Why Are Penetration Tests Important?
How do you measure the effectiveness of your cybersecurity program? Ask this question of a dozen CISOs and you’ll likely get twelve different answers. That’s because there’s no one-size-fits-all approach to measuring security but a penetration test plays into the most effective cybersecurity strategies.
While there may not be a single “right” way of measuring your cybersecurity program, one thing is for certain: creating and maintaining a strong cybersecurity posture requires a tactical and proactive mindset. And one of the best ways to stay a step ahead of clever threat actors is to simulate realistic network attacks with a penetration test, frequently referred to as a “pen test.”
This method of ethical hacking is designed to test the information security safeguards in place at your organization. By doing so, you gain insight into existing vulnerabilities or gaps in your cybersecurity program that could lead to a data breach or security incident.
Why pen tests?
Cybersecurity breaches can disrupt operations, damage reputations, and lead to costly fines or lawsuits. Penetration testing serves as a preventative measure, helping organizations identify and address potential weaknesses.
We recommend that any organization that has a web application conduct regulation penetration tests. Running an application where customers are inputting data and not testing it is irresponsible. Here’s why pen tests are vital:
Identifying vulnerabilities before attackers do
Hackers are constantly developing new methods and tools to exploit weaknesses in networks, applications, and systems. Regular penetration tests expose vulnerabilities such as misconfigured firewalls, outdated software, or weak authentication protocols, allowing you to fix them before attackers can take advantage. By conducting penetration tests, your organization can reduce its attack surface and make fully informed decisions about improving security.
Protecting sensitive data and maintaining customer trust
Data breaches don’t just compromise internal operations—they impact customers too. When personal data is exposed, it erodes customer trust and loyalty. High-profile breaches, like those targeting major retailers or financial institutions, often lead to public fallout and declining customer confidence.
Pen testing ensures weaknesses in systems handling sensitive information, such as credit card numbers, health records, or proprietary data, are proactively identified and mitigated. This practice also reinforces your reputation as a business dedicated to security and professionalism.
Meeting compliance requirements and avoiding penalties
Regulations like GDPR, HIPAA, PCI DSS, and ISO 27001 often require companies to conduct regular penetration tests. Compliance ensures your business adheres to stringent security requirements and avoids costly penalties associated with data breaches or non-compliance.
For example:
- GDPR fines can reach €20 million or 4% of annual turnover, whichever is higher.
- Companies out of compliance with PCI DSS could face fines between $5,000 and $100,000 per month.
Regular penetration testing not only satisfies regulatory obligations but also demonstrates security due diligence to customers, partners, and investors.
Improving incident response capabilities
Penetration tests don’t just uncover vulnerabilities—they refine your ability to respond to potential attacks. They can simulate real threats to evaluate how your incident response team performs under pressure. By identifying weaknesses in your response plans, you can fine-tune and strengthen them to minimize damage in the future.
Bad actors are growing in complexity
Attackers are growing in size and complexity, making it all the more likely that they could target your company. Consider just a few high-profile data breaches from 2024:
- Change Healthcare experienced a ransomware attack in February 2024 in which it allegedly paid attackers a $22 million ransom to gain access to its systems, which were restored over a month later. Attackers targeted a Citrix remote access portal that did not require multi-factor authentication. The attack resulted in major pharmacy chains and other healthcare organizations facing disruptions for multiple days when it came to billing, prescribing medication, and health claims.
- In May 2024, Ticketmaster disclosed a cyberattack that exposed customer information, payment details, and personal data to hackers. Attackers listed a batch of 560 million Ticketmaster customers for sale on the dark web for $500,000 one week after the attack.
- The medical insurance information of 954,000 people was exposed by a data breach at Young Consulting in April 2024. The software company experienced technical difficulties within its computer environment and later determined that an unauthorized actor gained access to its network for three days leading up to those difficulties and downloaded copies of files.
These breaches expose customer data, shut down internal systems, and cause loss of trust among customers.
Why should organizations invest in a pen test?
A well-executed pen test offers your team insights into weak and exploitable points within the organization, and how to remediate them to increase your security posture.
- Benefits of conducting regular pen tests include:
- Assessing your organization’s information security of technologies, systems and people (social engineering)
- Identifying vulnerabilities in your security posture before attackers do
- Helping your organization achieve and maintain compliance
- Giving your team insight into your organization’s true threat surface from an external hacker’s or rogue insider’s perspective
While certain compliance frameworks require an organization to conduct a pen test once a year, the reality is that new attack vectors pop up constantly. That’s why an annual pen test likely isn’t enough to ensure your organization is well protected against the latest threats. Additional assessments, like a ransomware preparedness assessment, continuous scanning or vulnerability assessments are often important ways to continue to stress test your organization’s cyber resilience.
Ransomware preparedness assessment
Ransomware attacks are more prevalent than ever, with bad actors demanding large sums of money to release their hold on organizations and their data. At A-LIGN, we offer a ransomware preparedness assessment, which includes a comprehensive review of your infrastructure and processes, real-world ransomware simulations, and a full pen test, all with the goal of reducing the likelihood that your organization will fall victim to this type of attack.
Vulnerability assessment
Every organization today, regardless of size or industry, is adding new endpoints and constantly provisioning new software. This emphasizes why making scheduled vulnerability scans an important part of every security program. Our vulnerability assessment scans map out threat surfaces and known weaknesses for your team before malicious actors can take advantage of them.
Worth noting is that a vulnerability assessment is a means of detection; it tests an organization’s network and systems for known vulnerabilities. When paired with a pen test—which takes a preventative approach—you increase your visibility into weak spots and gaps across your network. This enables organizations to take a more proactive approach to enhancing their security posture.
What type of pen test is right for my organization?
A comprehensive pen test should examine all relevant facets of your cybersecurity controls. At A-LIGN, there are six different components of our pen tests:
Network layer testing: We perform network layer testing using a comprehensive (host-by-host or port-by-port) or targeted (goal-driven) approach.
Web application testing: Our team profiles and targets weaknesses that are inherent in the development of proprietary and custom web applications. Our web application testing includes an in-depth manual review of vulnerabilities designed in the OWASP Top 10 and the SANS Top 20.
Mobile application testing: We use tooling and years of professional experience to capture traffic, analyze your application, and exploit weaknesses and misconfigurations often found in iOS and Android. For this we utilize the OWASP Top 10 for Mobile.
Wireless network testing: We perform a detailed analysis of your organization’s wireless infrastructure using innovative tooling and proprietary tactics.
Email phishing, phone vishing, and facility penetration testing: Whether you want to assess how susceptible your organization is to advanced entry tactics or want to evaluate employee security awareness, we’ll create a customized assessment to meet your testing goals.
Ready to schedule your pen test?
Pen tests are an important part of any risk management strategy. As attackers grow in size and complexity, there’s no better time to schedule a pen test to ensure your organization is protected against the latest threats.
A-LIGN’s OSEE, OSCE, and OSCP-certified pen testers emulate the techniques of actual attackers. We will create scenarios and strategies unique to your organization in an attempt to breach your networks and applications, with the ultimate goal of helping you improve your security posture. Ready to get started? Contact us today. your organization in an attempt to breach your networks and applications, with the ultimate goal of helping you improve your security posture.
CISO insights: The strategic role of the CISO
The role of the Chief Information Security Officer (CISO) continues to evolve beyond traditional security functions. Today’s CISO is a strategic business partner, balancing risk management with innovation enablement. From AI integration to shifting regulatory landscapes and sophisticated threat actors, the security ecosystem is more complex than ever.
In this article, Carbyne’s CISO, Paresh Patel, shares his perspective on current trends, compliance priorities, and strategic insights that every CISO should have on their radar this year.
Top security trends for CISOs to watch
AI is a challenge and a tool in cybersecurity, changing how leaders protect their systems. With more focus on identity-based security and higher accountability at the top, leaders need to adapt quickly, stay strong, and build trust. This highlights the need for proactive strategies and new technologies to keep up with the constantly shifting landscape.
AI: Friend and foe
AI is no longer a future concern; it’s a current reality. Depending on who is using it, AI can be an asset or a threat. Threat actors use generative AI to craft convincing phishing campaigns, automate vulnerability discoveries, and scale social engineering. This poses new challenges to organizations that need to stay two steps ahead.
At the same time, defensive AI is maturing. Behavior-based threat detection, autonomous response systems, and advanced anomaly detection are transforming how security teams operate, providing new ways to monitor and respond to threats.
The rise of identity-first security
As remote work and cloud services continue to expand, identity has effectively replaced traditional network perimeters as the frontline of cybersecurity. With compromised credentials responsible for more than half of data breaches, cybercriminals increasingly use sophisticated methods to exploit identity vulnerabilities.
These developments require CISOs to implement vigilant defenses and advanced strategies to protect against evolving threats and instill confidence in clients, partners, board members, and other key stakeholders.
Board-level accountability and cyber resilience
Following major incidents in 2023 and 2024, and in addition to increased regulatory scrutiny, boards are more cyber-aware than ever— and demand answers on how CISOs will keep organizations secure.
Cyber resilience, not just cybersecurity, is the new boardroom metric. CISOs need to come to the table with accountability and proactive planning to get buy-in and earn trust from board members. For example, CISOs need to communicate their security plans and know how fast their business can recover from a cyber event and what the short-term and long-term business impact could be.
Compliance and regulatory priorities for CISOs
Organizations face growing pressures to meet complex compliance requirements and protect data. From regional data sovereignty laws to SEC cybersecurity disclosure rules and emerging regulations like the EU AI Act, businesses must tackle evolving accountability and risk management standards. These shifts emphasize the need for proactive governance and a firm grasp of regulatory frameworks across jurisdictions.
Global data sovereignty and localization
As countries continue to tighten data protection laws, CISOs must navigate a patchwork of regulations that impact where and how their organizations store and process data. The EU’s NIS2 Directive, China’s PIPL, and India’s DPDP Act are just a few examples of regional frameworks shaping compliance strategies.
SEC cyber disclosure requirements
In the U.S., the SEC now requires public companies to disclose material cybersecurity incidents and outline governance practices around cyber risk. These mandates emphasize the need for strong incident detection, reporting mechanisms, and board engagement.
AI and emerging regulations
The EU AI Act, expected to go into effect soon, will classify AI systems based on risk and require transparency, accountability, and oversight. Even companies outside the EU may be impacted if they serve European customers.
Mitigating risk while embracing AI
AI holds massive potential to streamline operations, improve customer experience, and enhance decision-making. But without guardrails, it introduces significant risks, including data leakage, model bias, and shadow AI initiatives operating outside IT’s control.
Here’s how to adopt a secure and responsible AI approach:
Establish an AI governance framework
Create a cross-functional AI governance board that includes representatives from security, data science, legal, and compliance. This group should be responsible for reviewing high-risk AI applications, monitoring for drift or abuse, and enforcing ethical standards.
Secure AI development and deployment
If your organization is building AI models, apply the same level of security scrutiny as you would for software development. Threat modeling, secure coding practices, and continuous monitoring must be part of the pipeline.
Educate and empower your workforce
Security awareness programs should now include AI-specific modules covering risks like deepfakes, synthetic phishing, and prompt engineering attacks. At the same time, encourage innovation by providing secure AI tools and platforms.
The CISO is not just the guardian of data and infrastructure but a business enabler, digital ethicist, and risk translator. As AI transforms industries and regulatory pressures mount, security leaders must adopt a proactive, adaptable mindset.
Your security strategy should address today’s threats and empower your organization to explore tomorrow’s opportunities securely, responsibly, and resiliently.
About Paresh Patel
Paresh Patel is a seasoned cybersecurity and technology executive with over 20 years of progressive experience in leading security services, managing complex IT projects, and building global compliance programs. As CISO and CIO at Carbyne, he drives enterprise-wide information security and regulatory strategies to safeguard next-generation emergency communications.
With deep expertise in cybersecurity architecture, risk assessment, policy and procedure development, and security training, Paresh has shaped security postures across various industries. He is highly proficient in navigating complex regulatory landscapes, including ISO 27001/27701, NIST, SOC, HIPAA, PCI-DSS, FedRAMP, IRAP, HITRUST, FFIEC, CJIS, and GDPR.
Paresh’s work spans the development of secure frameworks, business continuity planning, and disaster recovery, alongside information systems management. He is known for his solutions-oriented approach, strong leadership, and ability to cultivate lasting partnerships while aligning security strategy with business innovation.
About Carbyne
Carbyne (Headquartered in New York, NY) is a leading global provider of cloud-native, mission-critical contact center solutions. Carbyne is one of the largest rich-data providers for emergency response centers, delivering over 250M data points annually in a unified platform. Our technologies enable emergency contact centers and select enterprises to connect with callers as well as connected devices via highly secure communication channels without needing to download a consumer app. With a mission to redefine emergency collaboration and connect the dots between people, enterprises, and governments, Carbyne provides a unified cloud-native solution that provides live, actionable data that can lead to more efficient and transparent operations and ultimately improve the entire dispatch function. With Carbyne, every person counts. Learn more at carbyne.com.
A-LIGN Expands Panama Office to Support Team, Operational Growth
PANAMA CITY– April 7, 2025 – A-LIGN, the leading provider in cybersecurity compliance, is excited to announce the expansion of its Panama office, located in the renowned neighborhood of Costa Del Este. This development reflects A-LIGN’s rapid growth, commitment to the region, and continued investment in its people.
The expanded office features 370 square meters of modern workspace and enhanced accommodations for A-LIGN’s growing team. With state-of-the-art facilities and a stunning ocean view, the new layout includes specialty and common areas designed to foster collaboration and innovation.
“This expansion marks a significant milestone in our continued growth and commitment to creating a workplace that enables teams to connect, collaborate and thrive,” said Jelena Brown, Chief Human Resources Officer. “We’re excited to provide a space that not only supports operational needs but also mirrors the company’s employee-focused culture.”
The expansion coincides with growth on the Panama team, with 11 new campus hires joining the team today. The group’s headcount now sits at 71 employees, a dramatic increase from when the office opened in 2021 with 12 team members. The new office space will also support A-LIGN’s growing number of clients in Latin America, which has doubled from 2024 to 2025.
A-LIGN’s Panama office has expanded across all teams at A-LIGN. The team originally supported Service Delivery’s SOC practice. Now, in addition to supporting multiple Service Delivery practices, the Panama office plays a vital role in supporting Operations, IT and Enginering. The team will continue to grow and invest in its people in 2025. To learn more, visit a-lign.com/careers.
For more information about A-LIGN, visit www.a-lign.com.
About A-LIGN
A-LIGN is the leading provider of high-quality, efficient cybersecurity compliance programs. Combining experienced auditors and audit management technology, A-LIGN provides the widest breadth and depth of services including SOC 2, ISO 27001, HITRUST, FedRAMP, and PCI. A-LIGN is the number one issuer of SOC 2 and a leading HITRUST and FedRAMP assessor. To learn more, visit a-lign.com.
Penetration Testing’s Crucial Role in SOC 2 Audits for Security Assessment & Risk Mitigation
Combining a penetration test with a SOC 2 audit is a powerful approach to strengthening an organization’s security measures. While a SOC 2 audit evaluates the controls and processes that safeguard customer data, a penetration test takes this evaluation a step further by actively identifying vulnerabilities and simulating real-world attack scenarios. Together, these methods provide a comprehensive view of security, ensuring compliance with the Trust Services Criteria (TSC) and highlighting areas for continuous improvement. Read on to learn about the benefits of this approach.
Comprehensive security assessment
A SOC 2 audit provides a structured evaluation of organizational controls that align with TSC requirements; however, it is limited to a top-down review of documentation and processes. A penetration test, on the other hand, complements this by simulating real-world cyberattacks. This hands-on approach identifies vulnerabilities and weaknesses that may not be apparent through standard audit procedures.
Penetration testing offers organizations a deeper understanding of where their security measures stand by uncovering gaps in safeguards like access controls, firewalls, or endpoint protection systems. For example, a misconfigured server might evade detection during a traditional SOC 2 review but could be identified during a penetration test. This dynamic assessment provides actionable insights, empowering organizations to address potential security risks before malicious actors exploit them.
Validation of security controls
Security controls are only as effective as their ability to withstand real-world threats. A penetration test provides a robust way to validate these controls by simulating attack scenarios against your organization’s systems. This active evaluation demonstrates how well your security measures perform under stress, offering tangible evidence of their effectiveness.
For instance, a penetration test might focus on evaluating how secure your network is against unauthorized access. If vulnerabilities are found during this test, it highlights areas where security controls need to be strengthened. Validation of controls also reassures customers, stakeholders, and partners that your organization is committed to protecting sensitive data and maintaining the highest security standards.
Additionally, this validation process ensures compliance with SOC 2’s TSC, reinforcing that your controls are not just well-documented but also operationally effective against potential security breaches.
Risk mitigation
Every organization faces the risk of cyberattacks and data breaches, but proactive measures like penetration testing can significantly reduce these risks. Unlike audits, which assess an organization’s adherence to established standards, penetration tests uncover specific vulnerabilities and allow organizations to prioritize risk remediation based on the likelihood and severity of potential exploits.
For example, a penetration test might reveal that a web application is vulnerable to SQL injection attacks. Identifying this issue early enables your organization to correct it, thereby preventing an attacker from exploiting it to access sensitive data. Similarly, if a test uncovers inadequate encryption settings, immediate adjustments can be made to neutralize the threat.
By addressing these vulnerabilities, organizations can reduce the likelihood of costly incidents that could disrupt operations, damage customer trust, or lead to regulatory penalties. Risk mitigation through penetration testing also demonstrates a forward-thinking approach to security, showcasing your organization’s commitment to staying ahead of cyber threats.
Compliance with Trust Services Criteria (TSC)
Several of SOC 2’s Trust Services Criteria align closely with outcomes that can be achieved through penetration testing. Performing a penetration test helps organizations meet these criteria by providing real-world evidence of their security measures. Here’s how it aligns with specific TSC components:
- Security: Penetration tests assess critical areas such as access controls, network protections, and defenses against malware, addressing the fundamental security pillar of SOC 2.
- Availability: By evaluating the resilience and availability of systems, penetration tests identify potential weaknesses that could lead to downtime or service disruptions.
- Confidentiality: Tests scrutinize data protection mechanisms, identifying vulnerabilities that could compromise the confidentiality of sensitive information.
- Processing Integrity: Penetration tests uncover issues that could impact the accuracy, completeness, or timeliness of data processing, ensuring operational integrity.
- Privacy: The assessments also reinforce privacy controls, ensuring personal information is protected from unauthorized access or exposure.
Achieving compliance with these criteria not only fulfills audit requirements but also signals to customers and stakeholders that your organization is committed to safeguarding data and delivering quality services.
Driving continuous improvement
Penetration testing is not a one-time activity—it plays a pivotal role in fostering a culture of continuous improvement within your organization. The insights gleaned from penetration testing reports go beyond identifying vulnerabilities; they also inform longer-term strategies for enhancing your security posture.
For instance, a recurring penetration test might show patterns in vulnerabilities, such as repeated weaknesses in web-facing applications. This information allows your organization to implement targeted training for developers or adjust coding best practices to prevent similar issues in the future. Penetration tests also encourage organizations to stay updated on evolving threats, ensuring security measures remain relevant in the face of changing cyber risks.
By making penetration testing a regular part of your security strategy, your organization can proactively adapt to new challenges, maintain compliance, and continuously build trust with customers and partners.
The performance-driven advantage
The integration of penetration testing with SOC 2 audits offers a performance-driven approach to enterprise security. It ensures that your controls are not just compliant on paper but effective against real-world threats. Whether it’s strengthening defenses, mitigating risk, or meeting regulatory expectations, this combination empowers organizations to optimize their security strategies and protect their most valuable assets.
If your organization is considering a SOC 2 audit, incorporating penetration testing into the process is no longer optional—it is a necessity. Together, these tools provide a comprehensive assessment of your organization’s security measures, helping you stay ahead of threats, achieve compliance, and continuously improve. Contact A-LIGN today to get started.
What Is the Difference Between a Vulnerability Scan and a Penetration Test?
Organizations understand the importance of having a strong security posture. From meeting various compliance and industry regulations to maintaining customer trust, organizations cannot risk overlooking any weak spots in their network. Yet many organizations often leverage a single security assessment and consider their due diligence complete. This approach, however, only tells part of the story. To create a truly strong security posture, organizations should explore both a vulnerability scan and a penetration test and see how they can complement one another.
What is a vulnerability scan?
A vulnerability scan checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. At the completion of the scan, the organization obtains a report that outlines their risk exposure.
What is a penetration test?
A penetration test (also referred to as a “pen test”) takes a preventative approach to security. A pen test is a more intentional and manual exercise designed with the goal of “penetrating” an organization’s network and systems to gain access to data. Basically, it’s a simulation that leverages a variety of tools and tactics to map out vulnerabilities.
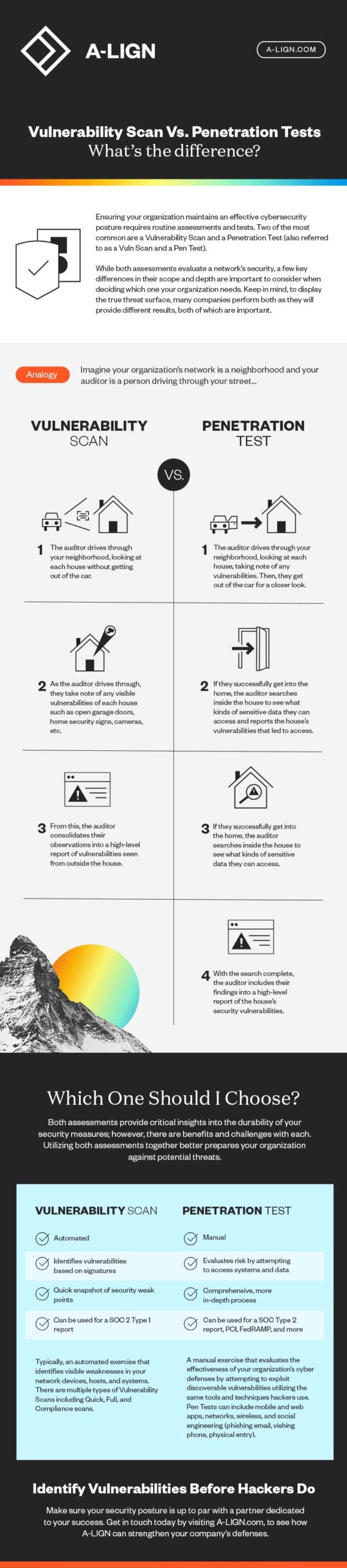
Better together: Combining a vulnerability scan and penetration test
When a vulnerability scan is paired with a pen test, it can provide organizations with deeper insights into where and how to enhance their security posture. A penetration test may not list or confirm every vulnerability in the environment, but a vulnerability scan will scan all systems looking for signatures that match known vulnerabilities that may (or may not) be able to be penetrated. This approach enables an organization to enhance its security posture with a more complete picture of the threat surface.
Ready to schedule your vulnerability scan and pen test?
Pen tests are an important part of any risk management strategy. Now that work-from-anywhere culture is here to stay, there’s no better time to schedule a pen test to ensure your organization is protected against the latest threats.
At A-LIGN, our OSEE, OSCE, and OSCP-certified pen testers emulate the techniques of actual attackers by creating scenarios and strategies unique to your organization in an attempt to breach your networks and applications, with the ultimate goal of helping you improve your security posture. Reach out now to get started on your compliance journey.
Combining Penetration Testing & ISO 27001 Audit for Enhanced Security Assessment
Performing a penetration test alongside a ISO/IEC 27001 audit is crucial as it provides a comprehensive assessment of an organization’s security measures. While an ISO 27001 audit evaluates controls and processes, a penetration test goes further by actively identifying vulnerabilities and simulating real-world attacks. This validation of security controls helps ensure their effectiveness and compliance with Trust Services Criteria (TSC) such as availability, confidentiality, processing integrity, and privacy. Additionally, a penetration test aids in mitigating risks, identifying areas for improvement, and fostering continuous enhancement of security practices.
By combining a penetration test with an ISO 27001 audit, organizations can proactively identify and address security weaknesses, protect sensitive data, and demonstrate their commitment to robust security measures. Performing a penetration test alongside an ISO 27001 audit is vital to comprehensively assess an organization’s security measures. While audits evaluate the implementation of security controls, penetration testing goes a step further by actively identifying vulnerabilities and potential risks. Combining these approaches can help organizations validate the effectiveness of their controls, demonstrate compliance with ISO 27001 requirements, and gain a more thorough understanding of their security posture. The penetration test provides valuable insights into potential weaknesses that could be exploited, allowing organizations to take deliberate measures to enhance their security defenses and minimize potential risks.
ISO 27001 & pen testing benefits
A-LIGN refers to the below list as the BIG 5 benefits of Penetration Testing alongside an ISO audit:
- Risk management: ISO 27001 requirements place a strong emphasis on risk management, requiring organizations to identify and assess risks to the confidentiality, integrity, and availability of information. Penetration testing helps organizations identify vulnerabilities and potential attack vectors that could be exploited by malicious actors. Conducting a penetration test can help proactively identify and mitigate security risks, reducing the likelihood of security incidents and their potential impact.
- Compliance: ISO 27001 is an internationally recognized standard for information security management. It provides a framework for organizations to establish, implement, maintain, and continually improve their information security management system (ISMS). Penetration testing is one of the key controls recommended by ISO 27001, specifically in Annex A, as a means to verify the effectiveness of security controls and assess the resilience of the system against real-world attacks. Performing penetration tests helps demonstrate compliance with ISO 27001 requirements and provides assurance to stakeholders, clients, and regulatory bodies.
- Validation of security controls: Penetration testing validates the effectiveness of an organization’s security controls, including technical controls (e.g., firewalls, intrusion detection systems) and procedural controls (e.g., access controls, incident response processes). It helps identify weaknesses or gaps in security measures, enabling organizations to make informed decisions about improving their security posture and implementing necessary safeguards.
- Incident response preparedness: Penetration testing simulates real-world attacks, allowing organizations to assess their incident response capabilities. By testing detection and response processes, companies can identify areas for improvement and refine their incident response plans. This helps enhance the organization’s ability to detect, respond to, and recover from security incidents effectively, minimizing potential damages.
- Continuous improvement: ISO 27001 promotes a culture of continual improvement. Penetration testing provides valuable insights into the effectiveness of existing security measures and helps identify areas for enhancement. By addressing vulnerabilities identified during penetration testing, organizations can continually improve their security controls and reduce the overall risk exposure.
It’s important to note that while a penetration test can contribute to satisfying certain aspects of risk management, internal audits, corrective and preventive actions, and continuous improvement, it is just one component of an overall security management program. Other items listed, such as documentation control, management commitment, training, competence, and customer focus are typically not directly satisfied by a penetration test but are important considerations for achieving ISO certifications.
Get started by downloading our ISO 27001 checklist.
What Is a Vulnerability Scan?
Organizations understand the importance of having a strong security posture. From meeting various compliance and industry regulations to maintaining customer trust, organizations cannot risk overlooking any weak spots in their network. Yet many organizations often leverage a single security assessment and consider their due diligence complete. This approach, however, only tells part of the story. To create a truly strong security posture, organizations should explore various cybersecurity assessments, and see how they can complement a vulnerability scan.
Let’s dig into what a vulnerability scan is and how it compares to — and works with — additional cybersecurity assessments.
What is the purpose of a vulnerability scan?
A vulnerability assessment checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. At the completion of the scan, the organization obtains a report that outlines their risk exposure.
There are two approaches to vulnerability scanning: authenticated and unauthenticated. An unauthenticated method scans the organization’s network and systems in a manner similar to a threat actor; the scan is designed to look for vulnerabilities a threat actor could exploit without trusted access to the network (e.g., logging in).
An authenticated method utilizes authentication to scan the organization’s network and systems typically by providing credentials with certain permissions (limited, admin, etc.). This offers insights into where vulnerabilities exist that could be exploited by a trusted user (insider threats) or a threat actor who gained access as a trusted user.
Any organization that has login credentials (read: most common), should include both an authenticated and unauthenticated scan to more accurately reveal both sides of the threat surface. Some vulnerabilities may only be displayed after passing through user authentication, and vulnerabilities can differ based on permissions level. To that point, organizations should include various levels of authenticated scans using accounts with various privilege levels.
What types of vulnerability scans exist?
Though vulnerability scans have two methods, the type of scans that exist typically fall into one of three categories:
- Full scan – As the name implies, a full scan is a thorough vulnerability scan that leverages its database of known vulnerabilities to look for any existing vulnerabilities across an organization’s network and systems. This can also be referred to as a “deep scan.”
- Quick scan – Also known as a “discovery scan” or a “stealth scan,” this type of vulnerability scan is meant to elevate awareness of the type of vulnerabilities that could be possible based on the network devices and system applications that exist.
- Compliance scan – This type of vulnerability scan is leveraged primarily as a means to audit an organization’s security as it relates to compliance regulations.
Different applications and programs that perform a vulnerability scan have different modes, some deeper than others. Worth noting is that when selecting your vulnerability scanning tool, know what you intend to use it for. Some scanners may perform different checks or may not offer some of these options and instead only scan the common ports.
The benefits and challenges of a vulnerability scan
Vulnerability scans offer organizations a number of unique benefits. For example, a vulnerability scan can be run as frequently, or as infrequently, as an organization deems necessary. Though many organizations tend to lean towards a quarterly approach, vulnerability scans can be set to run monthly, sometimes even weekly, depending on an organization’s needs.
And, because they are automated scans, a vulnerability scan can be highly targeted to detect any known vulnerabilities on a range of network devices, such as firewalls, routers, and services, or at an application level. As a result, organizations can more effectively identify and remediate any potential issues associated with a vulnerability faster across the network devices and applications.
Though vulnerability scans paint a solid picture of where known vulnerabilities exist, the picture is, realistically, out of focus. This is because vulnerability scans are designed to detect known vulnerabilities only. Some scan reports do offer guidance on how to remediate the vulnerabilities detected, but it requires a manual check of each vulnerability uncovered to determine validity and prioritize which items should be addressed first.
To that point, a vulnerability scan can generate false positives; some of the results produced may not result in a hack or “penetration” by a threat actor.
Additionally, because vulnerability scans are designed to detect known vulnerabilities only, a vulnerability scan cannot detect zero-day exploits. This means that though vulnerability scans are a great detection tool, they alone cannot provide organizations with enough insights to confidently build a strong security posture.
The challenges associated with vulnerability scans can often lead to a misconception among organizations that a vulnerability scan and a penetration test can be interchangeable. But this isn’t the case. Vulnerability scans and penetration tests take two completely different approaches for displaying attack surface or threat surface and work well together to provide a complete overview.
Penetration test vs. vulnerability scan: What’s the difference?
As we’ve discussed, a vulnerability scan serves as a means of detection, testing an organization’s network and systems for known vulnerabilities. Because it’s automated, it can be highly targeted to look for known vulnerabilities within specific network devices or applications, but the final output requires a manual review to determine which vulnerabilities are valid and which ones take priority to remediate.
A penetration test, however, takes a preventative approach to security. A penetration test (also referred to as a “pen test”) is a more intentional and manual exercise designed with the goal of “penetrating” an organization’s network and systems to gain access to data (e.g., financial records, personally identifiable information [PII], intellectual property). Basically, it’s a simulation that leverages a variety of tools and tactics to map out vulnerabilities. The penetration tester (frequently a security professional) will look to exploit these vulnerabilities in a manner that emulates the behavior of a threat actor. The real purpose of a pen test is to evaluate the risk associated with various vulnerabilities that may be exploitable, resulting in unauthorized access into systems and data..
Similar to vulnerability scans, there are benefits and challenges associated with a pen test. A benefit, for example, is that a pen test is a much more detailed process that provides a more accurate evaluation of an organization’s true risk profile. However, one of the challenges of a pen test is that it will not confirm every vulnerability in an environment.
Clearly, there are some great benefits—and challenges—associated with using a single security assessment. But what if they were combined?
When a vulnerability scan is paired with a pen test, it can provide organizations with deeper insights into where and how to enhance their security posture. As we previously discussed, a penetration test may not list or confirm every vulnerability in the environment, but a vulnerability scan will scan all systems looking for signatures that match known vulnerabilities that may (or may not) be able to be penetrated. This approach enables an organization to enhance its security posture with a more complete picture of the threat surface.
How A-LIGN can help
The best way to know where your organization’s greatest vulnerabilities exist is to hack your own network. Vulnerability scans offer organizations a great option to more effectively detect known vulnerabilities across their network and systems. And, when paired with a pen test, organizations can more effectively enhance their security posture by taking a truly proactive approach to cybersecurity.
A-LIGN is a trusted partner in helping organizations more effectively assess their cybersecurity and compliance needs. Our experienced team employs automated and manual techniques to find weaknesses so you have confidence that your organization’s critical data is protected. Contact us today to learn more.
Why Penetration Testing Is the First Step to Better Prepare for Hacks
The threat landscape is in a constant state of evolution. What may have been a best practice a year ago to help protect your organization against cyber threats may quickly become outdated, no longer providing enough protection on its own.
Consider the type of threats that have impacted organizations of all sizes and across industries, including cybersecurity organizations. Okta, a SaaS-based identity and access management company, fell victim to a third party data breach through the use of compromised credentials, and Shutterfly experienced a ransomware attack. And everyone remembers Colonial Pipeline’s ransomware incident that was the result of a compromised VPN password.
But it doesn’t stop there. Organizations need to take proactive steps to prepare for any threat that could elevate their threat risk, like cyberwarfare. To create and maintain a strong cybersecurity posture, organizations should leverage various assessments to test the strength of their cybersecurity efforts. One of the most effective approaches is to start with a penetration test (pen test).
What is pen testing?
A pen test is a simulated cyber attack that aims to penetrate an organization’s network. Sometimes referred to as “ethical hacking,” a penetration test takes a preventative approach to cybersecurity, evaluating an organization’s infrastructure by utilizing the same tools and tactics threat actors use. This goal-based exercise targets their technology and system’s vulnerabilities to determine if a threat actor can exploit them to gain access.
At A-LIGN, our penetration tests include six unique components that explore every part of an organization’s technologies and network. These include:
- API testing
- Network layer testing
- Mobile application testing
- Web application testing
- Wireless network testing
- Facility penetration testing
Though a pen test is extremely effective in helping organizations enhance their cybersecurity efforts, it’s important to note that it is not a one-and-done test. Most organizations conduct pen tests annually or after a big event, like switching from an on-prem to cloud architecture, development changes or feature enhancements that may introduce new functionality, or after hearing about a noteworthy cyberattack.
Relying solely on annual pen tests, however, is bad practice. Since threats emerge and evolve every day, eternal vigilance is needed to ensure organizations don’t lull themselves into a false sense of security. Fortunately, there are options available to fill in the gaps that exist between tests.
Pen tests + vulnerability scans
To maintain an updated cybersecurity infrastructure, organizations should supplement their pen tests with a quarterly vulnerability scan.
What is a vulnerability scan?
A vulnerability scan, also referred to as a vulnerability assessment, checks an organization’s network and systems for any known vulnerabilities against a database of vulnerability information. Vulnerability scans can be automated to run quarterly, monthly, or even weekly, and can be highly targeted to detect any known vulnerabilities. This enables organizations to more effectively identify and remediate potential issues associated with a vulnerability in a timely manner.
But it’s important to note that vulnerability scans are only used for detection of existing vulnerabilities; they cannot effectively detect a zero-day exploit. Pairing a vulnerability scan with a pen test is beneficial to an organization: The combination of the two provides a holistic approach to enhancing cybersecurity.
Determine your best practice
There is no one-size-fits-all approach to cybersecurity, but there are steps every organization should take to ensure they are effectively testing their security posture on a regular basis.
Leveraging pen tests is just one part of the equation. Additional steps include:
- Developing and implementing a framework. Do your research into existing frameworks, and leverage an acceptable framework, like NIST, to establish cybersecurity controls to reduce your cybersecurity risk.
- Leaning into a zero trust architecture. Be aware of who has access to your most sensitive resources, and limit that access to only the people who need it.
- Exploring additional cybersecurity assessments. Leveraging other assessments, like a Ransomware Preparedness Assessment, can provide even greater insight into your organization’s level of preparedness for a cyberattack.
- Staying educated on the evolving threat landscape. This means knowing what threat actors will try to use to infiltrate your organization, from phishing to ransomware. (To better understand and recognize various cyber threats, download The Ultimate Cybersecurity Guide.)
It’s not if, but when
Every organization across every industry is at risk for a cybersecurity incident. Staying ahead of threat actors requires organizations to adopt a tactical approach to cybersecurity. This means knowing the infrastructure, the devices connected to the network, how they communicate, the characteristics of the organization’s data, and who has access to the data.
Gain this insight by leveraging regular pen tests and supplement them with security scans and audits, including vulnerability scans and a Ransomware Preparedness Assessment.
At A-LIGN, our OSEE, OSCE, and OSCP-certified pen testers emulate the techniques of actual attackers by creating scenarios and strategies unique to your organization so you’re well prepared to respond to any cybersecurity event. Contact us today to get started.
Earning ISO/IEC 27001 or ISO/IEC 42001 accreditation for a certification body is an impressive feat. It takes time, resources and dedication to meet a high level of quality in an organization’s information security and artificial intelligence management systems program.
However, not all accreditation bodies are created equal. If you’re committing to protecting information and taking steps to improve your cybersecurity posture, don’t you want the highest level of quality from your accreditation body as possible?
Which bodies can oversee ISO 27001 and 42001 accreditations?
There are three major certification bodies in the United States: ANAB, IAS and UAF. The two most prominent bodies for ISO management system certification are the ANSI National Accreditation Board (ANAB) and the International Accreditation Service (IAS).
ANAB was the first management systems accreditation body in the United States. It is the largest multi-disciplinary accreditation body in the western hemisphere, with more than 3,000 organizations accredited in approximately 80 countries. The organization is a non-governmental organization and subsidiary of the American National Standards Institute, a non-profit organization. ANAB accredits organizations in compliance with several ISO/IEC frameworks across industries.
When you are looking for an auditor for ISO 27001 or ISO 42001 certification, make sure you choose a certification body that is accredited by a leading accreditation body. Most auditors have the accreditation body logo on their website, but if you don’t see it – do your due diligence and ask.
Why A-LIGN trusts ANAB for ISO certification
One of A-LIGN’s core values is “do the right thing, always.” That means we do the best thing for our clients as a part of our commitment to quality and don’t shy away from hard things. When it comes to choosing accreditation bodies, that means opting for the highest-quality choice. In the U.S., the gold standard for ISO accreditation is ANAB, which is why they have been our accreditation body of choice since the beginning.
Keep reading to learn about ANAB’s commitment to quality and why they are the superior choice for ISO 27001 and ISO 42001 accreditation.
Why ANAB: Stronger global and regulatory recognition
One of the key advantages of ANAB accreditation is its global recognition within the information security industry. ANAB is a signatory of the International Accreditation Forum (IAF) and Multilateral Recognition Arrangement (MLA), which ensures that ISO 27001 certifications accredited by ANAB are recognized internationally. These memberships are critical for businesses operating across borders, as many global clients require an internationally accepted accreditation.
Why ANAB: More rigorous accreditation process for ISO 27001 and 42001
ANAB’s accreditation process for ISO certification bodies is notoriously stringent, ensuring that only the most competent, well-audited certification bodies can issue certifications.
Key aspects of ANAB’s superior accreditation process include:
- Comprehensive audits of certification bodies, including technical evaluations of their ability to assess ISMS compliance.
- Strong oversight and continuous monitoring, ensuring accredited certification bodies maintain high standards. ANAB regularly looks for quality audits that follow the standards required for certification bodies.
- Alignment with ISO/IEC 17021-1, the key standard for bodies certifying management systems, with enhanced scrutiny for information security assessments.
Industry experts believe that ANAB’s high level of scrutiny results in stronger, more reliable ISO 27001 and ISO 42001 certifications, making it the preferred accreditation body for cybersecurity and compliance-driven organizations in North America. ANAB, trusted by firms including EY and Moss Adams, is associated with ANSI, an organization with more than 100 years of standards experience, which sets the stage for higher quality accreditation processes.
Why ANAB: Market and industry preference for ANAB-accredited certifications
In the cybersecurity and information security industries, ANAB accreditation is the gold standard. Many large enterprises, government agencies, and security-conscious organizations explicitly require ANAB-accredited ISO certification from their vendors and partners because of its high standards and reputation.
Companies in sectors such as cloud computing, fintech, healthcare IT, and SaaS often prefer ANAB-accredited certifications because:
- It enhances credibility with customers who prioritize security.
- It facilitates compliance with regulatory frameworks like GDPR, HIPAA, and SOC 2.
- It ensures international recognition, allowing businesses to operate in multiple regions without accreditation-related issues.
Other accreditation bodies do not hold the same influence or trust in the cybersecurity and compliance space. ANAB accreditation is the clear choice for ISO certification in the information security industry. Its strong global recognition, regulatory trust, rigorous accreditation process, and industry preference makes ANAB the accreditation body with the highest standards.
Ready to get started on your organization’s journey to ISO 27001 or 42001? Contact us today to get started with an ANAB-accredited certification body, A-LIGN.