A SOC 2 in 14 days? We’ve completed thousands of them and we can say with authority that this is misleading. As auditors, we believe in accuracy, so we wanted to share what it really takes to complete a SOC 2 and how to get it done as quickly as possible.
The other day I got a call from a fast-growing startup company in the data analytics space asking if we could do a SOC 2 in two weeks “like other companies do.” This isn’t the first time I’ve received this question – in fact, lately, it’s coming up more and more. The conversation that ensued went something like this…
Me: Two weeks? What’s driving that timeline?
Client: I see ads all the time about getting a SOC audit in 14 days. Are you doing that?
Me: Ahh, I’ve seen those too. I’m afraid the reality is a bit more complicated.
Client: Isn’t that the whole point of SOC 2 automation software – simplifying it?
Me: (shaking head) Ok, let me explain…
Setting the Record Straight: SOC 2 Audits Take More Than 14 Days
Here’s the thing. We’ve performed thousands of SOC 2 audits. In fact, A-LIGN is the top issuer of SOC 2 reports in the world. We’ve produced reports for companies of all shapes and sizes, across all industries and around the globe. We know the ins and outs of the process – where companies struggle, where they trip up, and where the opportunities are to move faster.
So, we can say this with a reasonable degree of authority: A SOC 2 can’t be completed in 14 days without any preparation.
Only Part of Your Audit Can Be Done in 14 Days
To help illustrate why – and where the confusion is likely coming from – here’s a little diagram:
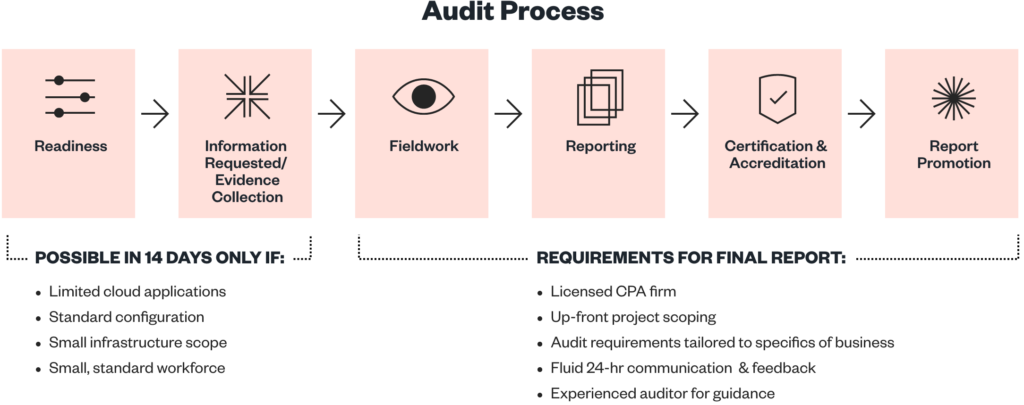
As this picture shows – when you see something that says, “14 days to SOC 2,” it’s actually only referring to the first part of the process. They aren’t talking about your completed SOC 2 report, which is your ultimate goal. The so-called “14-Day SOC 2” is a way of saying that, under certain circumstances, an automated system can get you a bunch of data that’s required to begin your audit in as little as 14 days. You won’t get a final report in that timeframe – you’ll only set the stage to get it produced.
Furthermore, that initial portion of your assessment can only be done if your environment meets a specific set of criteria. For example:
- You may need to be running your entire business from a limited set of cloud apps, such as AWS, Jira, GitHub, and a few others
- Those systems and the rest of your environment may need to be configured in a standard way
- Your infrastructure footprint probably needs to be small, simple, and consistent
- Your company probably can’t be too big – around 50 employees or under – and you’ll likely need a relatively standardized workforce in terms of roles and functions
The minute you start to introduce complexity at your company – in systems, processes, configurations, or your workforce – that’s when you’re going to see your SOC 2 take more time. Why? Because ultimately your auditor’s objective is to assess your cybersecurity practices, and the more complex your organization is, the more complex those practices will naturally be.
A more appropriate ad would read “14 days to gather information for your SOC 2” – or something similar. That’s not as catchy – but it is more accurate, and as auditors, we care deeply about accuracy.
Understand the Full Scope of Your SOC 2 with These 10 Questions
Alright, you’ve made it this far, and perhaps you are thinking that 14 days even to get ready for a SOC 2 sounds pretty good. And you’d be right – that would be fantastic. Just remember when something looks too good to be true, it often is. Do your due diligence by asking these questions:
1
After I’ve gotten through those 14 days, what else needs to be done – and by whom – so I can earn my final report?
2
Are there areas of my environment that can’t be instrumented or automated –– and who is responsible for populating this evidence? In particular, ask about:
- Legacy systems, data center systems, non-cloud systems
- Coverage across user workstations and mobile devices
- Differences between the health check that a tool provides and the evidence required to support it (for example, a report of where antivirus is supposed to be installed vs the actual evidence of the installation on each device)
- Observations for physical and environmental security concerns (including management of the maintenance records for applicable systems)
a. Legacy systems, data center systems, non-cloud systems
b. Coverage across user workstations and mobile devices
c. Differences between the health check that a tool provides and the evidence required to support it (for example, a report of where antivirus is supposed to be installed vs the actual evidence of the installation on each device)
d. Observations for physical and environmental security concerns (including management of the maintenance records for applicable systems)
3
For new policies that need to be developed – are templates provided enough for the context of your business? How will you customize them properly? What is the timeline required for implementation and training so I can show effectiveness against the policy control?
4
What is the process for instances when the data produced by the automation tool is not sufficient for the needs of the audit? Requirements fall through the cracks more often than you’d think, especially in more complex environments. This is commonly experienced when testing Sample Populations for Type 2 audits.
5
Who will project manage your SOC 2? When you have questions, who is available to address them? Does your software vendor know enough about SOC 2 to help in a meaningful way? What if their advice conflicts with your auditor? How quickly can you get questions answered with all those parties involved?
6
What is the process for evaluating, questioning, commenting on, and supplementing evidence when questions need to be addressed? Are those changes tracked in a software tool, or will you still need to rely on email and spreadsheets?
7
Who will my auditor be? How do I choose them and what is the transition like? Do they have a good reputation? Have they successfully published reports that stand up to demanding customers? Are they superior to the auditor used by your competitors?
8
Are there other assessments that need to be coordinated with your SOC 2, for example, penetration testing, vulnerability assessments, risk assessments, ISO 27001 certification, FedRAMP certification, etc.? Who will conduct these and how will information be shared?
9
How much evidence is needed to satisfy time-based requirements (particularly for SOC 2 Type 2 reports)?
10
Who is responsible for resolving disputes with the auditor?
Do the Right Thing, Always
One of A-LIGN’s core values is “Do the Right Thing, Always” – which is why we felt it was important to help people understand how the SOC 2 process actually works and what to expect from it, especially for those people going through it for the first time.
Our SOC 2 engagements are thoughtfully planned and professionally executed, leverage our expert auditors’ many years of experience, and include complimentary software and automation to get you through your SOC 2 as quickly and efficiently as possible.
