What Is the Difference Between a Vulnerability Scan and a Penetration Test?
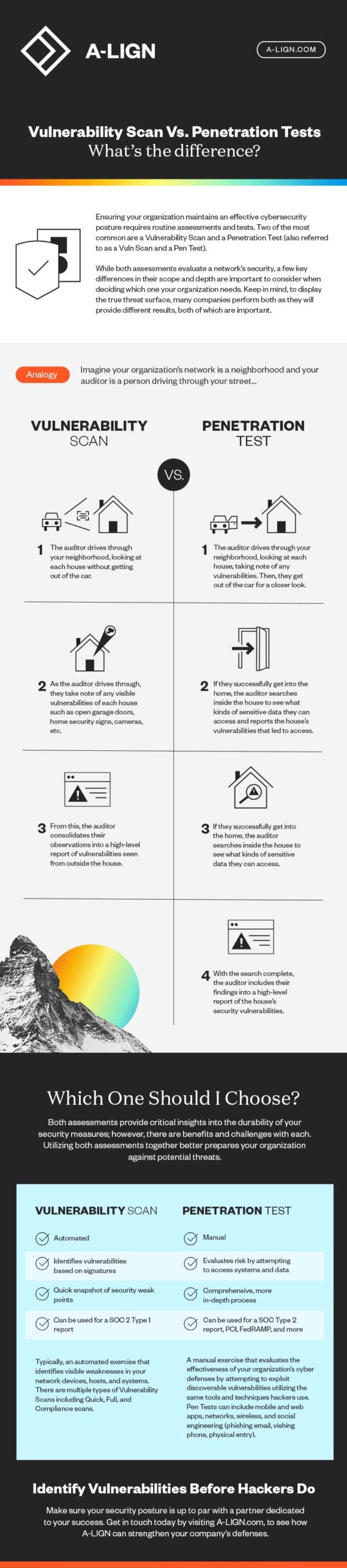
Organizations understand the importance of having a strong security posture. From meeting various compliance and industry regulations to maintaining customer trust, organizations cannot risk overlooking any weak spots in their network. Yet many organizations often leverage a single security assessment and consider their due diligence complete. This approach, however, only tells part of the story. To create a truly strong security posture, organizations should explore both a vulnerability scan and a penetration test and see how they can complement one another.
What is a vulnerability scan?
A vulnerability scan checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. At the completion of the scan, the organization obtains a report that outlines their risk exposure.
What is a penetration test?
A penetration test (also referred to as a “pen test”) takes a preventative approach to security. A pen test is a more intentional and manual exercise designed with the goal of “penetrating” an organization’s network and systems to gain access to data. Basically, it’s a simulation that leverages a variety of tools and tactics to map out vulnerabilities.
Better together: Combining a vulnerability scan and penetration test
When a vulnerability scan is paired with a pen test, it can provide organizations with deeper insights into where and how to enhance their security posture. A penetration test may not list or confirm every vulnerability in the environment, but a vulnerability scan will scan all systems looking for signatures that match known vulnerabilities that may (or may not) be able to be penetrated. This approach enables an organization to enhance its security posture with a more complete picture of the threat surface.
Ready to schedule your vulnerability scan and pen test?
Pen tests are an important part of any risk management strategy. Now that work-from-anywhere culture is here to stay, there’s no better time to schedule a pen test to ensure your organization is protected against the latest threats.
At A-LIGN, our OSEE, OSCE, and OSCP-certified pen testers emulate the techniques of actual attackers by creating scenarios and strategies unique to your organization in an attempt to breach your networks and applications, with the ultimate goal of helping you improve your security posture. Reach out now to get started on your compliance journey.
