
Privacy (optional)
- The Privacy Category reviews the Personally Identifiable Information (PII) that your organization captures from customers, such as social security numbers, birthdays, etc.
Note- the more TSC categories you’re able to include in your audit, the more you’re able to better your security posture!
What are the top policies and procedures needed for a SOC 2 audit?
To start preparing for your SOC 2 examination, begin with the 12 policies listed below as they are the most important to establish when undergoing your audit and will make the biggest impact on your security posture.
- Information Security Policy
- Access Control Policy
- Password Policy
- Change Management Policy
- Risk Assessment and Mitigation Policy
- Incident Response Policy
- Logging and Monitoring Policy
- Vendor Management Policy
- Data Classification Policy
- Acceptable User Policy
- Information, Software and System Policy
- Business Continuity and Disaster Recovery
For further details on each individual policy and produce, visit SOC 2: The Definitive Guide.
What are SOC 2 controls?
SOC 2 controls are a collection of policies, procedures, and directives dictating the operation of an organization’s systems, ensuring the security, availability, processing integrity, confidentiality, and privacy of both company and customer data. These guidelines aid organizations in managing and safeguarding sensitive information, fostering the implementation of robust security measures and mitigating the likelihood of data breaches and ensuring adherence to regulatory mandates.
How to start a SOC 2 audit
Before starting the SOC 2 audit process, it is important that you’re well-prepared to avoid any lengthy delays or unexpected costs. Prior to beginning your SOC 2 audit, we suggest you follow the below guidelines:
- Undergo a SOC 2 readiness assessment to identify control gaps that may exist and remediate any issues
- Decide which Trust Service Criteria to include in your audit that best align with your customer’s needs
- Choose a compliance automation software tool to save time and cost. Pro tip- select a licensed CPA firm that also offers compliance automation software for an all-in-one solution and seamless audit process that doesn’t require you to switch vendors mid-audit.
During the initial stage of the audit process, it’s important that your organization follow the below guidelines:
- Review recent changes in organizational activity (personnel, service offerings, tools, etc.)
- Create a timeline and delegate tasks (compliance automation software will make this activity much less time consuming)
- Review any prior audits to remediate any past findings
- Organize data and gather evidence ahead of fieldwork (preferably with automated evidence collection)
- Review requests and ask any questions (pro tip- it’s important to choose an experienced auditing firm that’s able to answer questions throughout the entire audit process)
What is compliance automation software?
If you’re looking for SOC 2 software, compliance automation software may be the best solution. Compliance automation software allows users to consolidate all audit information into a single system to gauge readiness, collect evidence, management requests and continually monitor your security posture.
When selecting a compliance automation software it is recommended that you look for one that offers:
- Automated readiness assessments
- Automated evidence collection
- Policy templates
- Auditor assistance when needed
- Cloud integrations
- Project dashboard
- Consolidated audit requests
- Continuous monitoring
It’s important to note that compliance automation software only takes you so far in the audit process and an experienced auditor is still needed to conduct the SOC 2 examination and provide a final report.
What’s the timeline of the SOC 2 audit process?
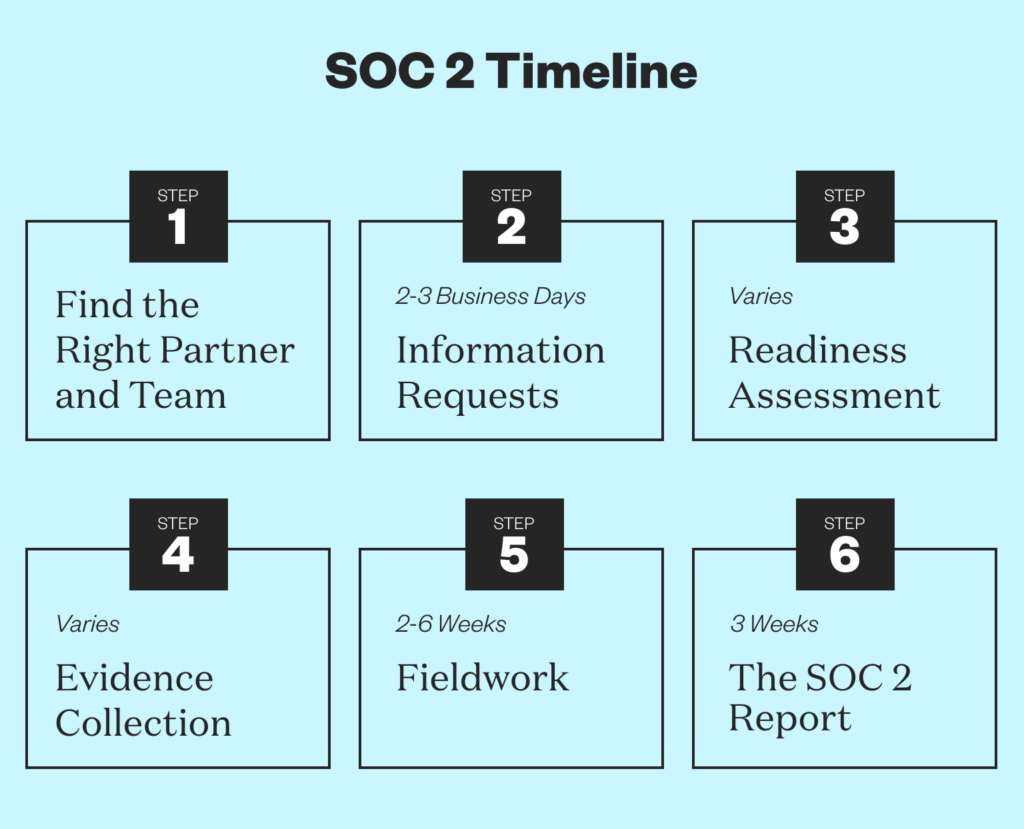
SOC 2 timelines vary based on the company size, number of locations, complexity of the environment, and the number of trust services criteria selected. Listed below is each step of the SOC 2 audit process and general guidelines for the amount of time they may take:
Step 1: Find the Right Partner and Team
A SOC 2 must be completed by a licensed CPA firm. If you choose to utilize compliance automation software, it’s recommended that you select an auditing firm that also offers this software solution for a more seamless audit.
Step 2: Information Requests: Estimated Timeline: 2-3 Business Days
Your audit team will generate an Information Request List (IRL) for your organization. The information in this list is based on the scope, the chosen Trust Service Criteria, and other factors such as cloud hosting services, locations, and company size.
Step 3: Readiness Assessment: Estimated Timeline: Varies based on scope
If it’s your first audit, we recommend completing a SOC 2 Readiness Assessment to find any gaps and remediate any issues prior to beginning your audit.
Step 4: Evidence Collection for a SOC 2 Audit: Estimated Timeline: Varies
The time it takes to collect evidence will vary based on the scope of the audit and the tools used to collect the evidence. Experts recommend using compliance software tools, like A-SCEND, to greatly expedite the process with automated evidence collection.
Step 5: Fieldwork: Estimated Timeline: 2-6 Weeks
This phase includes walkthroughs of your environment to gain an understanding of your organization’s controls, processes and procedures. The time it takes to complete this phase will vary based on your scope, locations, TSCs, and more but generally, most clients complete in two to six weeks.
Step 6: The SOC 2 Report: Estimated Timeline: 3 Weeks
The audit team will provide a SOC 2 report for your company that comes in two parts. Part one is a draft within three weeks of completing the fieldwork in which you’ll have the opportunity to question and comment. Part two is a final report two weeks after the draft has been approved with the inclusion of the updates and clarifications requested in the draft phase.
What’s the difference between SOC 2 Type I and Type II?
When determining what type of SOC 2 assessment to undergo you will have two options resulting in two different reports, a SOC 2 Type 1 audit and a SOC 2 Type 2 audit. There are two main differences between the different audit types. The first is the duration of time in which the controls are evaluated. A SOC 2 Type 1 audit looks at controls at a single point in time. A SOC 2 Type 2 audit looks at controls over a period of time, usually between 3 and 12 months.
In addition, SOC 2 Type 2 audits attest to the design, implementation, and operating effectiveness of controls. A Type II provides a greater level of trust to a customer or partner as the report provides a greater level of detail and visibility to the effectiveness of the security controls an organization has in place.
What’s the difference between SOC 1 and SOC 2?
The difference between SOC 1 and SOC 2 is that a SOC 1 audit addresses internal controls over financial reporting. A SOC 2 audit focuses more broadly on information and IT security. The SOC 2 audits are structured across five categories called the Trust Services Criteria and are relevant to an organization’s operations and compliance.
What is a SOC 3 report?
To be issued a SOC 3 report, you must have first earned a SOC 2 report. A SOC 3 report is a public-facing version of the SOC 2 report intended for distribution and/or publication without the need for a non-disclosure agreement (NDA). A SOC 3 report is a SOC 2 report that has been scrubbed of any sensitive data and provides less technical information making it appropriate to share on your website or use as a sales tool to win new business.
What’s the difference between SOC 2 and ISO 27001?
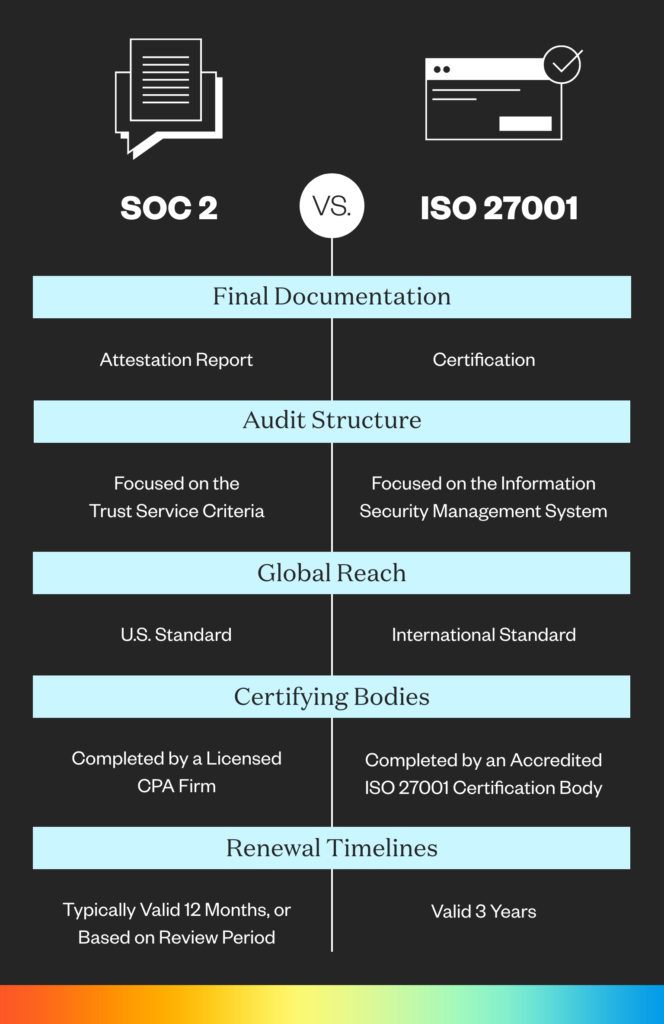
Both a SOC 2 report and ISO/IEC 27001:2013 certification are extremely attractive to prospective customers. Below are the major differences:
Certification vs. Attestation: ISO 27001 is a certification issued by an accredited ISO certification body and includes an IAF (The International Accreditation Forum) seal. SOC 2 is an attestation report provided by a third-part assessor such as a CPA firm.
ISMS vs. Trust Services Criteria: ISO 27001 is a pass/fail audit focused on the development and maintenance of an Information Security Management System (ISMS). SOC 2 is structured around the five Trust Service Criteria and includes an auditor’s opinion of the controls in place for each chosen TSC. A final SOC 2 report is much more detailed than the one-page letter that you receive with an ISO 27001 certification.
Global Reach: ISO 27001 is an international standard throughout the world while SOC 2 is primarily US-based. Note- while SOC 2 is American-born, it’s important for any organizations doing business in the US, and is rapidly gaining traction in Europe.
Certifying Bodies and Renewal Timelines: SOC 2 attestations are carried out by a licensed CPA firm and valid for 12 months. ISO 27001 certifications are carried out by an accredited ISO 27001 certification body and are valid for three years with annual surveillance audits.
Can you fail a SOC 2 examination?
No, you cannot “fail” a SOC 2 audit. It’s your auditor’s job during the examination to provide opinions on your organization within the final report. If the controls within the report were not designed properly and/or did not operate effectively, this may lead to a “qualified” opinion. This indicates that one of the SOC 2 criteria had testing exceptions that were significant enough to preclude one or more criteria from being achieved. Audit reports are crucial because they speak to the integrity of your executive management team and affect investors and stakeholders.
What should I do with my final report?
While you’re not able to publicly share your SOC 2 report unless under NDA with a prospective customer, there are ways you can utilize your SOC 2 assessment achievement for marketing and sales purposes.
- Announce earning your SOC 2 report with a press release on the wire and on your website. Then, share on your social media platforms!
- Showcase the AICPA badge you earned on your website, email footers, signature lines and more.
- Send a short email to customers announcing your SOC 2 report.
- Write a blog around earning your SOC 2 report and how this effort further demonstrates that you take your customer’s data security seriously.
- Teach your sales team how to speak about SOC 2 and the benefits it provides to customers.
If you would like a public-facing report to share, consider purchasing a SOC 3 report.
How long is my final report valid?
When you earn your final SOC 2 report, it’s generally valid for 12 months. Therefore, a SOC 2 audit should be conducted annually as an internal benchmark to assess your security posture year-over-year.
What are a few helpful SOC 2 resources?
SOC 1 vs SOC 2: What’s The Difference?
SOC 2 Framework: What You Need to Know
A Guide to SOC 2 Reporting: What Is a SOC 2 Report?
What are the SOC 2 Trust Services Criteria?
SOC 2 Compliance Requirements: An Overview
The Role of SOC 2 Auditors vs. Compliance Software
What’s an example of SOC 2 in the real world?
Below are several customer testimonials in which the organization earned a SOC 2 report to drive revenue, build customer trust and better their security posture.
Raindrop Earns SOC 2 Report with A-LIGN
ENSEK Earns a SOC 1 and SOC 2 Report, Building Customer Trust
MPS Monitor Demonstrates the Cybersecurity Gold Standard by Earning a SOC 2 Report
Plutoshift Utilizes A-LIGN to Earn SOC 2 Report and ISO 27001 Certification
Hifi Engineering Earns First SOC 2 Report
What is the history of SOC 2?
In 2010, the AICPA (The American Institute of Certified Public Accountants) introduced SOC 1 and SOC 2 to combat the growing need of companies to validate their cybersecurity posture.
Ready to start your SOC 2 audit?
SOC 2 can help you win more business and stand out from your competition. A-LIGN is the top issuer of SOC 2 audits in the world and has completed over 5,000 SOC 2 assessments. We provide the tools and expertise to help you during every step of the SOC 2 audit process — from readiness to report.
Ready to start your SOC 2 audit? Complete the below form to speak with an expert at A-LIGN.
Ransomware attacks are occurring more often, have become more harmful and now cost businesses a great deal of resources. A-LIGN’s 2022 Benchmark Report showed that of those surveyed, only 39% of organizations have a plan in place, whereas 40% are “planning to develop” something in the future, and 10% said they don’t view ransomware as a main cybersecurity concern. This gap is leaving businesses vulnerable to attacks. To help you best prepare for a cybersecurity event, we break down what goes into a ransomware preparedness assessment.

Contact A-LIGN to learn more about our one-of-a-kind Ransomware Preparedness Assessment.
How SOC 2 and ISO 27001 Create Business Value for Your Organization
For many, compliance is more than a legal necessity. More and more organizations now use compliance management as a way to create business value.
In our 2022 Compliance Benchmark Report, we surveyed more than 700 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs. Our findings indicated that an increasing number of organizations are now using SOC 2 reports and ISO 27001 certifications as a way to increase revenue and win new business.
The factors driving compliance programs
When we asked survey respondents about the key factors driving their organization’s compliance programs, the top three responses were:
- Increase revenue / win new business
- Meet board and C-level mandates
- Fulfill regulatory requirements
It’s no surprise that C-level mandates and regulatory requirements are a top driver of compliance programs. Executives and board members are legally required to oversee their organizations’ compliance programs, along with routinely taking action to mitigate compliance risks. Plus, several industries are legally required to abide by certain standards. HIPAA, for instance, is a federal law designed to ensure the security of healthcare patient data. 56% of our survey respondents were either planning, or already in the process of gaining, HIPAA compliance and 32% of respondents deemed HIPAA as one of their business’ most important services.
A whopping 63% of the organizations surveyed have conducted an audit or assessment to help increase revenue or drive new business. Organizations are continuing to take note of the strategic advantage compliance offers — as customers are increasingly concerned about cybersecurity risks and emboldened to ask partners for assurances that their data and information is secure.
Our team looked into what report or certification helps close the most deals and saw that SOC 2 is the most requested report or certification. That may be the reason why more than two-thirds of our survey respondents (67%, to be exact) said they were either currently completing a SOC 2 audit or had one scheduled within the next year.
The value of SOC 2 and ISO 27001
Applicable to all industries, SOC 2 and ISO 27001 are two of the most effective cybersecurity frameworks. Pursuing a SOC 2 report or an ISO 27001 certification (or both) can help increase trust with customers, prospects, and partners.
A SOC 2 audit is performed to ensure an organization is able to securely manage their data in order to protect the privacy of both the organization and its clients. Most customers and partners want to know the steps an organization is taking to protect their data and they want to see that their process is validated by a trusted, independent auditor.
Our experts recommend proactively completing a SOC 2 audit before a customer asks to see a report. Scheduling an audit and having a report on-hand when a prospect asks for one will prevent you from delaying important deals.
ISO 27001 is a certification organizations use to ensure they have an effective cybersecurity program in place. This international standard focuses on data confidentiality, integrity, and availability. Having an ISO 27001 certification showcases your organization’s commitment to data protection.
By building a culture of information security and diligence, organizations can reduce security incidents through implemented controls that are specific to their unique risks. Customers and partners will also feel more at ease entering a deal where the organization they want to work with has proven their dedication to risk management.
Unlock revenue through compliance
Cyberattacks remain on the rise and, despite looming economic uncertainty, organizations will continue to invest in partners who prove their commitment to cybersecurity. That’s why compliance audits and attestations continue to be a valuable differentiator for organizations looking to woo new clients — or simply protect their own data and information.
A-LIGN is the top issuer of SOC 2 reports in the world, having completed over 5,000 assessments for organizations across the country. We are also an accredited ISO 27001 certification body and can assist your company in leveraging compliance audits to strategically position you for success with customers and prospects.
Want to unlock revenue through compliance? Contact A-LIGN today!
Get started by downloading our ISO 27001 checklist.
A-LIGN’s Mike Herdegen Named Tampa Bay Business Journal’s 2022 CIO of the Year Honoree
Chief Technology Officer at A-LIGN Recognized as a Top Tampa Bay Executive in Information Technology
A-LIGN, the leading cybersecurity compliance and audit firm, today announced that the company’s Chief Technology Officer, Mike Herdegen, has been named a 2022 CIO of the Year honoree by the Tampa Bay Business Journal. This award recognizes top information technology executives and emerging leaders in Tampa Bay who are using innovative ways to create a competitive advantage and grow their companies.
Tampa Bay Business Journal’s CIO of the Year awards program is the most prestigious recognition of Tampa Bay’s top IT leaders and executives. CIOs and CTOs play a critical role in corporate success as technology continues to be a driving factor to operational success in the Tampa Bay business world. These leading executives’ roles daily expand and evolve from IT infrastructure, platforms, and cybersecurity to hardware and software development.
Herdegen is responsible for internal IT operations, ensuring A-LIGN operates against the highest standards for security in protecting information and system integrity. He also oversees the development of A-LIGN’s compliance management platform, A-SCEND, which enables customers to streamline their audits, save time and resources through automation, and demonstrate their security posture year-round.
“One of the reasons I came out of retirement to join A-LIGN was because of the organization’s values. A-LIGN has a culture of collaboration, expertise, integrity, and vision,” said Mike Herdegen, CTO at A-LIGN. “The A-SCEND features we are currently rolling out include market-leading new capabilities that keep pace with the rapidly-evolving expectations of our customers. At A-LIGN, support means exceptional service for our clients and opportunities for our employees, and we focus on people and technology to achieve both.”
The Tampa Bay Business Journal selected 2022 CIO of the Year honorees based on: accomplishments, leadership efforts, ethics in management and business practices, philanthropic contributions and involvement, significant projects spearheaded during the pandemic and over the past year, and how such initiatives have strengthened the company’s strategic market position.
Herdegen’s team of over 50 domestic and international IT professionals and developers have reimagined the A-SCEND product from an internal facing audit tool to an external facing solution to scale the organization’s footprint in the market as a leader in the cybersecurity service industry. The SaaS platform is purpose-built, performing end-to-end cybersecurity audits through the entire compliance process.
With an innovative single-provider, readiness-to-report approach, Herdegen’s primary goal over the last year and a half has been to transform A-SCEND into a cybersecurity platform that assists over three thousand clients in their compliance initiatives, and allows their audits to be as streamlined and successful as possible.
Outside of A-LIGN, Herdegen serves as the primary information technology resource at Think Big for Kids, helping underprivileged youth discover their untapped potential by bringing them exciting career exploration, mentorship, and skill development opportunities. Additionally, Herdegen is on the Tampa Bay Estuary Program’s (TBEP) Community Advisory Committee, responsible for judging the grants provided by TBEP and facilitating grant decision meetings.
To learn more about the team at A-LIGN, please visit our website.
For more information about TBBJ’s CIO of the Year honorees and awards and programs, visit
https://www.bizjournals.com/tampabay.
About A-LIGN
A-LIGN is the only end-to-end cybersecurity compliance solutions provider with readiness to report compliance automation software paired with professional audit services, trusted by more than 3,300 global organizations to help mitigate cybersecurity risks. A-LIGN uniquely delivers a single-provider holistic approach as a licensed CPA firm to SOC 1 and SOC 2 Audit services, accredited ISO 27001, ISO 27701 and ISO 22301 Certification Body, HITRUST CSF Assessor firm, accredited FedRAMP 3PAO, candidate CMMC C3PAO, PCI Qualified Security Assessor Company, and PCI SSC registered Secure Software Assessor Company. Working with growing businesses to global enterprises, A-LIGN’s experts and its compliance automation platform, A-SCEND, are transforming the compliance experience.
Media Contact:
Danielle Ostrovsky
Hi-Touch PR
410-302-9459
[email protected]
Zero trust is an important part of President Biden’s Executive Order (EO) on Improving the Nation’s Cybersecurity issued in May of 2021 and will continue to gain popularity as an effective cybersecurity solution. It focuses on restricting information access within an organization to only those who absolutely need to access the data. The entire point of zero trust is to assume that everyone is a potential threat actor and therefore, no internal or external users or systems are trusted.
In our 2022 Compliance Benchmark Report, we surveyed more than 700 cybersecurity, IT, quality assurance, internal audit, finance, and other professionals about their compliance programs. Here’s what we learned about how organizations are implementing zero trust strategies.
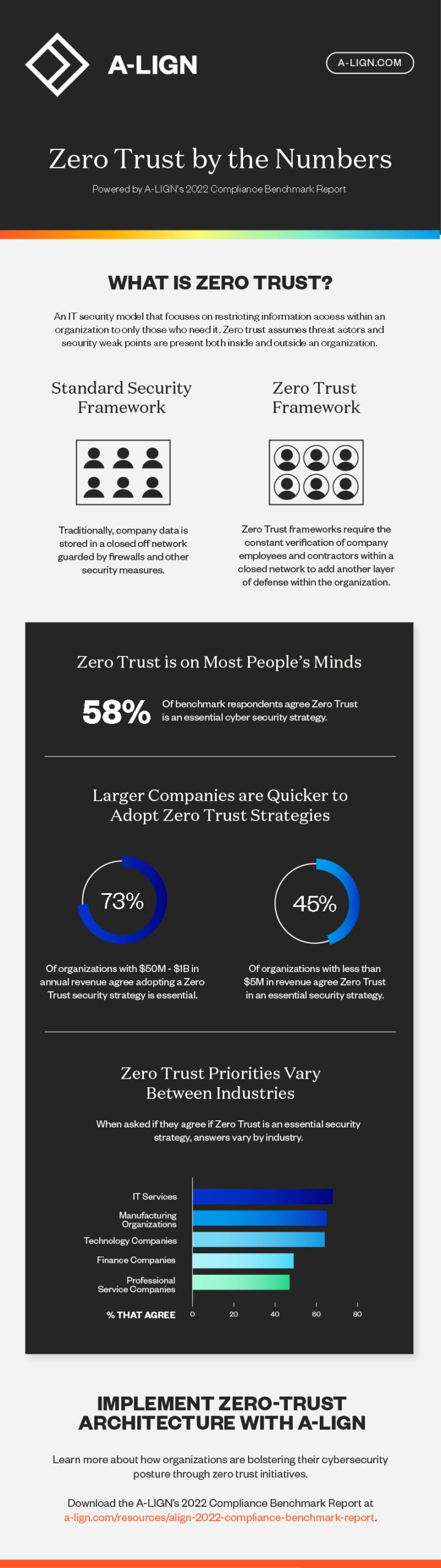
To learn more about strategically implementing a zero-trust architecture within your organization, complete our form below and one of our trusted experts will reach out directly.